GOAD-Light-Part3-用户枚举
列出用户
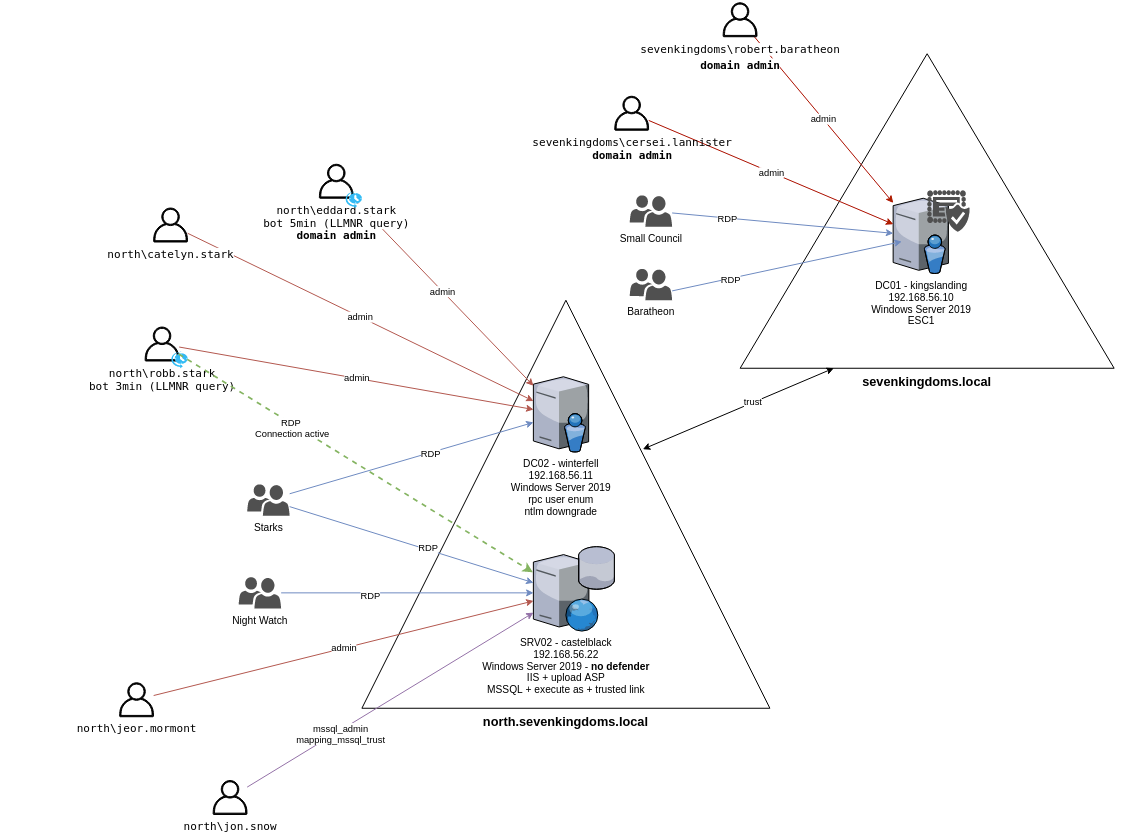
- 在上一部分,我们获得了一些用户凭据
- 当您在活动目录上获得一个帐户时,要做的第一件事总是获得完整的用户列表
- 域内的任何普通认证用户,默认都有权限读取 Active Directory 中的绝大多数信息(用户、组、计算机等)。
- 一旦你得到它,你就可以在完整的用户列表上进行密码喷洒(你经常会发现其他帐户的密码很弱,比如 username=password、SeasonYear!、SocietynameYear! 甚至 123456)
使用GetADUsers
1 | |
1 | |
使用CME
1 | |
1 | |
LDAP查询
1 | |
1 | |
通过 LDAP 查询,我们可以请求其他域的用户,因为存在信任关系。
在 sevenkingdoms.local 上
1 | |
父域用户结构
1 | |
1 | |
Kerberoasting
Kerberos协议
Kerberos是一种由MIT(麻省理工大学)提出的一种网络身份验证协议
它旨在通过使用密钥加密技术为客户端/服务器应用程序提供强身份验证
在Kerberos协议中主要是有三个角色的存在:
- 访问服务的Client(以下表述为Client 或者用户)
- 提供服务的Server(以下表述为服务)
- KDC(Key Distribution Center)密钥分发中心 kerberos 测试工具介绍
其中KDC服务默认会安装在一个域的域控中,而Client和Server为域内的用户或者是服务,如HTTP服务,SQL服务在Kerberos中Client是否有权限访问Server端的服务由KDC发放的票据来决定
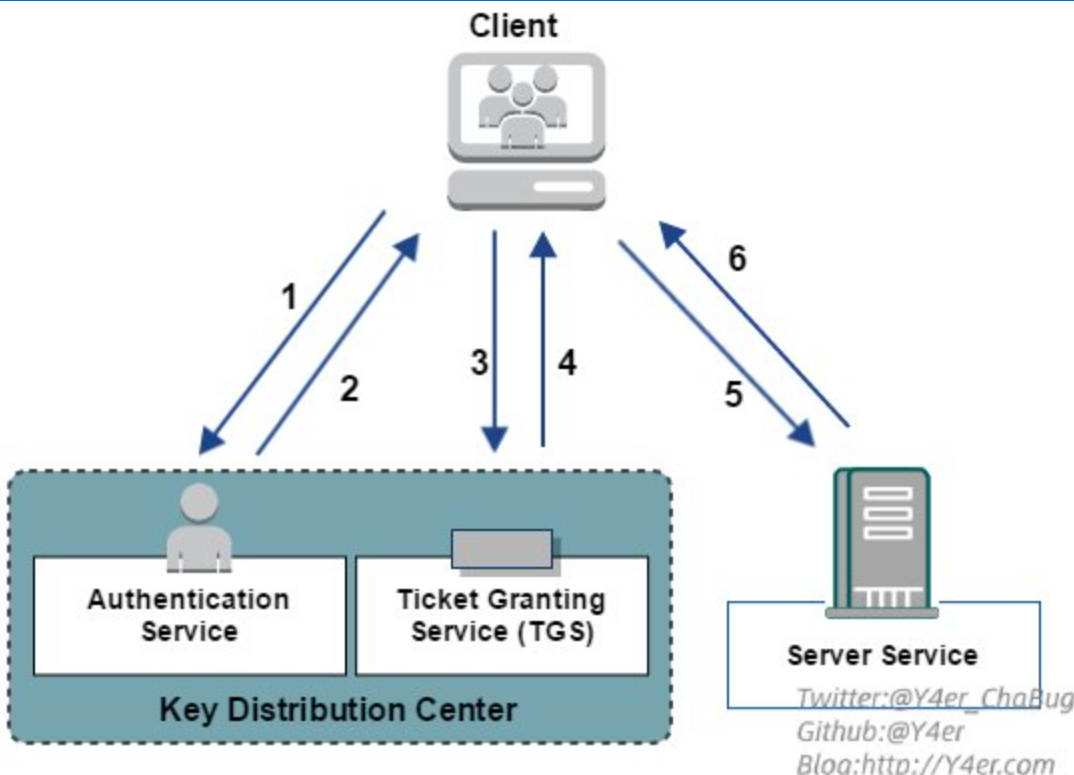
- AS_REQ: Client向KDC发起AS_REQ,请求凭据是Client hash加密的时间戳
- AS_REP: KDC使用Client hash进行解密,如果结果正确就返回用krbtgt hash加密的TGT票据,TGT里面包含PAC,PAC包含Client的sid,Client所在的组
- TGS_REQ: Client凭借TGT票据向KDC发起针对特定服务的TGS_REQ请求
- TGS_REP: KDC使用krbtgt hash进行解密,如果结果正确,就返回用服务hash 加密的TGS票据(这一步不管用户有没有访问服务的权限,只要TGT正确,就返回TGS票据)
- AP_REQ: Client拿着TGS票据去请求服务
- AP_REP: 服务使用自己的hash解密TGS票据如果解密正确,就拿着PAC去KDC那边问Client有没有访问权限,域控解密PAC获取Client的sid,以及所在的组,再根据该服务的ACL,判断Client是否有访问服务的权限
SPN
SPN简介
SPN(ServicePrincipal Names)服务主体名称,是服务实例(比如:HTTP、MSSQL、MySQL等服务)的唯一标识符 SPN是服务器上所运行服务的唯一标识,每个使用Kerberos的服务都需要一个SPN
SPN分为两种,一种注册在AD上机器帐户(Computers)下,另一种注册在域用户帐户(Users)下
当一个服务的权限为Local System或Network Service,则SPN注册在机器帐户(Computers)下
当一个服务的权限为一个域用户,则SPN注册在域用户帐户(Users)下
SPN的格式:
1 | |
- serviceclass可以理解为服务的名称,常见的有www, ldap, SMTP, DNS, HOST等
- host有两种形式,FQDN和NetBIOS名,例如server01.test.com和server01
- 如果服务运行在默认端口上,则端口号(port)可以省略
kerberoasting
通过SPN发现服务(比如MSSQL)
具有域内普通用户权限
向SPN服务进行交互,请求Kerberos票据(当用户的TGT被验证为有效时,TGS会向用户发送一张票据,该票据使用与SPN关联服务的计算机服务账号相同的NTLM Hash,比如MSSQL账户的Hash)
根据字典爆破生成Hash,去尝试打开该Kerberos票据
如果成功,则获得了MSSQL服务账户的密码
攻击者可以伪造TGS白银票据,在TGS中标识访问账号为域管理员账号 从而获取服务的域管理员访问权限
或者用于委派攻击(服务账号大多都会被设置委派,如果是非约束委派,则获取服务账号的口令后,可直接获取域管理员权限)
使用impacket
1 | |
1 | |
使用cme
1 | |
1 | |
使用john破解
1 | |
成功获取另一个用户凭据
1 | |
共享枚举
使用刚才的获得账号密码尝试,有个新的共享文件夹是可读的(在该靶场里什么都没有,但在真正的渗透中可能会经常得到有趣的信息)
1 | |
1 | |
DNS 转储
利用当前获取的域用户权限,把整个域内所有的 DNS 解析记录全部读取出来的过程。
AD 集成 DNS 允许认证用户列出区域内的所有记录。
默认情况下,Active Directory 中的任何用户都可以枚举域或林 DNS 区域中的所有 DNS 记录,类似于区域传输,此工具启用区域中所有 DNS 记录的枚举和导出,用于内部网络的侦察目的
1 | |
1 | |
1 | |
Bloodhound
参考链接
https://en.hackndo.com/bloodhound/#going-further
- Boodhound 是活动目录渗透测试的最佳工具之一,此工具将帮助您找到破解 AD 的所有路径,是您武器库中的必备工具!
- 要启动 bloodhound,您首先需要从不同的域中检索所有数据
Linux环境,直接用python脚本:
https://github.com/fox-it/BloodHound.py
Windows环境,可以用:
https://github.com/BloodHoundAD/SharpHound
RustHound支持ADCS收集:
https://github.com/OPENCYBER-FR/RustHound
安装
1 | |
收集信息
1 | |
1 | |
1 | |
1 | |
Bloodhound安装参考
https://www.cnblogs.com/yuy0ung/articles/18411240
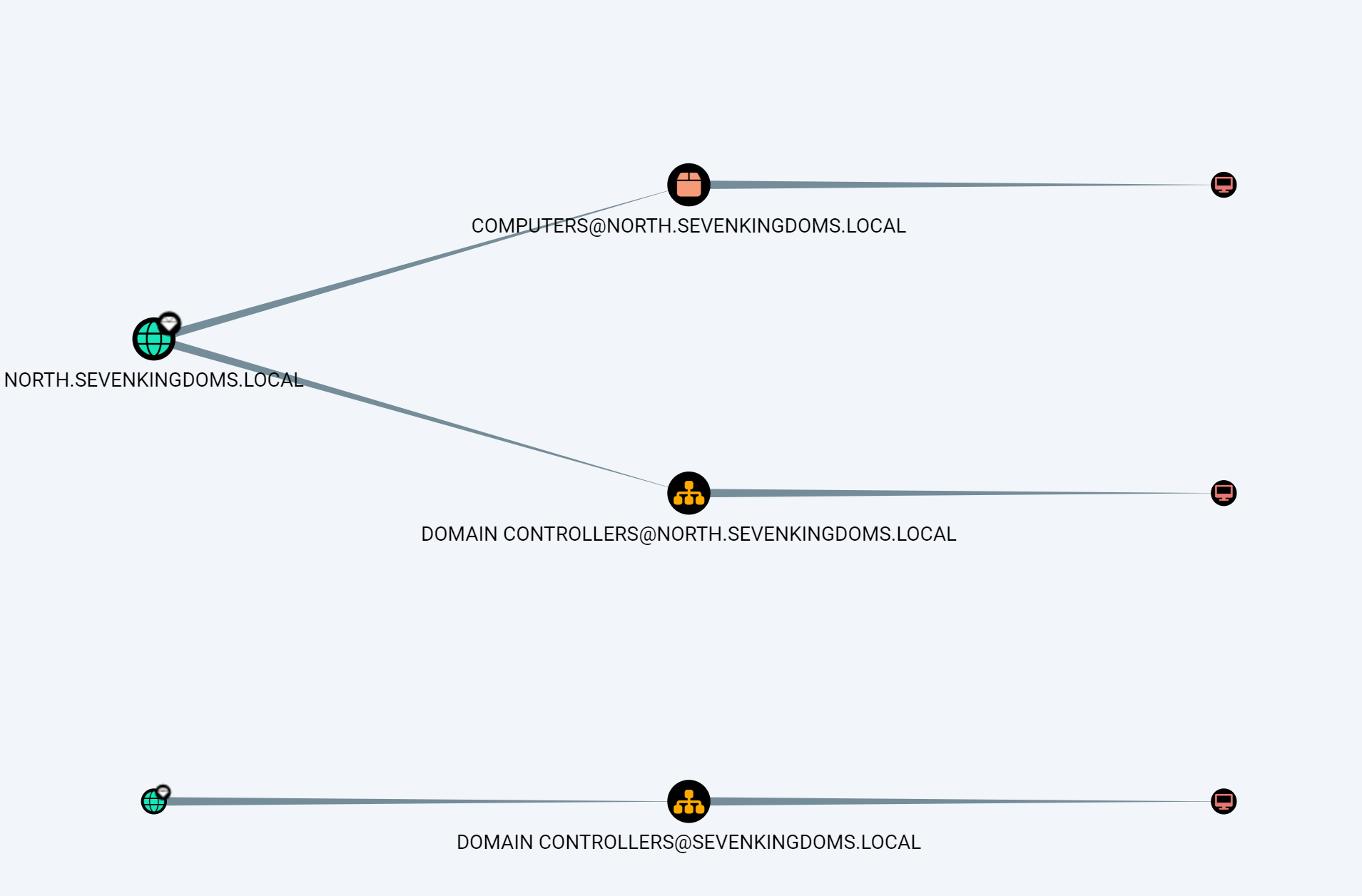
显示所有的域和主机
1 | |
显示所有用户
1 | |
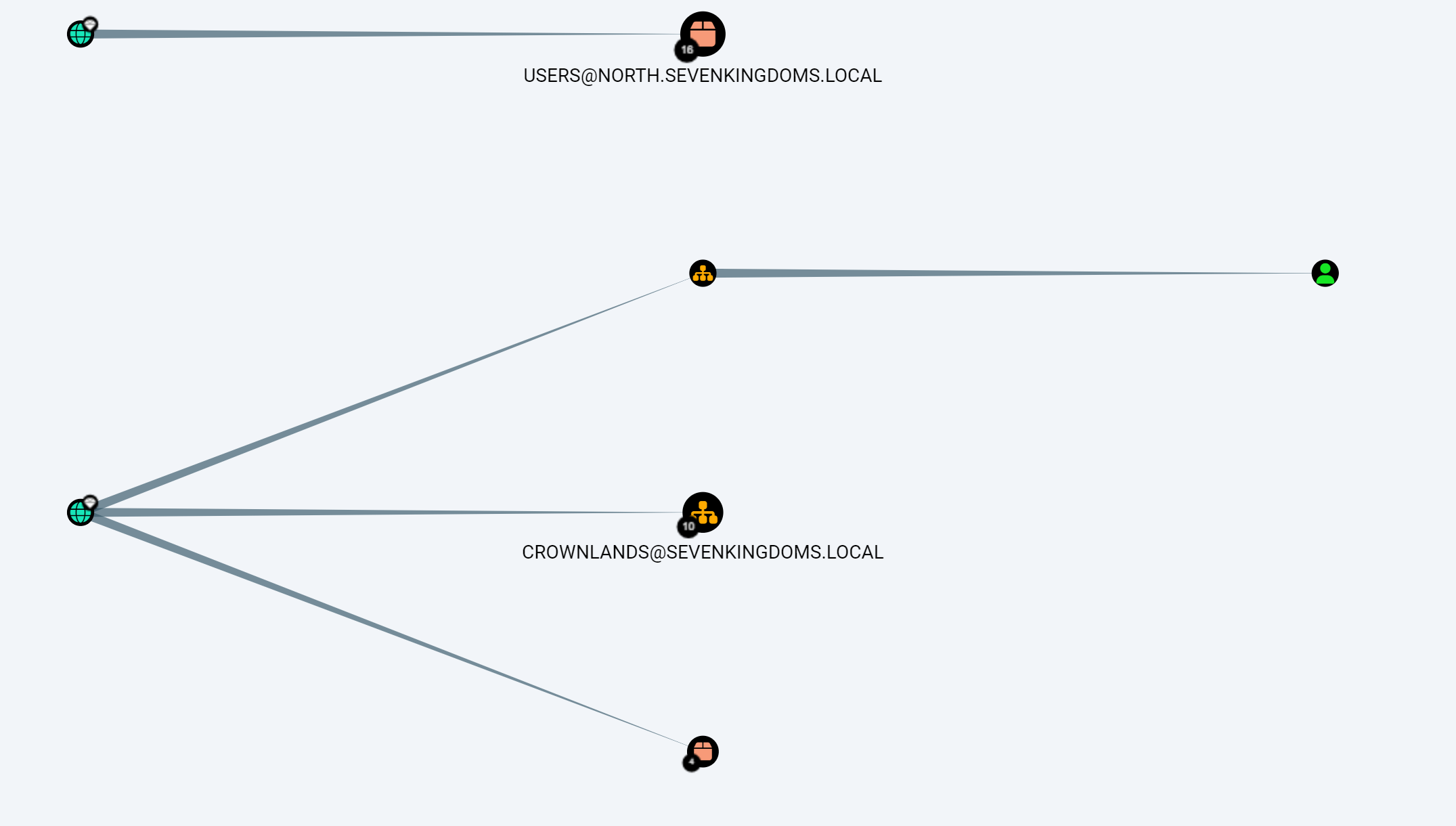
domain/group/user之间的映射
1 | |
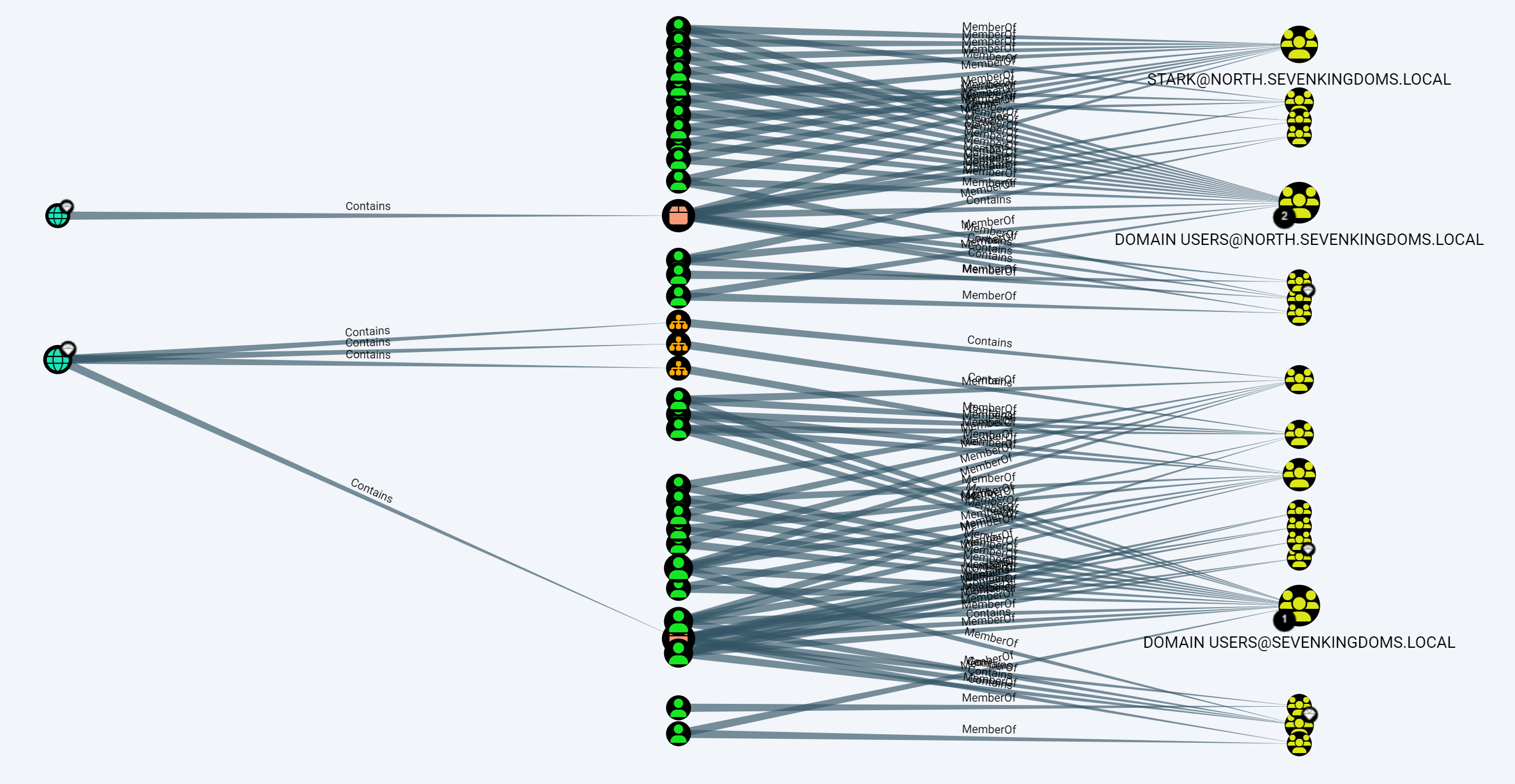
用户ACL
1 | |
